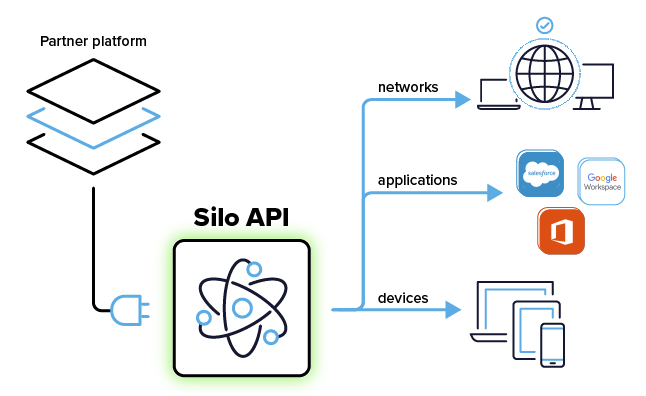
Integrate the Silo isolation API with your technology platform to address customer workflows that have been notoriously risky: application access by third parties, critical data access and employee web browsing.
The API leverages the context of your platform to erect flexible isolation perimeters around apps, data and devices. Decide which access scenarios require the isolated, cloud-based Silo environment and its built-in data transfer controls. Workflows can be transparently redirected into isolation — no disruption to the user, no software installation required.
Secure, anonymous OSINT investigations and data collection. Facilitate and automate analysts' ability to enrich threat intelligence data via the source.
Lock down access to critical web apps from anywhere, any device. Control and audit data transfer. Extend protection to contractors, suppliers and BYOD programs.
Air-gapped protection from ransomware, phishing and non-business web use. Seamlessly remove the risk of exposure from unidentified web and email links.

SSE, SWG, CASB and ZTNA partners extend zero-trust use cases to include risky web link isolation and secure app access with data control to third parties such as contractors.
SOC and threat intel teams use Silo to securely and anonymously investigate threat sources on the surface and dark web identified by the threat intel platform.
Incident response partners are offering Silo data collection automation for better event context and one-click, secure access to sources highlighted by their platforms.
Control unmanaged device access to critical applications by triggering Silo isolation and DLP policies based on context from identity management solutions.
EPP, EDR and XDR partners redirect suspicious activity identified by endpoint agents into Silo isolation with DLP policies to keep organizations secure and productive.
Extend feature sets by directing email links identified as untrusted or unknown into Silo isolation, inclusive of restricted user actions to limit data leakage.