How online tracking for customized ads could be affecting your research. Learn how to avoid those persistent cookies work and how to avoid them to get the results you need.
Online tracking techniques encompass a range of methods used to monitor and gather information about individuals' online behavior. When engaging in OSINT activities, it is crucial to safeguard the investigator's digital presence by concealing it effectively. Understanding the various tracking techniques employed online is essential in achieving this.
Researchers must understand different tracking techniques, including cookies, browser fingerprinting, mobile device identifiers, tracking pixels and location tracking. Each technique is unique in its functioning and the extent of information it can potentially gather about online users.
Online tracking techniques
Hiding the activity of OSINT investigators online is often crucial for the success of their information gathering. For instance, when researching a criminal organization, revealing our search could put the investigator at risk and alert the criminals to the research, giving them time to hide evidence and conceal their activities. Different types of data can be tracked online, such as:
- Personal information: Online activities can expose personally identifiable information (PII) such as email addresses, mailing addresses, phone numbers and birth dates
- Internet browsing history: When you search online using popular search engines like Google or Yahoo, visit websites or click links in emails, your activities can be recorded by your internet service provider (ISP), the websites themselves and other entities like major IT providers (e.g., Facebook, Google, Twitter) and government agencies
- Location data: Many mobile applications collect users' geolocation data, revealing their geographic locations over time
- Social media activities: Social media platforms such as Facebook and Twitter can track users across various websites, potentially revealing significant information about their internet usage habits
- Online merchants: When making online payments, your information is recorded by online merchants. Some merchants, like Amazon, track your activities to personalize their products
- Website tracking: Websites employ different tracking technologies, such as fingerprinting, cookies and IPs, to monitor visitors and understand their browsing behaviors
- Online communication metadata: When sending and receiving emails, the email header contains technical information related to your device and/or current location
Other tracking methods exist, but their usage depends on the specific service, the level of user consent and the security settings employed on the end user's device.
What’s tracking you?
Cookies
Cookies are the most popular technique used to track internet users online. There are different types of cookies, however, the most popular is HTTP cookies.
HTTP cookie
An HTTP cookie is a small text file created by a website server when you visit a website for the first time and is stored within the user’s smartphone or computer web browser. It contains information such as the cookie name, expiration date, value and domain name. The purpose of a cookie is to identify your device when you revisit the website, allowing it to remember certain preferences or settings (e.g., theme and language settings).
There are two types of HTTP cookies:
Session cookies: Also known as temporary cookies, session cookies are created and stored on the user's device during a browsing session. These cookies are programmed to be deleted automatically once the user exits the web browser window or closes the application. They are stored in temporary memory on the user's device.
Persistent cookies: Unlike session cookies, persistent cookies remain on the user's device until they reach their expiration date, which can be set for a specific date or indefinitely! Persistent cookies are commonly used for tracking user visits to the same website over time, allowing website owners to provide personalized experiences.
Persistent cookies can be renewed by cooperating owners of other domains when you visit their sites. They create cooperative networks to keep cookies from expiring, even when you don’t visit the original site again.
A brand new Silo Session with no history or cookies
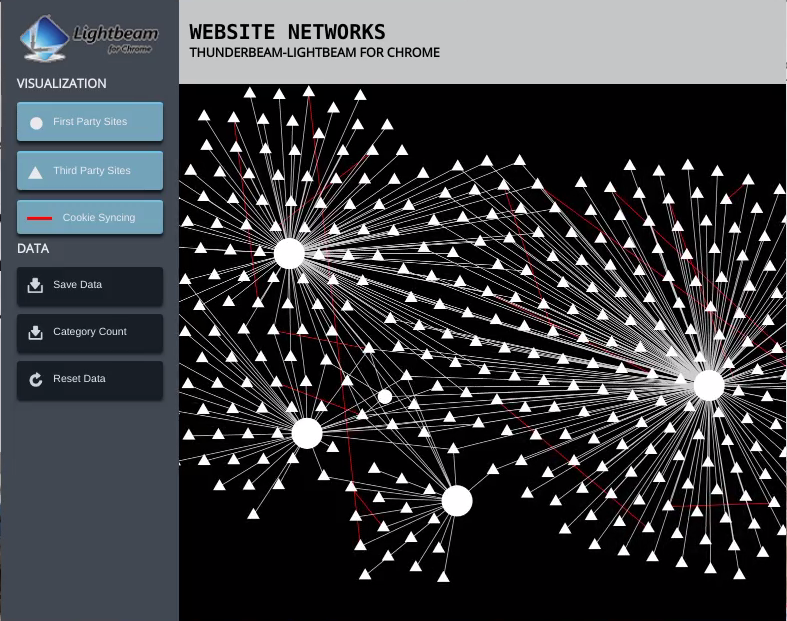
The image above shows the number of cookies on a clean instance after visiting Google News, clicking on two articles and then visiting Ebay and Nike. Each main site allows for a series of interconnected cooperating cookies.
