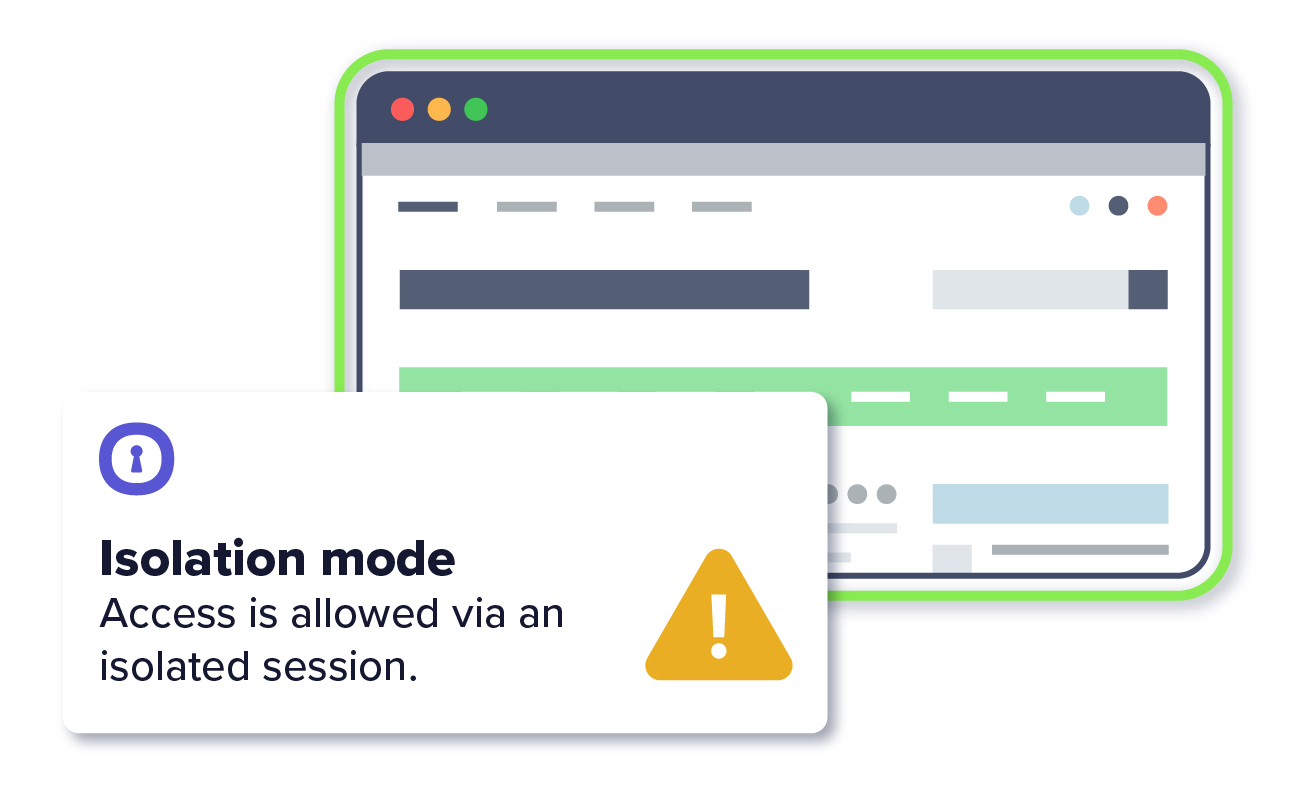
Confidently allow users to click web links without introducing risk to your organization. Direct untrusted or unknown links into a 100% isolated, cloud-based environment.

Restrict user actions to limit data leakage via policy to eliminate the risk of human error, social engineering or careless data handling. Maintain full audit and oversight ability.
Embed into existing security gateways via the Silo API and selectively isolate web links. Users work as usual. IT gets the steadfast protection they need in the browser.