Experience the ultimate flexibility with the Isolation API, allowing you to securely Quisque pellentesque id ultrices lacus ornare elit vitae ullamcorper. Learn More

Third-party app access
Rapidly enable suppliers, contractors and other partners, exercising control over unmanaged devices and reducing risk
BYOD and remote workers
Give distributed workforces the application access they need without data leakage or cyber risks
Secure app workspace
Create isolated, centralized environments to launch and use sensitive business applications tailored to specific groups
Authentic8 adheres to strict know-your-customer (KYC) requirements and requires a valid business email address in order to initiate followup. At this time, we do not sell individual licenses to consultants or students and will not provide demos to these parties.
The information you provide will be used in accordance with the terms of our privacy policy.
Information Technology Manager
 REVIEW
REVIEW
IT Director
 REVIEW
REVIEW
IT Analyst
 REVIEW
REVIEW

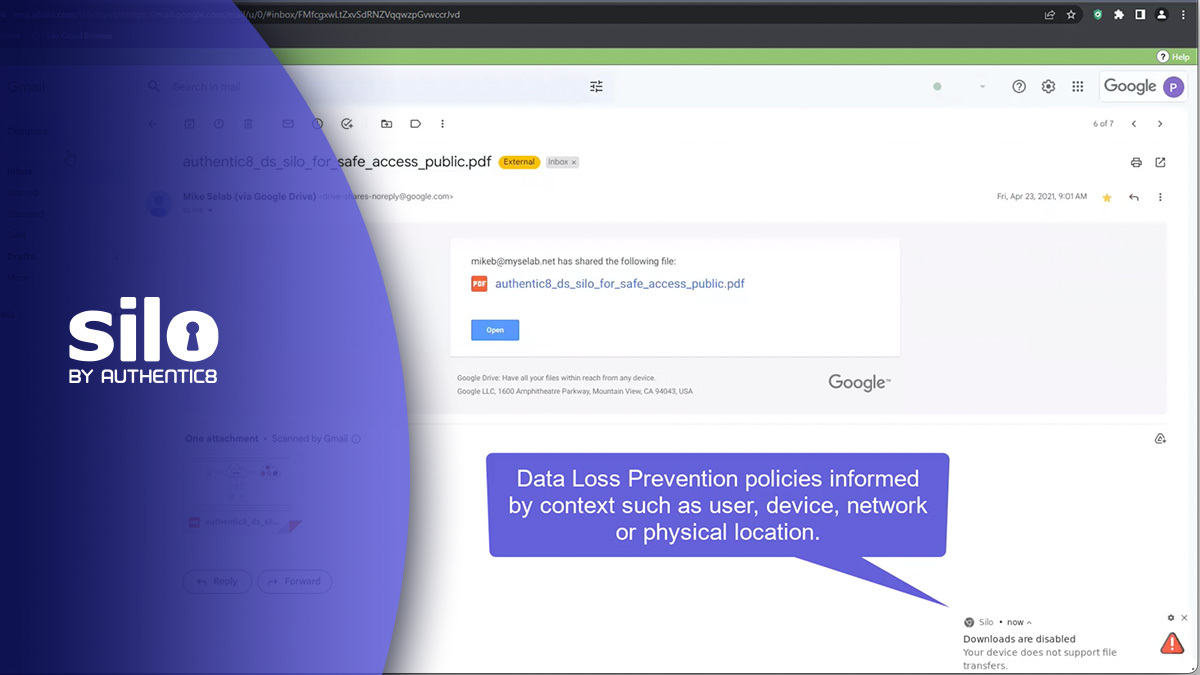
A decentralized, digitized, cloud-first world requires more than block or allow. Fine tune your organization's security and control with Silo.