Providing secure, audited access to third parties like contractors, suppliers, partners or part-time workers presents ongoing challenges to organizations of all sizes.
External parties handle your data using non-sanctioned and potentially compromised devices, local browsers and networks. Zero Trust Application Access extends security, streamlines management and provides visibility over third parties who access your resources.


Every company's digital ecosystem requires the exchange of sensitive data. Negotiating and enforcing security and compliance controls with your business partners is time-consuming and costly. Silo allows you to place a security and control perimeter where you previously couldn't — where you don't own or govern users, devices, networks or policies.
Your business partners are distributed across the globe. Coordinating policies and maintaining oversight across the diverse environment consumes time and resources. As a cloud-native platform, Silo covers all web scenarios across your ecosystem. From individual users in remote locations using personal devices to remote offices with groups of users.
Today’s environment has more diverse points of risk than organizations can effectively manage. Trends like mobility and cloud applications put organizations under even greater pressure. Zero Trust Application Access makes the web environment the single point of control. Networks become utility services, devices become simple displays and all the intelligence and enforcement shifts to the central Silo Web Isolation Platform.
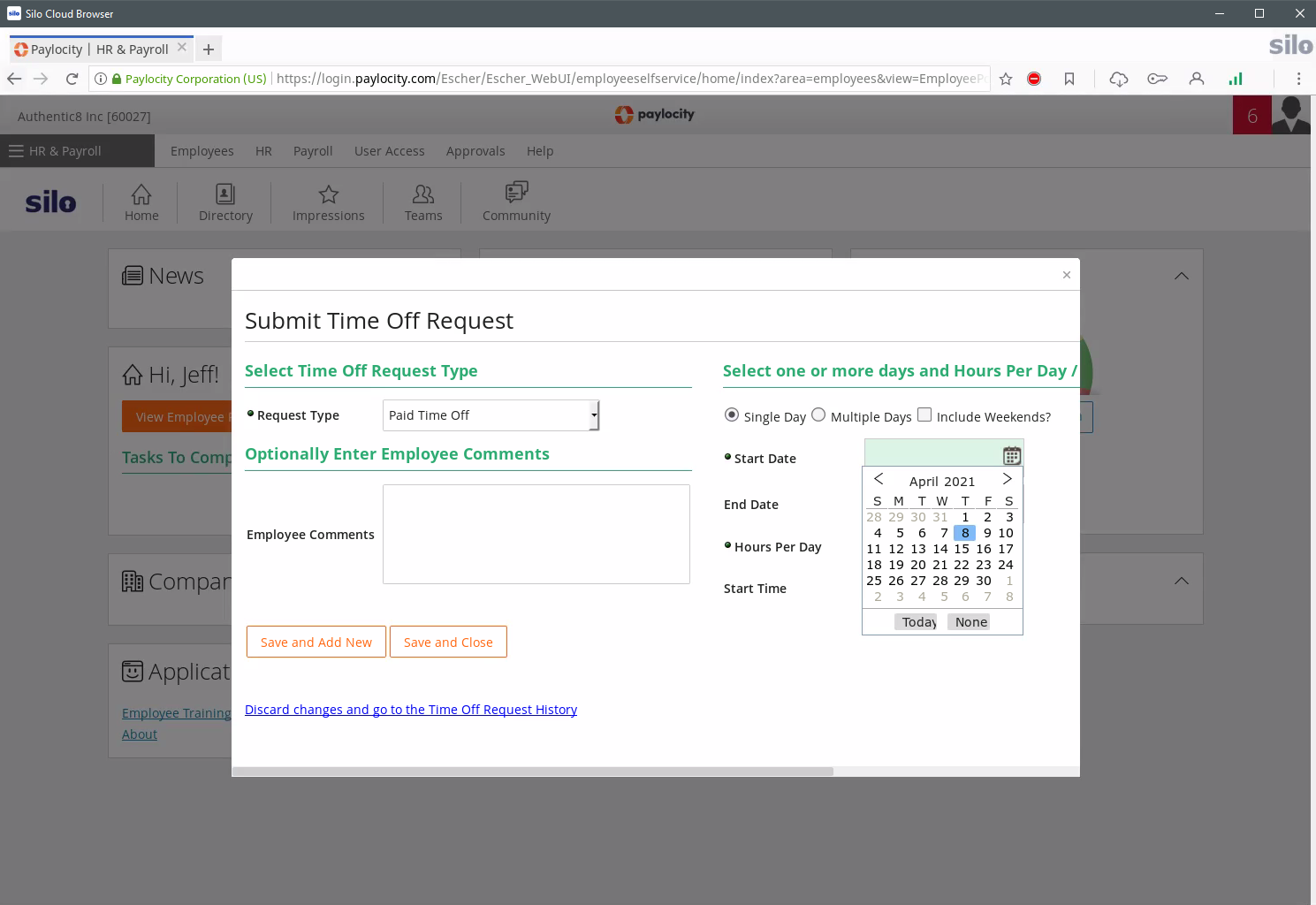
Consultants, temps, auditors, advisors — all types of third parties require access to your data in web-based applications. Zero Trust Application Access lets you define specific access and use permissions across all use cases, even when they use devices outside of your control. All policies are enforced in the browser profile, regardless of the device or the network.
