While automated systems and community self-policing raise flags for harmful conduct or inappropriate content, deeper trust and safety investigations may be needed to get the whole picture and insight on the appropriate action. This research often extends beyond the confines of the company’s platform or service to the broader web, and could result in malware exposure, retribution of negative brand associations.
Silo for Research reduces time-to-insight and protects the analysts tasked with conducting trust and safety investigations. With better analysis, organizations can make better decisions to keep their communities safe and secure. Read more in our Trust and Safety solution brief.

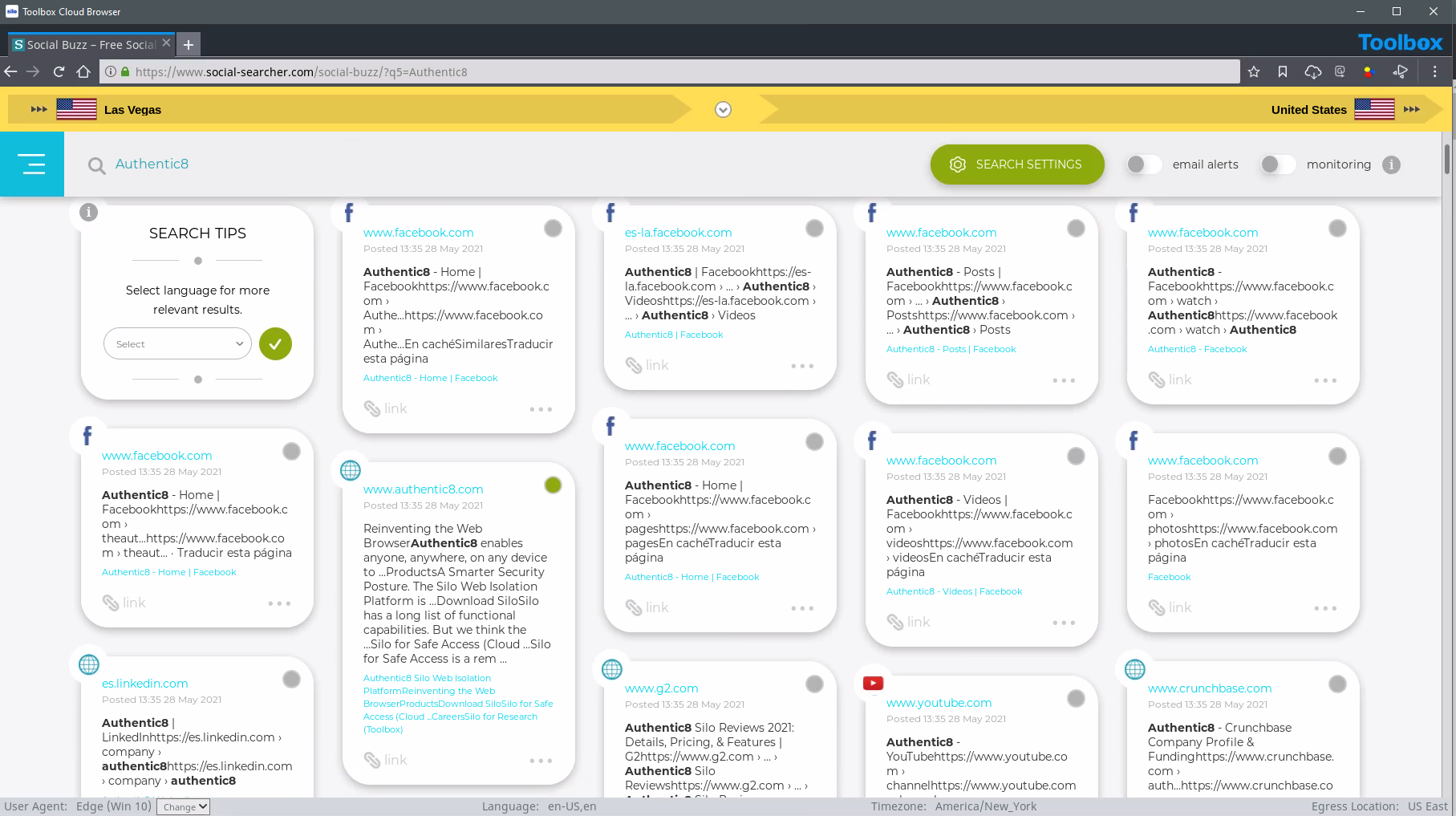
Trust and safety analysts need access to all available information in order to take or recommend appropriate action. But roadblocks like IT policies, regional IP restrictions or other access restrictions in the target environment keep researchers from accessing third-party communities. Silo for Research safely and securely opens up these sources — on the surface, deep or dark web — regardless of geography and with a full audit trail.
