Large-scale malvertising campaigns have pushed more than a billion malicious ads through online ad networks onto "secure" web browsers. Ad-blocking software fails to stem the tide
In case you were wondering - yes, you're right: October's official designation still is Cybersecurity Awareness Month. For bystanders, web publishers, and the victims of malicious ads, though, it turned into unofficial "Malvertising Awareness Month" rather quickly.
That's because news broke that cyber criminals had hit major browsers (Chromium/Chrome, Safari, Opera, Edge) with a broadscale malvertising campaign. Dubbed eGobbler by threat hunters, it generated more than a billion malicious advertising ad impressions over the past months.
The not-so-secret sauce of malvertising campaigns is that they piggyback on legitimate online advertising networks and popular websites to push malware, such as ransomware exploit kits, onto millions of unsuspecting targets at once.
The malicious code then gets downloaded and executed by the web browser on the victim's computer. Game over.
In 2015/2016, for example, malvertisements on the web pages of The New York Times, BBC, and MSN spread the Angler ransomware exploit kit to millions of site visitors.
Source: Talos Threat Spotlight: Malvertising
The criminals behind malvertising campaigns know that companies rarely block major media websites in their secure web gateways and content filters. Distributing malware-laced ads through trusted web destinations ensures a broader reach and top infection rates, especially when malvertising campaigns breach the IT perimeters of corporate networks.
Not all malvertising campaigns require actual clicking on the malicious ad. Some drop their hidden payload onto the site visitor's computer without the user's intervention.
Still, they all rely on a locally installed browser to bring home the bacon. That's because today's "free" browsers were designed first and foremost with advertisers and marketers in mind, instead of security and privacy for web users.
To put it more plainly: Without the "free" browser, malvertising would be a non-issue.
So why exactly do malicious ads need the conventional web browser to hit their mark? Because regular browsers, although often labeled "secure", suffer from inherent security flaws and vulnerabilities.
One could even argue that the proliferation of locally installed browsers has created the malvertising phenomenon in the first place, and continues to serve as an incentive.
The business model of malvertizers depends on locally installed browsers. So do ransomware and other malware and spyware campaigns. This has primarily two reasons:
Decentrally installed and managed, regular browsers are notoriously difficult to& update, patch, secure, and monitor. Firewalls, AV tools, and content filters haven't stopped malvertising campaigns.
Nor have rigid web use policies. Ad blockers may be more effective in defending against malvertising - until they are not (read on for an example below), or are themselves malware in disguise.
It only takes one malware-dropping ad impression on an employee's PC to infect the entire corporate network with ransomware. Consider these recent malvertising exploits:
The eGobbler campaign was first investigated and reported by security software vendor Confiant. The company frequently publishes details and code samples of exploits affecting programmatic advertising on its blog.
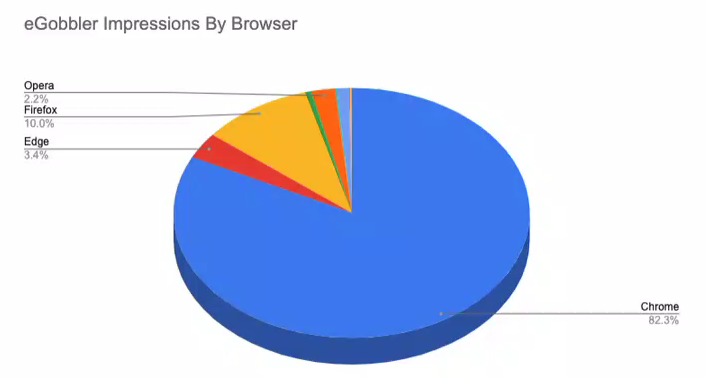
Source: Confiant Blog
The sophistication and impact of eGobbler, as well as the increasing impact of malvertising in general, alarmed not only security professionals. Publishers and the online advertising industry are also increasingly worried.
eGobbler provided more proof that isolating web ads in a software-defined "sandbox" locally, essentially segregating them from other processes running in the browser, isn't working.
"Shockingly," the Confiant researchers reported, "we found that even when the sandbox parameters were present, a pop-up would be spawned when the user tapped on the parent page." Ouch.

Source: Breaking and Evading the Local
Browser Sandbox - Authentic8 Blog
There goes another defense that the advertising industry and browser makers had hoped would provide a bulwark against malicious ads. If you read Amir Mohammadi's two-part post Breaking and Evading the Local Browser Sandbox on our blog, you already know: this hope was misplaced from the beginning.
eGobbler is just the latest incident in a string of malvertising "success stories" that have turned world-renowned media sites (and ad-heavy adult entertainment portals) into Reliable Sources - for Ransomware Infections.
2019 malvertising incidents have increased the pressure on ad networks and publishers. They are increasingly concerned about ad-blocking browser plugins cutting further into their ad revenues and about the growing reputation damage caused by malvertising.
The problem for publishers is that while malvertising primarily targets the local browser and its inherent vulnerabilities, most victims, once they find out they've been hit, don't care much about the finer points and technicalities.
Instead, they blame the perceived sources of the attack: site publishers and advertising networks. The fallout is manifest in headlines like "Forbes website spread malware attack via poisoned ads" - even if the publishers initially were as clueless to an attack as the victims.
Needed: a solution that is more than a quick fix. eGobbler serves as a reminder that merely propping up the same "secure" and "free" browsers that spawned the problem in the first place will only prolong the agony.
"The more prevalent that malvertising attacks become," wrote Nicole Lindsey in CPO Magazine back in March, "the more likely that there will be negative repercussions for ad networks, ad tech companies, and national advertisers."