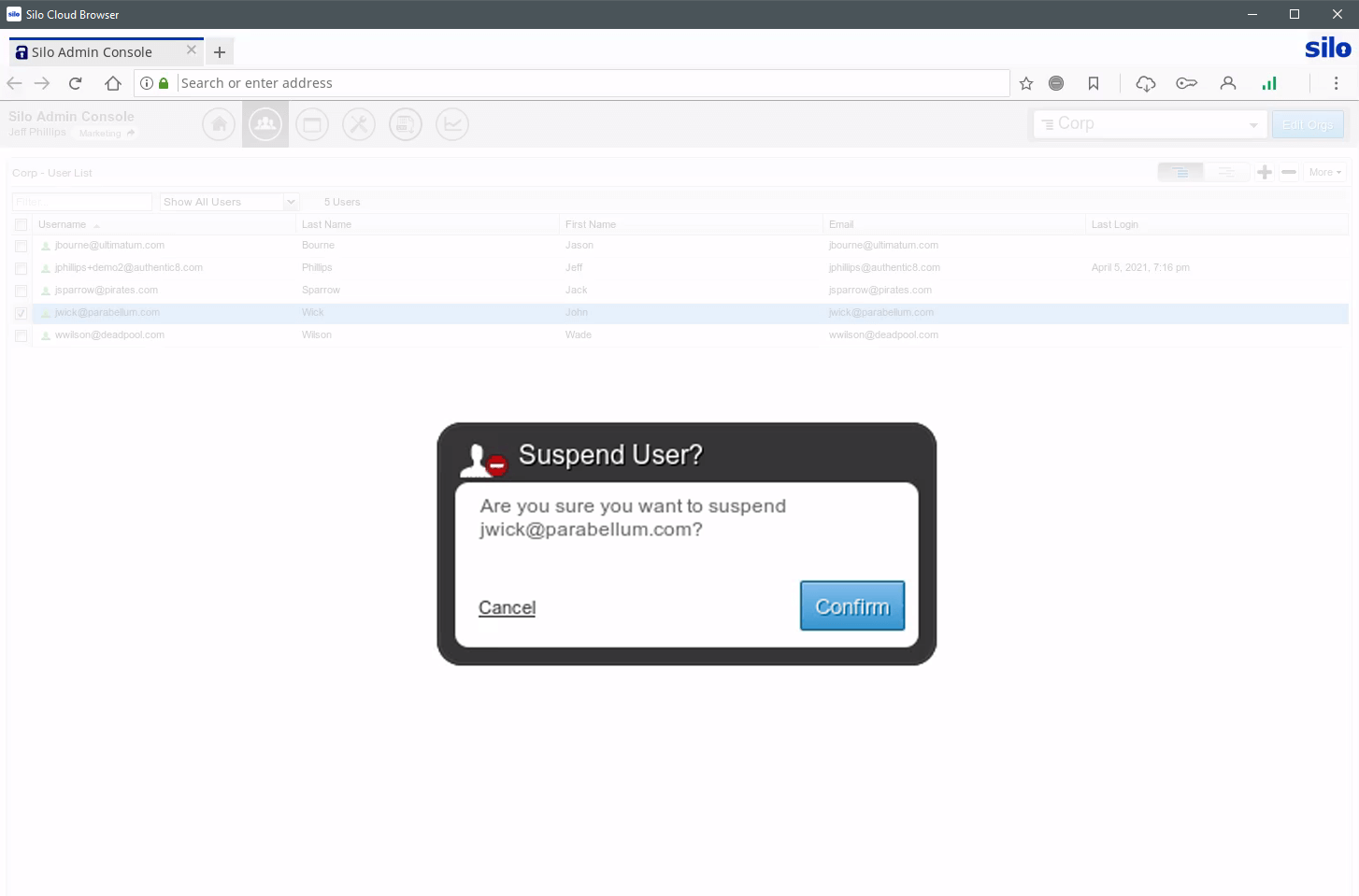
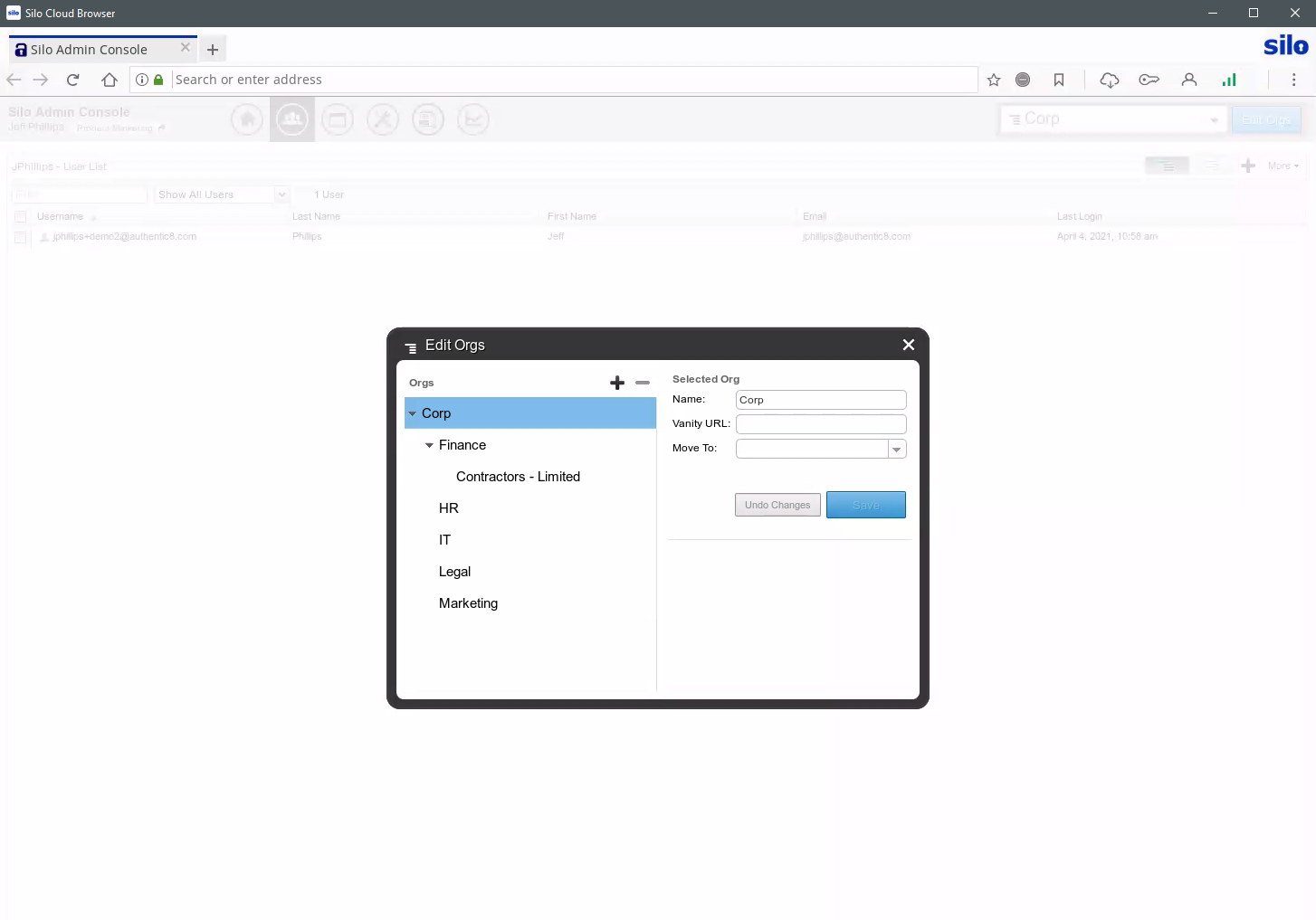
Different workflows require varying levels of access to information. With Zero Trust Application Access, access permissions for your applications and policies governing data use are managed centrally in real time. Segregate your third parties into logical management groups, and keep your controls current as individuals rotate on or off projects.
Zero Trust Application Access lets you define specific data policies across managed and unmanaged computers. For instance, authorized or trusted devices may be allowed to download or copy/paste, while a personal device can be limited to read-only access or blocked altogether.
