Stay up to date the most pressing cyber threats, emerging trends and what they mean for enterprise security, critical infrastructure and global risk.
TLP: CLEAR
EXECUTIVE SUMMARY
Intelligence analysis confirms escalating nation-state operations with Chinese actors conducting coordinated SharePoint zero-day campaigns while deploying ransomware capabilities, representing continued convergence of espionage and financial motivations.1 The simultaneous targeting of critical infrastructure through hacktivist operations has reportedly increased 150% and sophisticated supply chain attacks via compromised Salesforce instances are affecting Fortune 500 companies, including Google and Cisco.2 Most concerning is the weaponization of artificial intelligence at industrial scale, with DPRK nexus adversary FAMOUS CHOLLIMA infiltrating over 320 companies using generative AI for sustained deception operations, while critical endpoint security platforms face active zero day exploitation enabling attackers to compromise security infrastructure itself.3
The convergence of multiple high-severity attack vectors, nation-state zero-day campaigns with ransomware deployment, AI-enhanced social engineering increasingly growing in scale, and systematic targeting of security tools and cloud infrastructure, indicates coordinated escalation requiring immediate enterprise-wide defensive posture elevation across all domains simultaneously.
CRITICAL INCIDENTS
1. Chinese Nation-State SharePoint Campaign Deploys Warlock Ransomware
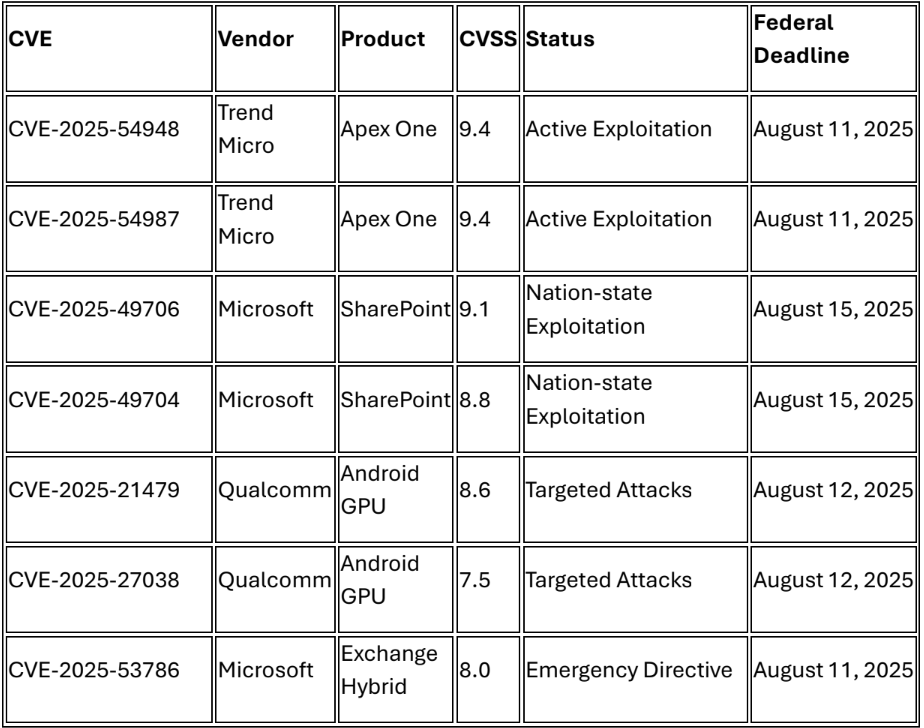
CISA confirms active exploitation of CVE-2025-49706 (spoofing) and CVE-2025-49704 (remote code execution) targeting on-premises SharePoint servers by Chinese nation-state actors Linen Typhoon, Violet Typhoon, and Storm-2603.4 Storm-2603 deploys Warlock ransomware in post-exploitation activities, with patch bypass vulnerabilities CVE-2025- 53770 and CVE-2025-53771 added to CISA KEV catalog.5 Campaign impacts only on premises SharePoint installations with specific indicators of compromise including IP addresses 107.191.58[.]76, 104.238.159[.]149, and 96.9.125[.]147.6
Analyst Comment: The deployment of ransomware by nation-state actors represents tactical evolution blurring traditional boundaries between espionage and financially motivated attacks, indicating potential resource diversification strategies.