Will malvertising break online advertising as we know it? Not necessarily. Publishers can have their piece of the online advertising cake and eat it, too - without continuing to expose their audiences to malvertising exploits.
Paradoxically, their dilemma can be solved by disconnecting their audiences from the web.
Sounds whacky? You may be surprised to learn that this approach is already working, and malvertising is just one of the many web-related problems it has solved for commercial and public organizations.
How to eliminate web-borne threats when employees use the web? How to protect them where AV tools and URL filters fail? For a growing number of organizations in the commercial and public sectors, the answer is web isolation.
Banking and financial services,"Big Law" firms, defense contractors, tech companies, and government agencies have switched from a reactive to a proactive IT security model for their employee's web activities by deploying Silo Cloud Browser, developed by Authentic8.
Silo isolates all web-borne code offsite, in a secure cloud container on Authentic8's server. (For more details, check the FAQ below.) Remote browser isolation with Silo ensures that no web-borne code can touch the local computer or mobile device.
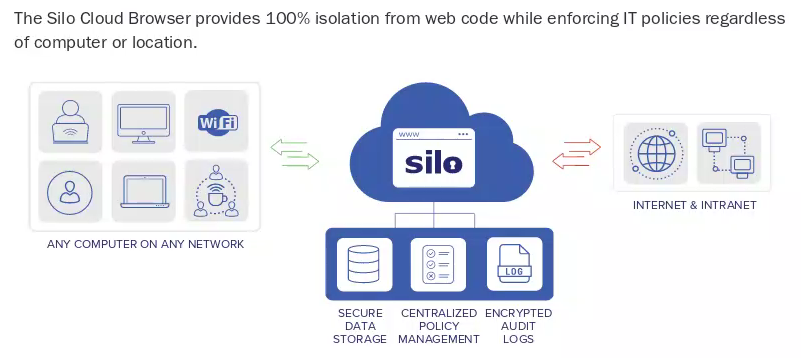
This additional layer of security for web users has been compared to the air gap that protects the IT of submarines and nuclear power plants from the public internet.
After banks, lawyers, and law enforcement, will online publishers be next to leverage web isolation?
With remote browsing and web isolation, they could prevent more revenue and reputation losses by simply locking malvertising out cold. Their audiences don't even have to be part of a tightly regulated or particularly security-sensitive organization to use Silo Cloud Browser.
All site visitors need is to be able to access cloud browsing as-a-service that enables them to access the online publisher's content risk-free - including ads. No browser download required.
Find out for yourself how it works - just click the Launch button on this page:

A: AV tools provide limited and unreliable protection against malvertising exploit kits, as proven by malicious ad campaigns such as eGobbler.
Most antivirus tools rely on heuristic, database-driven methods to detect malicious software. This approach is rendered useless by most malvertising campaigns because they typically leverage polymorphic malware and zero-day exploits. This enables malicious ads to bypass the safeguards of traditional AV programs.
A: While ad blockers can provide limited protection against malvertising, they are also known to introduce additional security and privacy risks on the local browser. Security experts find them far from reliable.
One recent example is the attack against Windows 10 users in Germany. Although many had ad-blocking add-ons installed in their browser, they were still subjected to a malicious ad campaign on the Microsoft Advertising network, reported Bleeping Computer.
The victims suddenly found themselves buried in an avalanche of tech support scam alerts, sweepstakes, and fraudulent gambling pages popping up in their default browser. They can blame the tight integration of regular web browsers with the local operating system.
Because the malvertisements were activated through MS News, MS Jigsaw, and other MS Advertising-supported apps, the browser's ad blocking extensions never stood in the way of the function calls invoking the malicious pages.
A: On the most basic level, keeping your installed browser base and ad-blocking software updated and patched helps (and still often doesn't happen).
Also, avoid browser plugins that are known to be particularly vulnerable to malvertising and other malware exploits (infamous examples: Adobe Flash, Acrobat Reader).
While these are necessary steps, they can only provide limited protection. To prevent all potentially malicious web code from touching the endpoint, without exception, you need web isolation as provided by Silo Cloud Browser.
Based on the Zero Trust approach to IT security, Silo's security model assumes that all web content, including from legitimate resources, should be treated as untrusted until proven otherwise and handled outside the web user's IT perimeter, i.e., not on the local machine.
Silo makes it possible to hermetically insulate the site visitor's computer and network from the web and its inherent risks, such as malvertising. As a cloud browser, it doesn't download and process web pages, scripts, files or "cookies" on the local computer.
Instead, Silo Cloud Browser transmits only visual display information (pixels) back to the endpoint over an encrypted connection. On their devices, Silo customers enjoy the same rich web experience they are used to - without any of the risks associated with local browsers.
A: We sometimes get asked if Silo provides "traditional" ad-blocking functionality, for example to screen out ads even visually.
By default, our cloud browser uses Adblock Plus to limit access to ads when browsing web pages.
This has both readability and security reasons. For one thing, it reduces visual distractions through annoying pop-ups and display ads.
For another, it creates an additional level of protection. Yes, web isolation with Silo prevents any malvertising payloads (all web code for that matter, good or bad) from getting through. And no, it cannot prevent a gullible web user from picking up the phone and calling 1-800-SCAMMER.
This leaves fraudulent ad campaigns that rely on the "human factor" instead of code to worry about. Take spray-and-pray ads for tech support scams, for example. They often don't push malware, at least not initially.
Instead, scammers often rely at this stage on visual design and psychological trickery to make the victim pick up the phone and call the "support" number on the screen: "Contact the FREE Support Hotline Now!" With the ad-blocking feature enabled, Silo customers can minimize the risk.