Different priorities and communication gaps between teams threaten compliance and cybersecurity posture of financial firms, according to industry research
Different priorities and critical communication gaps between IT security teams, compliance professionals, and legal counsel are threatening the regulatory and cybersecurity posture of financial firms, according to new industry research sponsored by Authentic8.
The researchers, who examined secure web use and regulatory compliance in the financial sector, document what they call a "surprising disconnect" between the primary compliance and data protection stakeholders within leading financial firms.
The research report, titled Surprising Disconnect Over Compliance and Secure Web Use at Financial Firms, presents the results of an in-depth survey of senior decision-makers in IT, legal, and compliance roles. It was conducted by Beacon Technology Partners.
Their study analyzes the IT security and compliance impact of differing online risk perceptions within the surveyed organizations - mostly banks, investment firms, other financial service providers, and law practices that have specialized in data protection and compliance in the financial sector.
To prevent data breaches and compliance violations resulting from different priorities and a lack of communication, researchers warn, IT, compliance, and legal departments (respectively external law partners) "must restore trust and get into sync."
They base their conclusion on an in-depth survey completed by 163 respondents, including senior-level compliance officers, legal managers, and IT leaders, such as Chief Information Security Officers (CISOs).
All respondents were personally involved at the time of the survey (summer 2019) in setting policies and procedures for managing the security of IT operations, infrastructure, and regulatory compliance for their organizations.
"Financial firms have some of the best-funded IT departments of any industry, that's no secret," says Scott Petry, Co-founder and CEO of Authentic8. "What's perplexing to me, with data breaches and privacy violations at an all-time high, is how deep the divide still runs between IT, compliance, and legal professionals in many firms, according to these findings."

Among the report's key findings for compliance and IT security leaders:
The survey also discovered that "less accessible" IT departments are generally more aware of the risks involved when employees go online than those with a higher ratio of IT personnel to serve the employee population.
While this finding applies to financial companies of all sizes, including large organizations with many field offices, the increased awareness does not guarantee a stronger cybersecurity and compliance posture, the report shows.
"IT departments stretched thin seem to be more acutely aware of web-borne threats and the potential impact on their organization," says Scott Petry.
"That's the good part. Unfortunately, that awareness doesn't necessarily always translate into an effective prevention strategy, as the study shows."
Instead, some IT departments in the financial services sector have developed "tunnel vision" in identifying solutions, according to the research report.
"The results show that firms often still rely on ineffective traditional perimeter defenses and point solutions, such as anti-virus tools, URL filtering, and VPN, which in turn introduce additional risks," says Petry.
The report also quotes practitioners, independent industry observers, and analysts who were not involved with the actual research and were asked to put its results in perspective.
How do they explain the different takes by IT, legal, and compliance functions on what needs to be done to protect customer data and ensure secure and compliant web use?
"These three groups are working on the same problem, but they have different views of what the main problem is," said Michele DeStefano, a professor at the University of Miami School of Law.
One takeaway from the survey results, according to the founder of the Compliance Elliance Journal (ECJ): "Financial firms should move to a flatter organizational structure between those groups." Michele DeStefano's recommendation for firms facing this challenge: "IT should be involved in the beginning rather than at the end."
Michael Osterman agrees. The president of Osterman Research, a firm focused on the messaging, collaboration, and web industries, adds: "Compliance doesn't realize how difficult it is for IT to get things up and running. Their focus is on managing the infrastructure and dealing with user complaints."
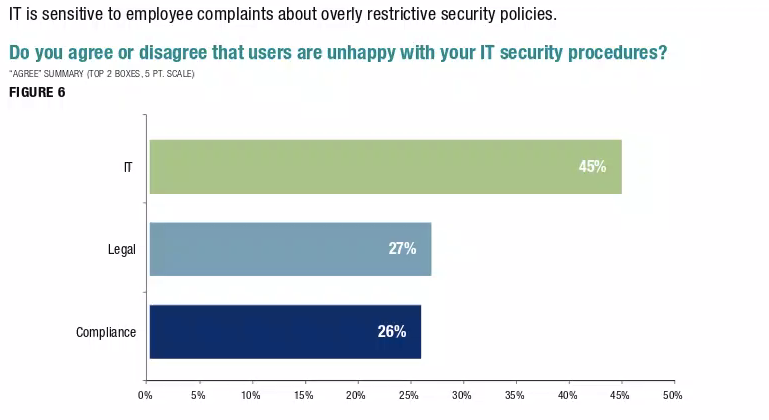
Source: Authentic8
It is mostly IT that has to deal with the push back from employees for web use policies that are often perceived as overly restrictive, the study shows.
"One of the most challenging issues for businesses in this area," comments Tom Lin, professor at Temple University's Beasley School of Law in Philadelphia, "is balancing concerns about cybersecurity caused by employees with the need to provide employees with the freedom to be autonomous, creative and productive."

So how can financial firms maximize IT security and compliance, while maintaining and improving productivity at the same time?
A significant part of the survey was geared towards identifying methods and best practices that respondents say contribute significantly to mastering this challenge.
The researchers found the following hallmarks for success:
The study also includes interviews with respondents whose firms are already using cloud-based browser isolation to protect the organization from web-borne exploits when users access the web, or to ensure anonymity and operational security for their SOC teams, analysts, or fraud investigators.
Web isolation with Silo Cloud Browser and Silo for Research is already changing how the financial services industry is conducting sensitive and compliance-relevant research, the interviews show.
The report quotes the head of fraud investigations for a global financial firm. His team uses Authentic8's Silo for Research to safely investigate sites based in foreign countries and on the dark web. "We have to make sure the identity of the analysts and the company are protected," he says.
The value that web isolation for day-to-day web use in the financial sector is highlighted by the IT director of a financial services firm who describes how Silo Cloud Browser became a core component of the firm's compliance and cybersecurity programs.
Web isolation, he says, enabled his firm to provide employees with access to the web to attend to personal matters when necessary, without sacrificing security or compliance.
Trying to bar external web access to protect the firm against exploits that target local browsers, such as ransomware, had proved untenable. "It was very painful to tell people they couldn't check their personal email on company technology," he says.
"In our industry, everyone is so busy that you have to run your personal life from the office. Browser isolation was huge for us and solved the problem."