Learn how Signal works and inspect the different ways in which OSINT gatherers can collect practical intelligence from the platform.
Signal is a free, open-source messaging application similar to WhatsApp. It allows its users to send text messages, share some types of digital files such as PDF and images/videos, and conduct voice and video calls in addition to group chat.
Signal is known for its robust encryption capabilities; everything you do using Signal is completely end-to-end encrypted, and even Signal administrators cannot read sent messages, which makes Signal a very secure messaging application.
The robust security capabilities of Signal make it ideal for exchanging sensitive information; however, it opens a few doors for OSINT gatherers to collect information from this platform.
Signal architecture
Signal runs using a centralized computing architecture, it has applications that run on iOS, Android and supports desktop programs on Windows OS, Linux and macOS.
To use Signal, you first need to register your mobile phone number to receive an SMS to activate your account. Although after signing up, you can use a username to hide your phone number when chatting with other Signal users.
According to BBC, Signal's user base is estimated to reach 70 million active monthly users. This number is small when compared with other platforms such as WhatsApp or Facebook messenger, however, this should not underestimate the importance of Signal app for OSINT analysts.
Inspecting Signal user profiles
As we already said, you need to have a phone number to register for a Signal account; however, beginning from 2024, users can add a username to their account to conceal their phone number when chatting with others.
By default, a user's phone number is not visible to other Signal users, although some users may opt to display it. Still, anyone who has your phone number stored in their phone's address book can see you are on Signal.
Inspecting the Signal phone number
If we know the target phone number, then we can conduct a reverse phone number search to see where this number appears online. This can reveal important information such as:
- Identify the telecom provider, such as T-Mobile or Verizon and the name behind a phone number –if applicable- using different tools such as:
- Identify target geographical location (Country/City): Approximate location based on area code or carrier data.
- Discover connected social media profiles. For instance, we can conduct a reverse phone search to check if the number is linked to social media accounts:
- Facebook (via "Find by phone number" in search)
- Instagram (if linked in profile)
- LinkedIn (if the user added it)
- Telegram (if "Privacy" settings allow phone number visibility)
- Conduct a phone number search using Google to see where this phone number appears online. Here are some Google dorks to execute this search on Google:
- "123-456-7890" OR "1234567890" | Search in web pages for the exact match.
- site:facebook.com "123-456-7890" | Search across a specific social media platform, in this example, I'm searching on Facebook.
- filetype:pdf "123-456-7890" | Search in PDF documents.
- site:pastebin.com "1234567890" | Search on a specific pastebin website. You can replace the pastebin.com with other pastebin websites available in this list: https://osint.link/#pastebin
- filetype:xls OR filetype:csv "1234567890" | Search in MS Excel and CSV files.
- intitle:resume OR intitle:cv "phone number" "contact" filetype:pdf | Search for a phone number in resumes.
- inurl:contact OR inurl:about "phone" OR "call us" | Search for phone numbers in "contact us" web pages.
- site:reddit.com OR site:quora.com "123-456-7890" | Search for phone numbers in discussion forums websites.
- inurl:wa.me OR inurl:api.whatsapp.com "1234567890" | Check if the Signal phone number is associated with a WhatsApp link.
- Search data breach repositories to check if the phone number appears in any previous breaches. Here are some data breach websites:
- Search for phone numbers in public records & people search engines, such as:
- Business/professional links: If the number is tied to a business, Google Maps or Yelp may show it.
Advanced Signal phone number investigation techniques
Aside from basic reverse phone number searches, OSINT analysts should consider temporal analysis of phone numbers. Phone numbers can be recycled by mobile carriers, which means the current Signal user may not be the original owner. To verify phone number history, we can execute the following checks:
- Check carrier reassignment policies - most carriers recycle numbers after 90-180 days of inactivity. IMEI website has a list of mobile network operators in the US.
- Cross-reference findings with timestamp data from other social media posts or data breach repos.
- Use Wayback Machine to see historical associations of a particular phone number on websites.
- Verify number portability records if available through carrier databases.
Inspecting Signal username
Signal uses a username in a way that is different from other social media platforms. For instance, a username is a way to initiate a connection with another Signal user without revealing your phone number. Using a username is not mandatory in Signal; however, if the Signal user has a username associated with their account, we should perform two searches on them:
- Reverse username search to see where this username appears. For instance, many people prefer to use the same username across different social media platforms, for example, the same username on Facebook and X.
- Know the meaning behind a username, such as its meaning in other cultures or civilizations.
However, before we start analyzing Signal usernames, we should first understand the Signal-specific naming conventions:
- Usernames can be between 3 and 32 characters.
- A user must include at least two digits at the end of their username.
- Usernames may only contain a-z, 0-9 and _.
- Signals usernames are case-insensitive.
- Usernames are unique across the Signal platform; once you take a username, no one else can take it.
Taking the Signal username naming convention into consideration, for example, trying first to search using the first characters of the username without the last digits, then by using the complete username, we can start our search.