2. Trend Micro Apex One Zero-Days Compromise Security Infrastructure
Trend Micro confirms active exploitation of critical command injection vulnerabilities CVE 2025-54948 and CVE-2025-54987 in Apex One on-premise Management Console with CVSS 9.4 severity score.7 Attack vector enables unauthenticated remote code execution requiring only network access to management console, providing system-level access to endpoint security infrastructure across enterprise networks.8 Temporary mitigation tool FixTool_Aug2025 released with critical patch expected mid-August 2025.9
Analyst Comment: Compromise of endpoint security management platforms creates cascading risks by providing attackers comprehensive visibility into detection capabilities and potential control over enterprise-wide security enforcement mechanisms.
3. ShinyHunters Execute Mass-Scale Salesforce Data Extortion Campaign
Cybercrime collective ShinyHunters executed sophisticated vishing attacks against major corporations including Google, Cisco, Chanel, and Pandora using voice phishing to authorize malicious OAuth applications enabling mass data exfiltration.10Campaign tracked by Google as UNC6040 uses fake Data Loader applications named "My Ticket Portal" to access corporate Salesforce instances.11 Google breach disclosed August 5, 2025, with threat actors preparing data leak site for increased extortion pressure against additional Fortune 500 victims.12
Analyst Comment: The systematic success of OAuth-based social engineering demonstrates fundamental vulnerabilities in cloud service authorization workflows that transcend technical controls and require enhanced human verification procedures.
4. ECScape Attack Technique Exposes AWS ECS Credential Theft
Security researchers unveiled ECScape technique at Black Hat USA 2025 demonstrating how low-privileged ECS tasks can hijack IAM credentials of higher-privileged containers on same EC2 instance.13 Attack exploits undocumented ECS internal protocol to abuse agent communication service and harvest credentials for all running tasks.14 Amazon acknowledged issue and updated documentation clarifying task isolation limitations on EC2 instances affecting containerized cloud environments globally with shared infrastructure deployments.15
Analyst Comment: This vulnerability exposes fundamental architectural assumptions about container isolation in shared cloud infrastructure, requiring immediate review of deployment models and migration to isolated compute environments where possible.
5. Interlock Ransomware Surge Targets Healthcare Critical Infrastructure
Joint advisory from CISA, FBI, HHS, and MS-ISAC warns of increasing Interlock ransomware activity specifically targeting healthcare sector using double extortion tactics—encrypting data while stealing it—threatening operational continuity and patient privacy.16 Campaign demonstrates sophisticated targeting of healthcare organizations across North America and Europe since September 2024, with escalating activity documented through August 2025.17 Healthcare sector represents high-value target due to operational urgency and sensitive data value.18
Analyst Comment: Healthcare-specific ransomware targeting exploits sector vulnerabilities including operational urgency, patient safety considerations, and regulatory compliance requirements that increase likelihood of ransom payment.
6. Android Devices Face Active Qualcomm GPU Exploitation
Google Threat Analysis Group confirmed "limited, targeted exploitation" of critical Qualcomm vulnerabilities CVE-2025-21479 (CVSS 8.6) and CVE-2025-27038 (CVSS 7.5) affecting Adreno GPU frameworks in Android devices.19 CISA added both vulnerabilities to KEV catalog June 3, 2025, with patches released in Android August 2025 security bulletin addressing graphics framework incorrect authorization and use-after-free vulnerabilities.20 Exploitation enables unauthorized command execution and potential device compromise across millions of Android devices globally.21
Analyst Comment: Mobile platform targeting through GPU vulnerabilities represents sophisticated attack vector requiring advanced technical capabilities and indicates high value targeting of specific individuals or organizations.
