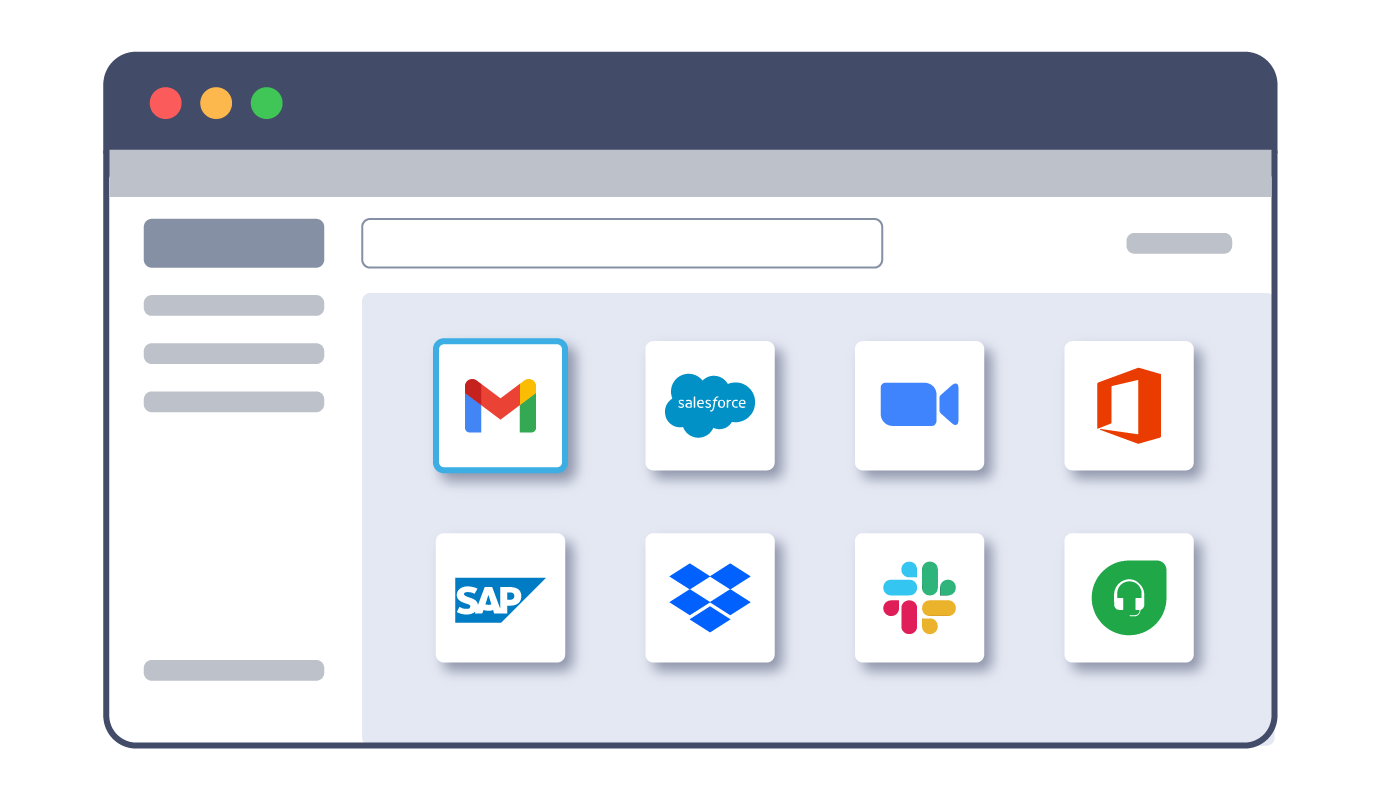
The practice of bring-your-own-device (BYOD) is highly desirable to end users but a nightmare for IT security teams. For years, IT has had to decide whether to sacrifice security for user productivity or vice versa: force users into clunky or imperfect solutions like virtual desktops or VPNs, or allow all access on BYOD despite the risk, lack of visibility and control.