To conduct a reverse username search, use any of the following services:
After finding where this username appears online, we should check the username's meaning to see if it has a special meaning in other cultures. Here are two websites that give you name meaning:
Users behavioral pattern analysis
Signal usage patterns can reveal additional intelligence about targets, such as:
- Online status indicators: Although Signal does not show "last seen" timestamps similar to WhatsApp, message delivery confirmations can indicate active usage periods.
- Response time analysis: Consistent response patterns may indicate target time zones, work schedules, or a form of automated responses.
- Message frequency: Sudden changes in communication frequency might indicate important life events, such as moving to another location or changing work schedule.
- Group participation: Active participation in multiple Signal groups can reveal interests, affiliations, or professional networks.
Start a new chat by username
To initiate a new chat, go to the Signal application, click the pen icon, and type the username or phone number in the search box. If the user already has a Signal account and you type their username correctly, you will find their name, click on it to access their Signal profile page (see Figure 1).
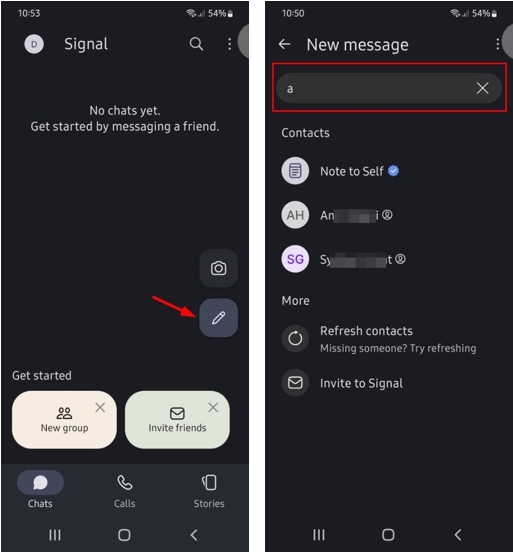
Figure 1 - Start a new Chat in Signal Application
After selecting the contact you want to chat with, click on the name to access the full profile page (see Figure 2).
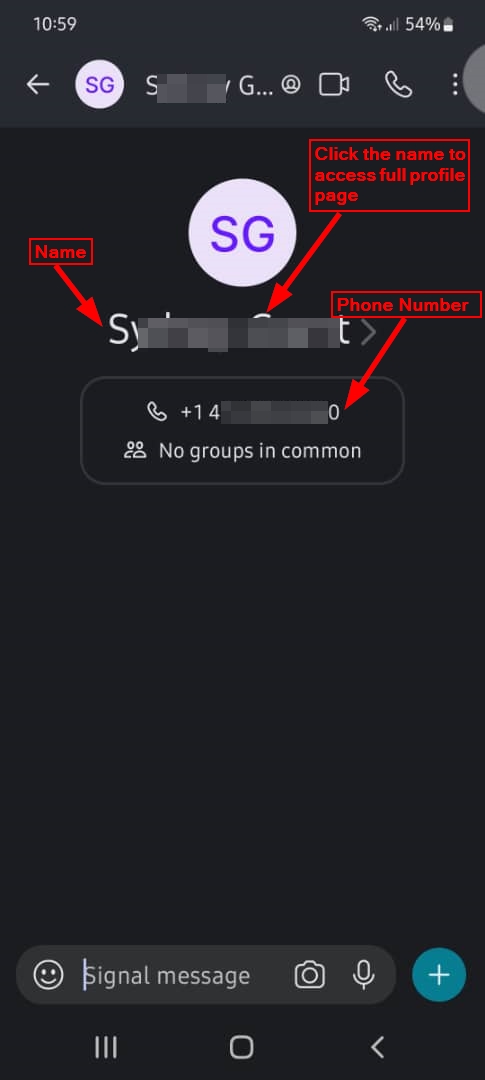
Figure 2 - Access Signal user full profile window
As we note from Figure 3, Signal provides little information about its users; however, we should ensure to inspect every element to expand our search and maybe discover new leads.
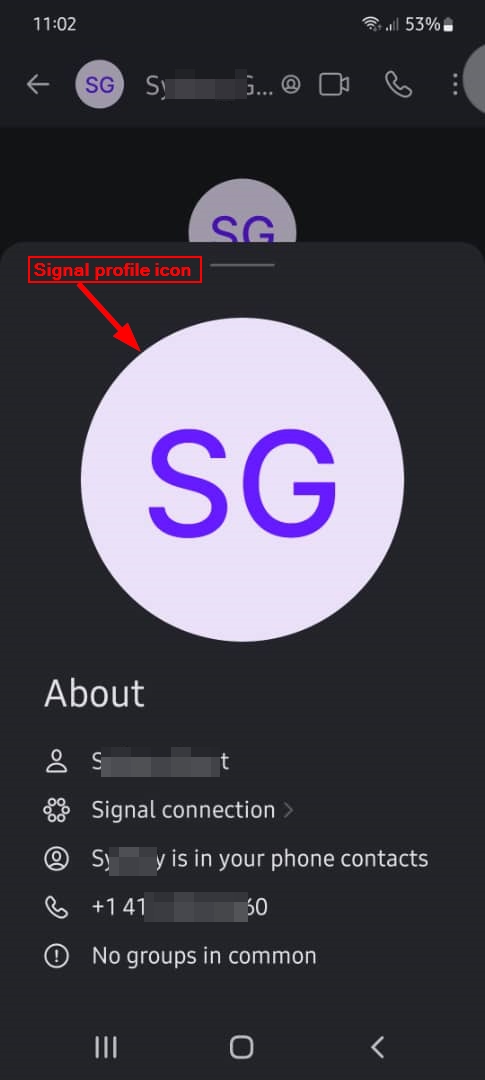
Figure 3 - Signal full profile window
Inspecting the Signal profile icon
A Signal user may use an icon (avatar) for their account, such as a personal picture or other image. If there is an image associated with a Signal account, then we should conduct a reverse image search to see where this image appears online. Here are some resources to start your image search:
If the image contains a human face, then it is beneficial to use a specialized face search engine to locate where this photo appears online:
It is worth noting that Signal does not allow taking screen captures from its web application; however, taking screen captures of the application is possible using the mobile application (I tested it using my Signal Android app).