ACTIVE THREAT ACTORS
FAMOUS CHOLLIMA (DPRK-nexus)
North Korean state-sponsored group demonstrates unprecedented AI weaponization capabilities, infiltrating over 320 companies in the last 12 months—a 220% year-over-year increase—using generative AI at every stage of hiring and employment processes.22 IT workers use GenAI to create attractive resumes, deploy real-time deepfake technology to mask identities in video interviews, and employ AI code tools to perform job functions.23 Campaign represents first confirmed large-scale use of AI for sustained insider threat operations, with adversaries using AI to automate tasks requiring advanced expertise.24
Secret Blizzard (Russian State Hackers)
Russian state hackers conducted sophisticated cyberespionage campaign targeting embassies in Moscow using ApolloShadow malware to manipulate system certificates and disguise activities as trusted applications.25 Campaign demonstrates advanced tradecraft focused on diplomatic intelligence collection through sophisticated certificate manipulation and application masquerading techniques.26 Operations indicate continued Russian intelligence focus on diplomatic targets and foreign mission monitoring capabilities.27
UAC-0099 (Pro-Russian Threat Actor)
CERT-UA warned of cyberattacks by threat actor UAC-0099 targeting Ukrainian government agencies and defense forces using phishing emails with court summons lures to deliver MATCHBOIL, MATCHWOK, and DRAGSTARE malware families.28Campaign demonstrates sophisticated targeting of Ukrainian critical infrastructure and government operations with custom malware toolkit designed for persistent access and intelligence collection.29 Operations indicate continued Russian-aligned targeting of Ukrainian governmental and military capabilities.30
Silver Fox APT (Chinese State-Sponsored)
Chinese espionage group demonstrates dual-use capabilities conducting both intelligence collection and financially motivated attacks against primarily Chinese-speaking targets.31 Campaign deploys trojanized medical software including Philips DICOM viewers to deliver ValleyRAT/Winos 4.0 backdoors, keyloggers, and cryptocurrency miners.32 Attacks achieve persistent firmware-level compromise surviving Windows reinstallation using vulnerable TrueSight driver, targeting healthcare organizations, government sectors, and critical infrastructure across Taiwan, Japan, and Asia-Pacific region.33
UNC6040/ShinyHunters (Cybercrime Collective)
Sophisticated cybercrime operation executing coordinated vishing attacks against major technology companies to compromise Salesforce instances through OAuth application manipulation.34 Group demonstrates advanced social engineering capabilities combined with technical expertise in cloud service exploitation, targeting Fortune 500 companies for data theft and extortion operations.35 Campaign indicates evolution of cybercrime operations toward sophisticated supply chain targeting through trusted cloud services.36
TRENDS
Artificial Intelligence Weaponization Reaches Industrial Scale
Analysis confirms adversaries weaponizing AI at unprecedented scale with multiple threat actors exploiting vulnerabilities in AI software for initial access while using AI tools to enhance attack capabilities.37 Lower-skilled adversaries increasingly abuse AI to automate tasks requiring advanced expertise, with malware families Funklocker and SparkCat demonstrating emergence of GenAI-built malware.38 CrowdStrike observed AI expansion of enterprise attack surfaces through targeting of AI development platforms and model repositories, fundamentally altering threat landscape complexity and detection requirements.39
Analyst Comment: The democratization of advanced attack capabilities through AI tools accelerates threat evolution exponentially and demands immediate investment in defensive AI applications, enhanced detection capabilities, and AI-aware security architectures.
Ransomware Operations Achieve 20 Daily Attacks with 46% Zero-Day Increase
Intelligence indicates ransomware attacks averaging 20 per day throughout 2025 with 46% increase in zero-day exploitation representing industrial-scale criminal operations.40 Analysis shows 57% of 2024 ransomware attacks targeted United States, with critical manufacturing facilities representing 20% of attacks against critical infrastructure.41 Multiple ransomware families demonstrate sophistication including Gunra built on leaked Conti codebase, Chaos with possible Royal/BlackSuit links, and DeadLock demanding Bitcoin/Monero payments through Session messenger.42
Analyst Comment: Sustained daily attack tempo combined with increased zero-day usage indicates ransomware operations have achieved industrial-scale capabilities with sophisticated supply chains requiring proportional defensive investments and coordinated response mechanisms.