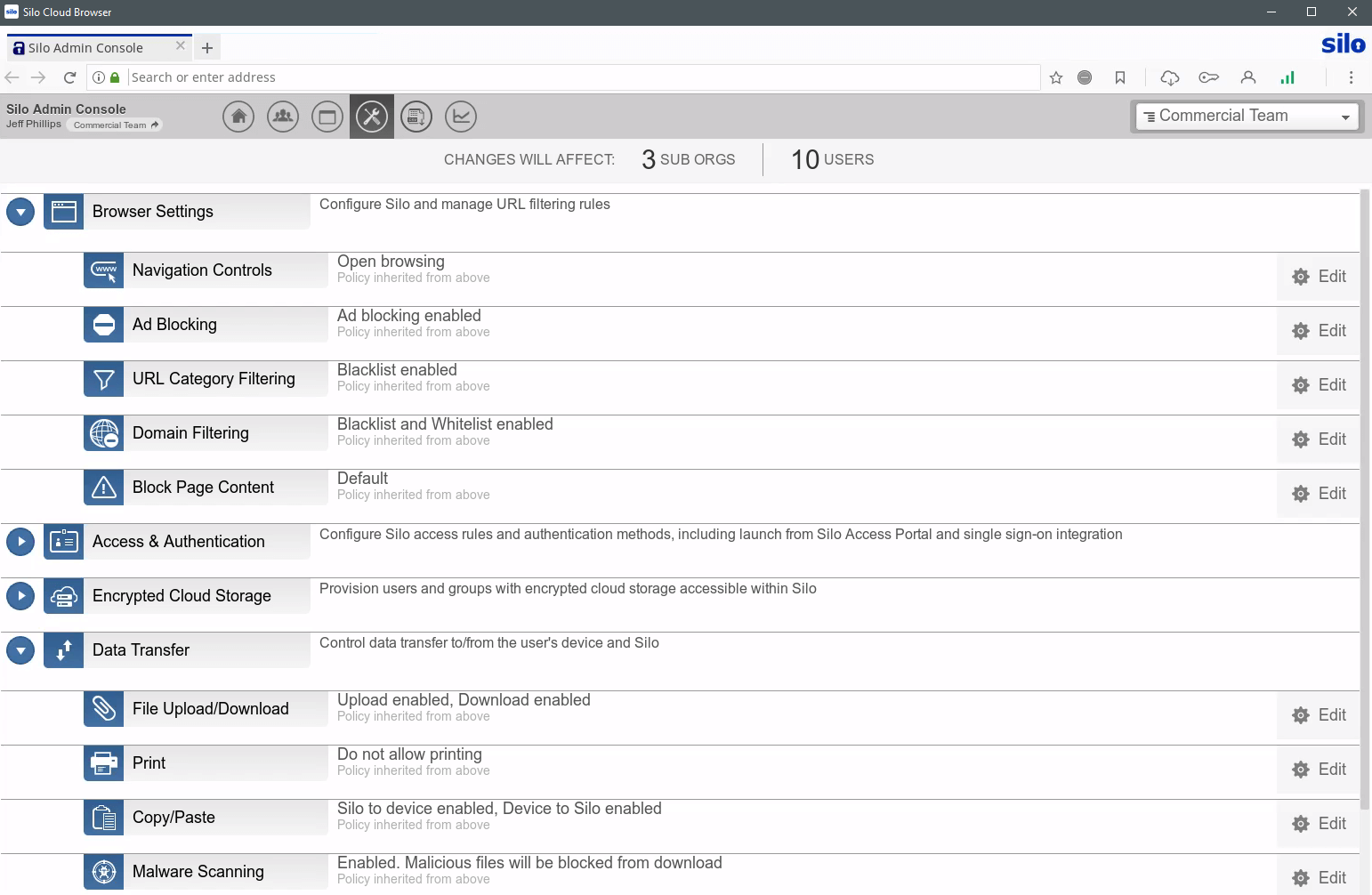
All management actions are performed in the cloud, and admins can seamlessly grant or revoke access to applications and data. Changes happen in real time, even in live sessions. Regardless of the user, location or device, Silo’s central policy framework defines control, whether you’re granting access or taking it away.