Signal groups
By default, the person who created a Signal group is the admin, and all other users in the group are members only. Members can invite new users to join the group and can change the group avatar and name as they want (if this option is allowed by the group admin).
Group link is turned off by default; however, if the group admin enables it, then anyone with that group URL can access and join the group (if the admin disables the option "Require Admin Approval"). Signal group link appears similar to this URL:
https://signal.group/#CjQKIIiP8Y-7nDes9K_PLK7KKPyjTxSBYj2afdLMr7p4hmnsEhC9I-tRwOJHIIJNo_dZ-fD9
Each Signal group can hold up to 1000 users. If the group admin has activated the option "Require Admin Approval", then anyone who wants to join that Signal group needs to get admin approval first.
Investigating the Signal group link, we can easily find that it starts with https://signal.group/#<group_code>. We can conduct a Google search to see publicly exposed Signal groups using the following dorks:
- inurl:https://signal.group/# | This search for URLs containing the Signal group base link.
- site:example.com https://signal.group/# | Find Signal groups on a specific website. Replace example.com with your website, such as reddit.com.
- "Join my Signal group" OR "Signal group invite" OR "Signal group link" | Search within web pages for Signal group invite links.
- "https://signal.group/#" site:twitter.com OR site:facebook.com OR site:reddit.com | Search for Signal group links on popular social media platforms.
- "https://signal.group/#" AND "crypto", "https://signal.group/#" AND "OSINT" | Search for Signal group links for a specific topic. You can change the topic keywords as you want.
- "https://signal.group/#" ext:md OR ext:txt site:github.com | Search for Signal groups in GitHub or other code repositories.
It is worth noting that most Signal groups are private, so expect to get limited information from public groups.
Advanced group investigation techniques
Signal groups offer more intelligence opportunities beyond basic link discovery:
- Group metadata analysis: Check group creation dates, member count changes, and admin transitions can reveal target group organizational structures.
- Invitation pattern tracking: Who invites whom can show recruitment patterns or hierarchical relationships between group members.
- Group name evolution: Changes in group names or descriptions might indicate operational phases
- Cross-platform group migration: Groups often migrate between different platforms - Search for similar group names on Telegram, Discord, or WhatsApp. Here are some Google dorks to initiate your search:
- "Your Group Name" site:telegram.me OR site:chat.whatsapp.com OR site:discord.gg OR site:reddit.com | Replace "Your Group Name" with the actual group name
- intitle:"Your Group Name" OR intext:"Your Group Name" site:reddit.com OR site:twitter.com OR site:facebook.com | Searches for the group name in page titles or text on major platforms.
- "Join Your Group Name" OR "Invite to Your Group Name" site:telegram.me OR site:reddit.com | Looks for invite messages that might reference the same group on different platforms.
- "Your Group Name" (inurl:group OR inurl:chat OR inurl:channel) site:telegram.org OR site:discord.com | Searches for target group/channel pages on Telegram and Discord.
- "Your Group Name" filetype:txt OR filetype:csv | Checks text files that might list group names.
Operational security for an OSINT analyst when inspecting Signal
Signal OSINT activities can expose investigators to external parties via:
- Creating Signal accounts reveals your phone number to targets.
- Signal may notify targets if they have your investigation number.
- Joining groups makes your presence visible to all members.
To counter such risks, OSINT gatherers should consider using dedicated investigation phone numbers when conducting investigations on the Signal platform.
Signal's end-to-end encryption protects message content, but metadata and user behaviors remain accessible to skilled OSINT analysts. This guide demonstrated how phone numbers, usernames, profile images, and group memberships can reveal valuable intelligence about Signal users.
The techniques covered - from reverse phone searches to cross-platform group analysis - work because human behavior creates patterns even within highly encrypted environments. Phone numbers remain the primary investigation entry point, while Signal groups offer the richest intelligence opportunities through public links and membership patterns.
Remember that Signal OSINT is most effective when integrated with broader investigation methodologies. Always consider operational security risks and legal boundaries when conducting these investigations, as Signal users specifically choose this platform for privacy and security reasons.
Tags OSINT research Social media