Critical Infrastructure Faces Coordinated Multi-Vector Targeting
Hacktivist groups conducted 64 industrial control system attacks in Q2 2025 representing 150% increase, with Z-Pentest responsible for 38 attacks and Dark Engine for 26 incidents.43 Energy & Utilities sector represents primary target with additional focus on Manufacturing, Transportation, and Telecommunications, with Italy most frequently targeted followed by United States, Czech Republic, France, and Spain.44 Coordinated Russian-linked groups demonstrate deliberate collaboration supporting strategic objectives while UNC3886 maintains persistent access across multiple critical infrastructure sectors through zero-day exploitation of Fortinet, VMware, and Juniper systems.45
Analyst Comment: Convergence of hacktivist operations, nation-state campaigns, and criminal ransomware targeting critical infrastructure indicates coordinated escalation requiring enhanced defensive cooperation between public and private sector stakeholders and international partners.
Cloud Service Supply Chain Exploitation Scales Through OAuth Manipulation
VexTrio cybercrime network operates through seemingly legitimate advertising technology companies spanning nearly 100 companies across adtech, mobile apps, energy, construction, and hospitality sectors, with Los Pollos claiming 200,000 affiliates and over 2 billion unique users monthly.46 Microsoft OAuth impersonation campaigns targeted nearly 3,000 account compromises across 900 Microsoft 365 environments in 2025, while sophisticated vishing operations successfully compromise major cloud service providers through employee manipulation.47 Attack methodology enables threat actors to scale operations through trusted third-party relationships rather than individual target compromise.48
Analyst Comment: Supply chain attacks through cloud services represent force multipliers enabling threat actors to achieve broad impact through compromise of shared infrastructure and trusted vendor relationships, requiring enhanced third-party risk management and cloud service authorization procedures.
VULNERABILITIES
Critical Patches Required This Week
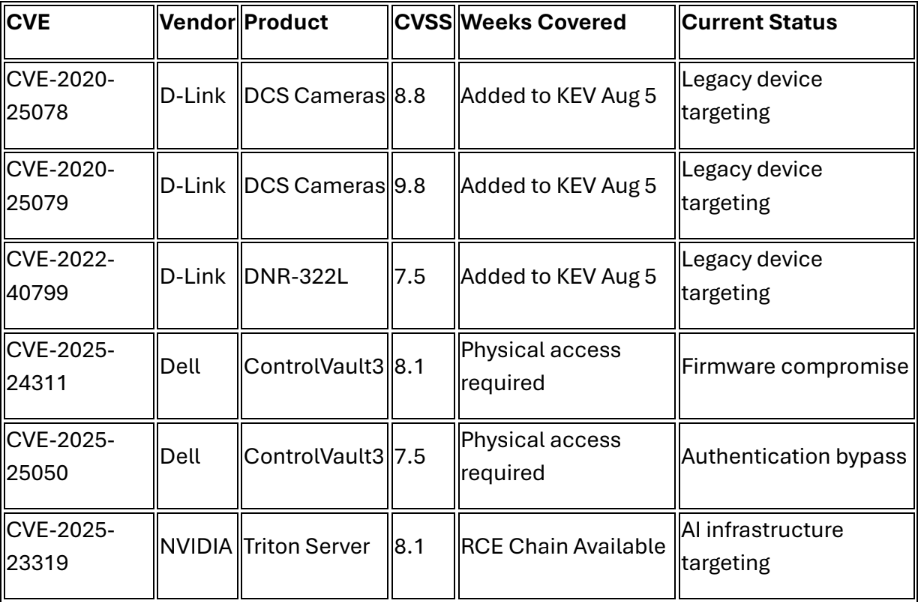
Continuing Active Exploitation
RECOMMENDATIONS
Immediate Actions (0-24 Hours)
- Apply Trend Micro FixTool_Aug2025 to all Apex One on-premise installations immediately and restrict external network access to management consoles49
- Patch Microsoft SharePoint on-premises servers using April 2025 Exchange Server Hotfix Updates and monitor for specific IOCs provided by CISA50
- Deploy Android August 2025 security patches across mobile device fleet to address actively exploited Qualcomm Adreno GPU vulnerabilities51
- Implement Microsoft Exchange Server hybrid mitigations per CISA EmergencyDirective ED 25-02 and deploy dedicated Exchange hybrid application52
- Conduct immediate audit of Salesforce instances for unauthorized OAuth applications and implement additional MFA requirements for cloud service authorizations53
- Cybersecurity and Infrastructure Security Agency. (2025, July 22). UPDATE: Microsoft releases guidance on exploitation of SharePoint vulnerabilities. https://www.cisa.gov/news-events/alerts/2025/07/20/update-microsoft-releases-guidance-exploitation-sharepoint-vulnerabilities
- Whittaker, Z. (2025, August 6). Google says hackers stole its customers' data by breaching its Salesforce database. TechCrunch. https://techcrunch.com/2025/08/06/google-says-hackers-stole-its-customers-data-in-a-breach-of-its-salesforce-database/