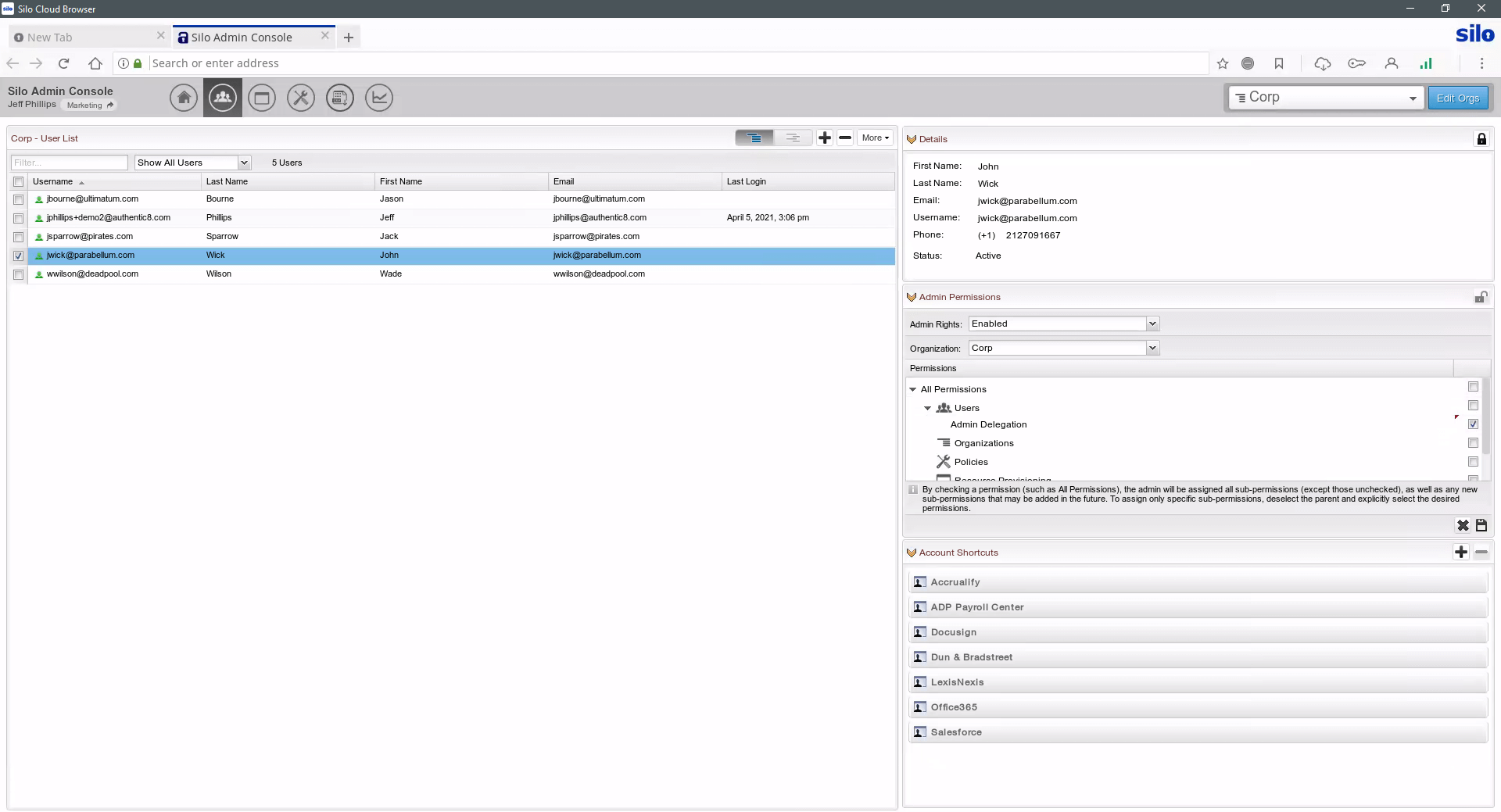
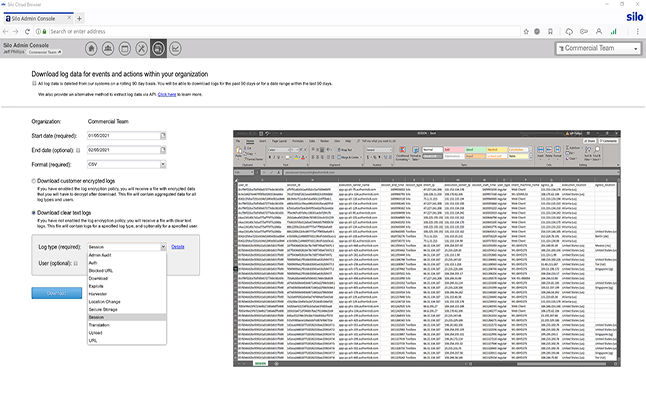
Whether comprehensive monitoring via log analysis, integrations with an orchestration platform, or spot-checking for violations, Zero Trust Application Access logs and encrypts all user and admin activity for post-factum analysis. This keeps your dynamic and mobile workforce in compliance with organizational policies.