What makes cookies dangerous for OSINT gatherers is their ability to track their browsing history over time. In this context, we can group cookies into two categories:
- First-party cookies: These cookies are created by the website you visit directly. These cookies do not pose privacy risks in general. However, OSINT researchers should delete them
- Third-party cookies: These cookies are installed by websites other than the ones you directly visit. For example, when you visit a website like example.com, it may contain tracking elements or advertisements from other websites. These third-party websites can install cookies on your device to track your online activity, often without your explicit knowledge
The Facebook “Like” and Twitter “Tweet this” buttons installed on millions of websites are examples of third-party elements used to install cookies on end-user devices, even if the user did not click on them.
You can view saved cookies under the Google Chrome browser by checking this guide.
Silo for Research was designed specifically for conducting comprehensive online investigations. Silo provides users with an isolated, anonymous environment that ensures utmost privacy throughout their search activities.
By leveraging Silo, users can open up a new, sterile instance every time they do a search, ensuring confidence in the results, and knowing that all tracking cookies will be automatically eradicated upon session closure. Previous sessions never affect the next search or follow the user back to their personal accounts.
Want to see this web come together for yourself? Book a demo.
Tracking pixel
A tracking pixel is a small, transparent graphic file (usually a 1x1 pixel) embedded within a website's HTML source code or email message. It is used to monitor and track internet users browsing behavior, similar to cookies.
The tracking pixel graphic is connected to a tracking pixel server. When a user visits a website that contains a tracking pixel code, their web browser follows the URL and requests to download the invisible tracking pixel graphic file. Various technical information about the user's device is collected and then sent to the tracking pixel server by downloading this image. This information includes:
- The operating system type (e.g., computer OS or mobile and its type: Mac, Android, Windows, Linux)
- The type of website or email used, such as whether it is accessed from a mobile device or desktop
- The type of client being used, such as a specific web browser type or mail client, such as MS Outlook or Thunderbird
- The screen resolution of the client's device
- The time when the email was opened or when the website was visited
- If there are multiple tracking pixels employed on the visited website, it can track user activities across the website (e.g., which pages were visited and how much time was spent on each web page)
- User internet protocol (IP) address which can identify the user’s geographical location and their ISP provider
Browser fingerprinting
Digital fingerprinting is an advanced tracking technology that aims to create a complete profile of internet users. Even if you use your web browser in Incognito or private browsing mode and you keep clearing your web browser cookies regularly, websites employing fingerprinting techniques can still track your internet browsing activities.
How does fingerprinting work?
When you access a website that leverages this technique, a small JavaScript code runs in the user’s web browser background. The fingerprinting code will gather various technical information about the web browser add-ons, software and hardware characteristics of the user device, such as:
- Operating system type and version
- Device model and unique number (if it is a mobile device)
- Device battery level
- Device screen size and resolution
- Installed operating system language
- Installed fonts
- Web browser type and version
- Installed add-ons and browser-unique configuration settings
Combining these artifacts builds a unique user profile that can distinguish a particular user device among millions of devices and is used to track users across different websites.
Many websites allow users to check their device fingerprint:
Device identifiers
All mobile devices, such as tablets and smartphones, have unique alphanumeric strings that distinguish them globally. Installed applications can access these identifiers, which can be used to identify mobile users worldwide.
For iOS, the device ID is called “Identifier For Advertisers”, while on Android, the device ID is called “Android Advertising ID (AAID)”.
Location tracking
The most commonly used technique for tracking the locations of internet users is by using their IP addresses. In the case of web applications, the GPS coordinates of the device can also be employed to track users' locations over time precisely.
Websites and search engines utilize IP address tracking to offer customized services. However, researchers should conceal their IP addresses when conducting OSINT research. This can be accomplished through the use of virtual private network (VPN) service or the TOR network. But using a VPN or Tor is not foolproof. Tor can also expose researchers to unintended dangers if accessed without a protocol or plan.
A purpose-built research platform can protect researchers and give them unique advantages in location-based research. The ability to set the location, browser and language settings to precise location (where they are not currently sitting) can not only help a researcher from being sniffed out, but also give them the advantage of search results unavailable on a non-native browser. With points of presence in a remote browser, researchers can automate the ability to automate the collection of data at an appropriate time for the zone, in order to avoid tipping off webmasters.
Protecting your research from online trackers
Various entities employ online tracking techniques to improve internet users' browsing experience and to offer personalized services and advertisements. However, for OSINT researchers, understanding how these techniques work is essential to mitigate them and to conduct OSINT searches covertly, avoiding attracting unnecessary attention to their online activities.
To learn more about how cookies could be impacting your investigation or how your research could be improved with the help of points of presence, book a demo today.