- CrowdStrike. (2025, August 4). CrowdStrike 2025 threat hunting report: AI becomes a weapon and target. CrowdStrike Blog. https://www.crowdstrike.com/en-us/blog/crowdstrike-2025-threat-hunting-report-ai-weapon-target/
- Cybersecurity and Infrastructure Security Agency. (2025, July 22). UPDATE: Microsoft releases guidance on exploitation of SharePoint vulnerabilities. https://www.cisa.gov/news-events/alerts/2025/07/20/update-microsoft-releases-guidance-exploitation-sharepoint-vulnerabilities
- Microsoft Security. (2025, July 23). Disrupting active exploitation of on-premises SharePoint vulnerabilities. Microsoft Security Blog. https://www.microsoft.com/en-us/security/blog/2025/07/22/disrupting-active-exploitation-of-on-premises-sharepoint-vulnerabilities/
- Cybersecurity and Infrastructure Security Agency. (2025, July 22). UPDATE: Microsoft releases guidance on exploitation of SharePoint vulnerabilities. https://www.cisa.gov/news-events/alerts/2025/07/20/update-microsoft-releases-guidance-exploitation-sharepoint-vulnerabilities
- Trend Micro. (2025, August 6). ITW critical security bulletin: Trend Micro Apex OneTM (on-premise) management console command injection RCE vulnerabilities. Trend Micro Success Portal. https://success.trendmicro.com/en-US/solution/KA-0020652
- Zorz, Z. (2025, August 6). Trend Micro Apex One flaws exploited in the wild (CVE-2025-54948, CVE-2025-54987). Help Net Security. https://www.helpnetsecurity.com/2025/08/06/trend-micro-apex-one-flaws-exploted-in-the-wild-cve-2025-54948-cve-2025-54987/
- Trend Micro confirms active exploitation of critical Apex One flaws in on-premise systems. (2025, August 7). The Hacker News. https://thehackernews.com/2025/08/trend-micro-confirms-active.html
- Abrams, L. (2025, August 6). Google suffers data breach in ongoing Salesforce data theft attacks. BleepingComputer. https://www.bleepingcomputer.com/news/security/google-suffers-data-breach-in-ongoing-salesforce-data-theft-attacks/
- Lakshmanan, R. (2025, June 4). Google exposes vishing group UNC6040 targeting Salesforce with fake data loader app. The Hacker News. https://thehackernews.com/2025/06/google-exposes-vishing-group-unc6040.html
- Kovacs, E. (2025, August 5). Google discloses data breach via Salesforce hack. SecurityWeek. https://www.securityweek.com/google-discloses-salesforce-hack/
- Researchers Uncover ECScape Flaw in Amazon ECS Enabling Cross-Task Credential Theft. (2025, August 6). The Hacker News. https://thehackernews.com/2025/08/researchers-uncover-ecscape-flaw-in.html
- Researchers Uncover ECScape Flaw in Amazon ECS Enabling Cross-Task Credential Theft. (2025, August 6). The Hacker News. https://thehackernews.com/2025/08/researchers-uncover-ecscape-flaw-in.html
- Neerajlovecyber. (2025, August). ECScape Flaw in Amazon ECS Allows Credential Theft. https://neerajlovecyber.com/news/ecscape-flaw-amazon-ecs-credential-theft
- Cybersecurity and Infrastructure Security Agency. (2025, July 22). #StopRansomware: Interlock. https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-203a
- TATA Communications. (2025, August 5). Your weekly threat intelligence advisory. TATA Communications. https://www.tatacommunications.com/solutions/cyber-security/threat-advisory/
- TATA Communications. (2025, August 5). Your weekly threat intelligence advisory. TATA Communications. https://www.tatacommunications.com/solutions/cyber-security/threat-advisory/
- Gatlan, S. (2025, August 5). Android gets patches for Qualcomm flaws exploited in attacks. BleepingComputer. https://www.bleepingcomputer.com/news/security/android-gets-patches-for-qualcomm-flaws-exploited-in-attacks/