Zero Trust Application Access gives organizations the ideal combination of iron-clad security and flexibility they need for BYOD users and hybrid workforces. Use web isolation to lock down access to critical apps without restricting workflows — and without installing software on personal devices.
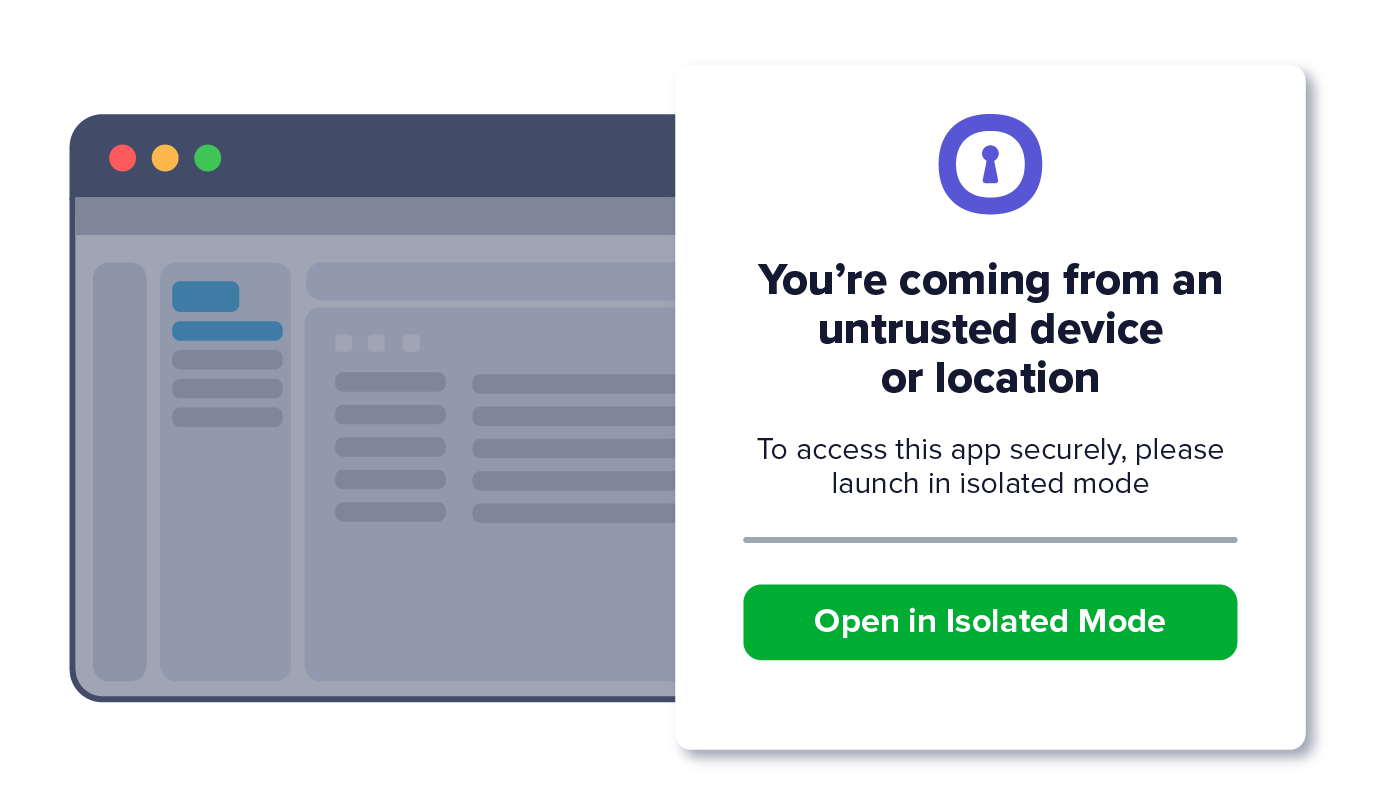
Trigger isolated app access and data transfer controls based on context such as network or device posture.
Shield critical apps and data from compromised devices and public connections.
Affix policies to users so access is always simple, secure and controlled.
Gain visibility into how your apps are being accessed and actions taken with data.
Built for the cloud, our solution deploys and scales easily.
