Your business apps and their data are so sensitive, so critical to your organization, that you never want to expose them to potentially compromised devices and networks. But third parties like suppliers, contractors, IT help desks and others need to access them — from untrusted, unmanaged devices.
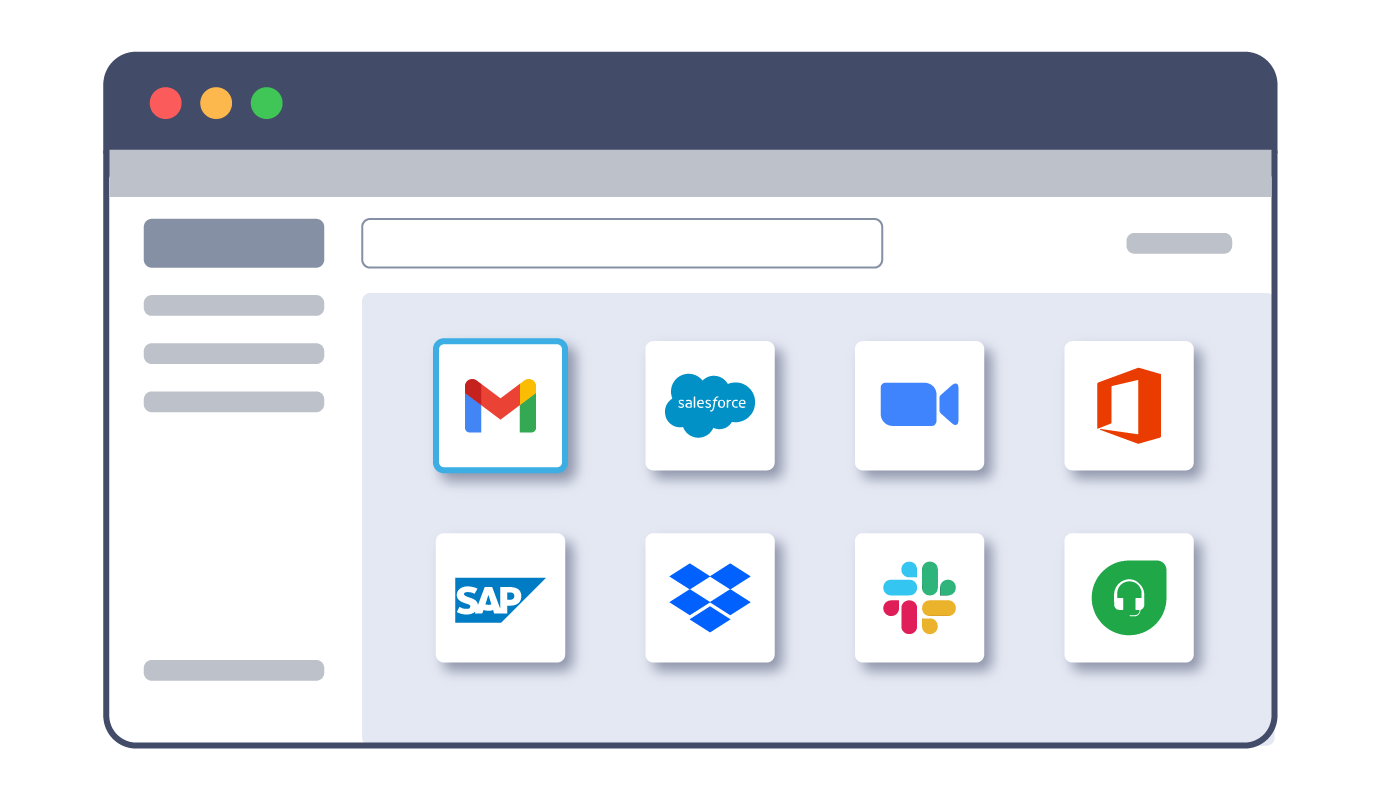
That’s why Zero Trust Application Access from Silo provides a distinct, cloud-based workspace to create tailored app launchers for different user groups. Constrict sensitive app access to only those a user needs in a 100% isolated environment with data transfer control.
Lock down the path for how any user accesses your apps — trust only what’s necessary.
Isolate access to your data from untrusted and potentially compromised devices and networks.
No client software installation. Trigger isolation in an existing browser based on context from your tech stack.