- Gatlan, S. (2025, August 5). Android gets patches for Qualcomm flaws exploited in attacks. BleepingComputer. https://www.bleepingcomputer.com/news/security/android-gets-patches-for-qualcomm-flaws-exploited-in-attacks/
- Critical Android vulnerabilities patched---update as soon as you can. (2025, August 7). Malwarebytes. https://www.malwarebytes.com/blog/news/2025/08/android-critical-vulnerabilities-patched-update-as-soon-as-you-can
- CrowdStrike. (2025, August 4). CrowdStrike 2025 threat hunting report: AI becomes a weapon and target. CrowdStrike Blog. https://www.crowdstrike.com/en-us/blog/crowdstrike-2025-threat-hunting-report-ai-weapon-target/
- CrowdStrike. (2025, August 4). CrowdStrike 2025 threat hunting report: AI becomes a weapon and target. CrowdStrike Blog. https://www.crowdstrike.com/en-us/blog/crowdstrike-2025-threat-hunting-report-ai-weapon-target/
- CrowdStrike. (2025, August 4). CrowdStrike 2025 threat hunting report: AI becomes a weapon and target. CrowdStrike Blog. https://www.crowdstrike.com/en-us/blog/crowdstrike-2025-threat-hunting-report-ai-weapon-target/
- Cyware. (2025, August 1). Cyware daily threat intelligence, August 01, 2025. Cyware. https://www.cyware.com/resources/threat-briefings/daily-threat-briefing/cyware-daily-threat-intelligence-august-01-2025
- Cyware. (2025, August 1). Cyware daily threat intelligence, August 01, 2025. Cyware. https://www.cyware.com/resources/threat-briefings/daily-threat-briefing/cyware-daily-threat-intelligence-august-01-2025
- Cyware. (2025, August 1). Cyware daily threat intelligence, August 01, 2025. Cyware. https://www.cyware.com/resources/threat-briefings/daily-threat-briefing/cyware-daily-threat-intelligence-august-01-2025
- Cyware. (2025, August 1). Cyware daily threat intelligence, August 01, 2025. Cyware. https://www.cyware.com/resources/threat-briefings/daily-threat-briefing/cyware-daily-threat-intelligence-august-01-2025
- Cyware. (2025, August 1). Cyware daily threat intelligence, August 01, 2025. Cyware. https://www.cyware.com/resources/threat-briefings/daily-threat-briefing/cyware-daily-threat-intelligence-august-01-2025
- Cyware. (2025, August 1). Cyware daily threat intelligence, August 01, 2025. Cyware. https://www.cyware.com/resources/threat-briefings/daily-threat-briefing/cyware-daily-threat-intelligence-august-01-2025
- Silver Fox APT Blurs the Line of Espionage & Cybercrime. (2025, August 7). Dark Reading. https://www.darkreading.com/threat-intelligence/silver-fox-apt-espionage-cybercrime
- Picus Security. (2025, June 18). Silver Fox APT Targets Public Sector via Trojanized Medical Software. https://www.picussecurity.com/resource/blog/silver-fox-apt-targets-public-sector-via-trojanized-medical-software
- Silver Fox APT Blurs the Line of Espionage & Cybercrime. (2025, August 7). Dark Reading. https://www.darkreading.com/threat-intelligence/silver-fox-apt-espionage-cybercrime
- Abrams, L. (2025, August 6). Google suffers data breach in ongoing Salesforce data theft attacks. BleepingComputer. https://www.bleepingcomputer.com/news/security/google-suffers-data-breach-in-ongoing-salesforce-data-theft-attacks/
- Lakshmanan, R. (2025, June 4). Google exposes vishing group UNC6040 targeting Salesforce with fake data loader app. The Hacker News. https://thehackernews.com/2025/06/google-exposes-vishing-group-unc6040.html
- Kovacs, E. (2025, August 5). Google discloses data breach via Salesforce hack. SecurityWeek. https://www.securityweek.com/google-discloses-salesforce-hack/