Seamless and transparent security without asking users to install any software.

1. IT sets policy for BYOD-based access to SaaS apps to only work through Silo
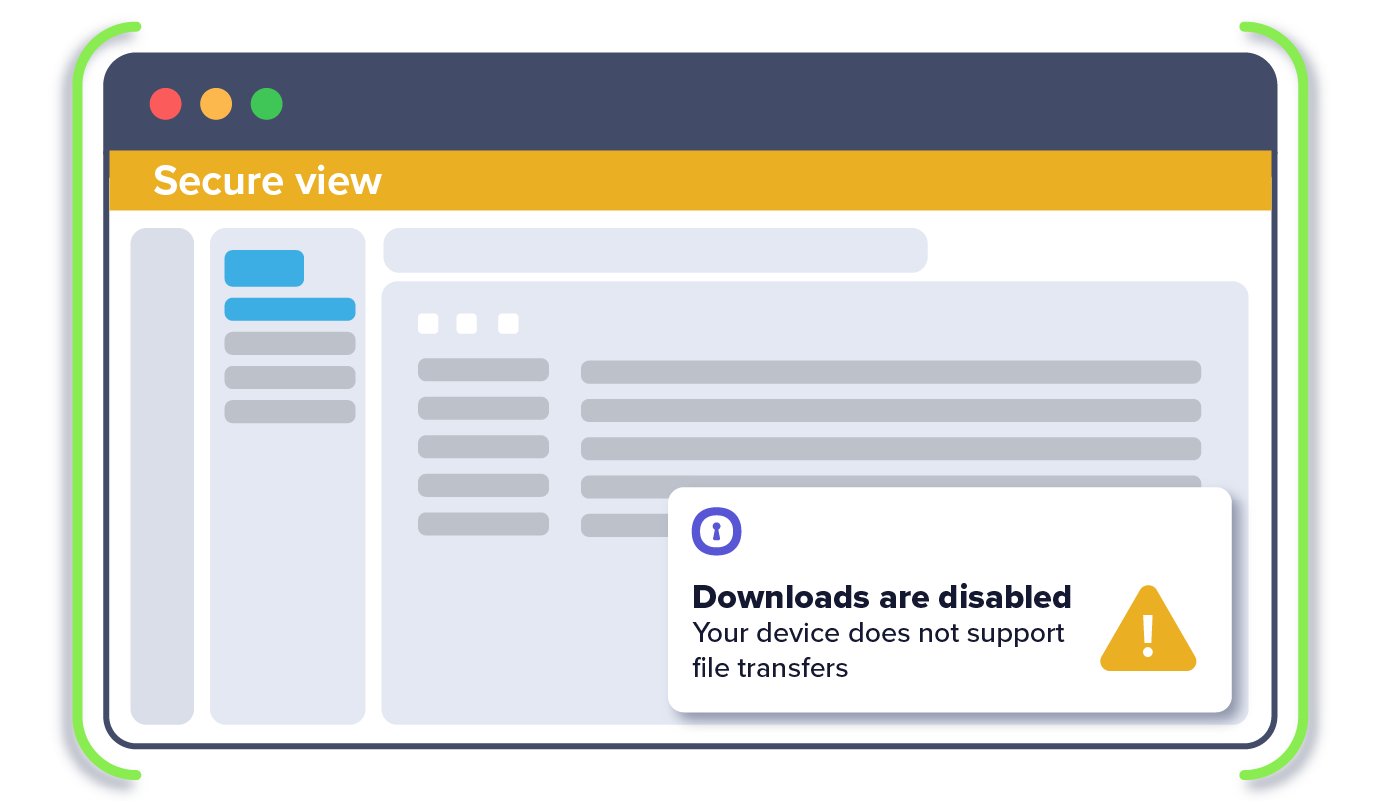
2. IT sets DLP policies, limiting copy/paste, up/download, printing
3. Third party opens application on existing browser (e.g., Chrome) on unmanaged device
4. BYOD user is transparently and seamlessly redirected into an isolated tab
5. BYOD user is prevented from or allowed certain data actions in the app (e.g., downloading)