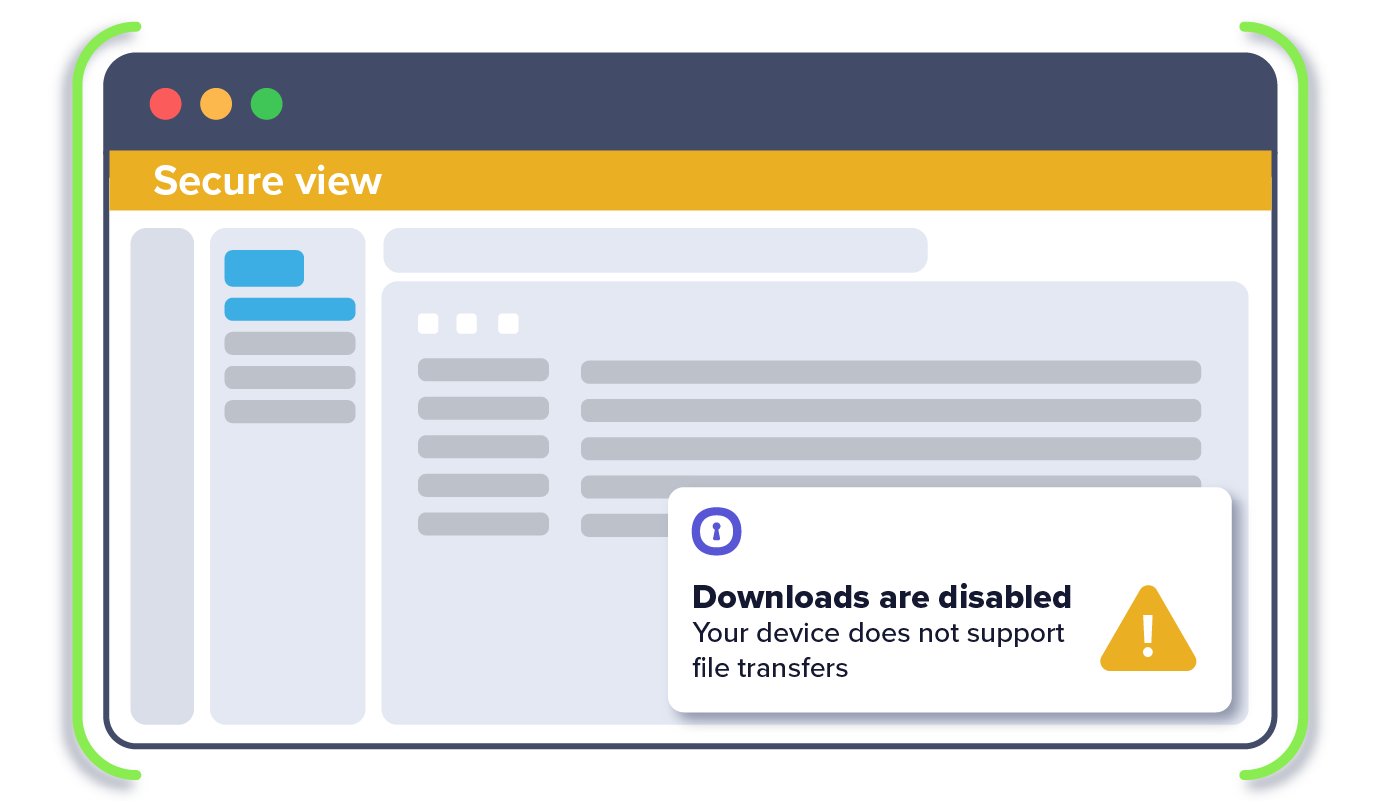
Control user passwords and data transfer rights even on unmanaged devices.
Built for the cloud, our solution deploys and scales easily to for same-day enablement.
Provide a one-stop-shop app launcher for employees or third parties to securely access sensitive apps.

1. IT sets policy to restrict access to desired SaaS apps through the Silo environment
2. IT sets DLP policies by application, limiting copy/paste, up/download, printing
3. User accesses the secure app launcher via their installed browser (e.g., Chrome)
4. User opens an app from within the isolated workspace, protecting apps and data from "last-mile" vulnerabilities
5. User is prevented from or allowed certain data actions in the app