- CrowdStrike. (2025, August 4). CrowdStrike 2025 threat hunting report: AI becomes a weapon and target. CrowdStrike Blog. https://www.crowdstrike.com/en-us/blog/crowdstrike-2025-threat-hunting-report-ai-weapon-target/
- CrowdStrike. (2025, August 4). CrowdStrike 2025 threat hunting report: AI becomes a weapon and target. CrowdStrike Blog. https://www.crowdstrike.com/en-us/blog/crowdstrike-2025-threat-hunting-report-ai-weapon-target/
- CrowdStrike. (2025, August 4). CrowdStrike 2025 threat hunting report: AI becomes a weapon and target. CrowdStrike Blog. https://www.crowdstrike.com/en-us/blog/crowdstrike-2025-threat-hunting-report-ai-weapon-target
- Help Net Security. (2025, August 6). Ransomware is up, zero-days are booming, and your IP camera might be next. https://www.helpnetsecurity.com/2025/08/06/ciso-2025-cybersecurity-threat-trends/
- MSSP Alert. (2025, February 20). Ransomware attacks on critical infrastructure, AI use to grow in 2025. https://www.msspalert.com/news/ransomware-attacks-on-critical-infrastructure-ai-use-to-grow-in-2025
- TATA Communications. (2025, August 5). Your weekly threat intelligence advisory. TATA Communications. https://www.tatacommunications.com/solutions/cyber-security/threat-advisory/
- Cyble. (2025, July). Hacktivists attacks on critical infrastructure surge in 2025. https://cyble.com/blog/hacktivists-attacks-on-critical-infrastructure/
- Cyble. (2025, July). Hacktivists attacks on critical infrastructure surge in 2025. https://cyble.com/blog/hacktivists-attacks-on-critical-infrastructure/
- TATA Communications. (2025, August 5). Your weekly threat intelligence advisory. TATA Communications. https://www.tatacommunications.com/solutions/cyber-security/threat-advisory/
- VexTrio Cybercrime Gang Run by Legit Ad Tech Firms. (2025, August 6). Dark Reading.https://www.darkreading.com/threat-intelligence/vextrio-cybercrime-outfit-legit-ad-tech
- Cyware. (2025, August 1). Cyware daily threat intelligence, August 01, 2025. Cyware. https://www.cyware.com/resources/threat-briefings/daily-threat-briefing/cyware-daily-threat-intelligence-august-01-2025
- Fake VPN and Spam Blocker Apps Tied to VexTrio Used in Ad Fraud, Subscription Scams. (2025, August 6). The Hacker News. https://thehackernews.com/2025/08/fake-vpn-and-spam-blocker-apps-tied-to.html
- Trend Micro. (2025, August 6). ITW critical security bulletin: Trend Micro Apex OneTM (on-premise) management console command injection RCE vulnerabilities. Trend Micro Success Portal. https://success.trendmicro.com/en-US/solution/KA-0020652
- Cybersecurity and Infrastructure Security Agency. (2025, July 22). UPDATE: Microsoft releases guidance on exploitation of SharePoint vulnerabilities. https://www.cisa.gov/news-events/alerts/2025/07/20/update-microsoft-releases-guidance-exploitation-sharepoint-vulnerabilities
- Gatlan, S. (2025, August 5). Android gets patches for Qualcomm flaws exploited in attacks. BleepingComputer. https://www.bleepingcomputer.com/news/security/android-gets-patches-for-qualcomm-flaws-exploited-in-attacks/
- Kumar, R. (2025, August 8). Microsoft discloses exchange server flaw enabling silent cloud access in hybrid setups. The Hacker News. https://thehackernews.com/2025/08/microsoft-discloses-exchange-server.html
- Abrams, L. (2025, August 6). Google suffers data breach in ongoing Salesforce data theft attacks. BleepingComputer. https://www.bleepingcomputer.com/news/security/google-suffers-data-breach-in-ongoing-salesforce-data-theft-attacks/