Because Silo executes remotely, no web-native code ever reaches the endpoint, and no endpoint code can affect web data. Silo keeps all scripts, cookies, trackers, executables, binary content and everything in between in the secure, remote container. Thanks to our proprietary access protocol, trust and safety analysts get full-fidelity access to the web without ever actually touching it. And regardless of the level of sophistication of countermeasures, threats are always neutralized. Collected information can also be securely stored and shared off network.
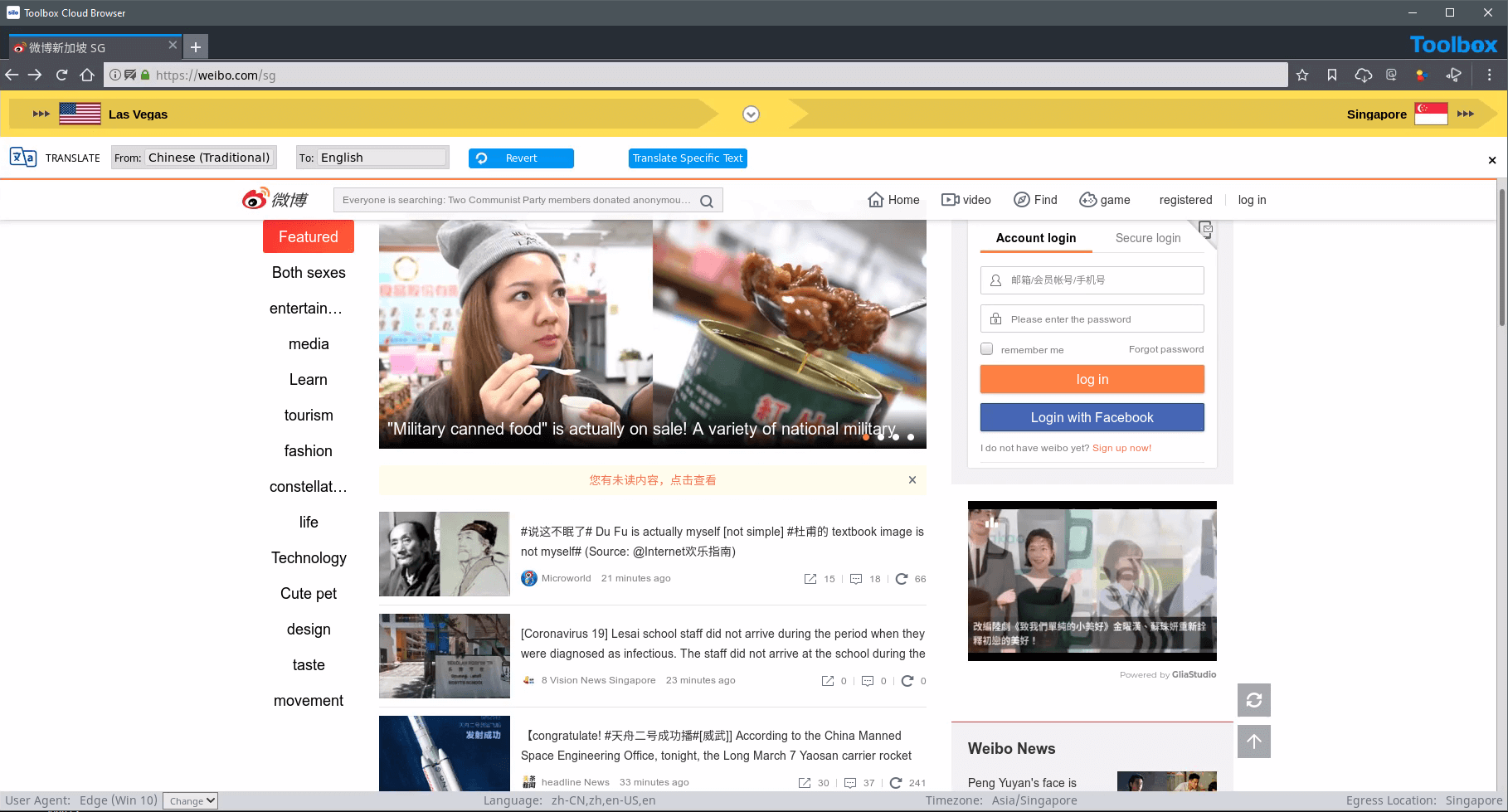
Obtain information without tipping off the subject to analysts’ identity or affiliation to their company. Silo for Research can execute in dozens of geographies, showing a local IP that never refers back to the organization. And it can be configured to fit the local characteristics to blend in with the crowd (e.g., OS, browser, device type, time zone, language, keyboard settings). Built-in tools like out-of-band language translation, intelligently automated collection and multi-search workflows also maintain tradecraft while trust and safety analysts search the web.

Trust and safety teams protect their company’s online platform and user community by enforcing acceptable use policies and monitoring marketplace integrity. Acceptable use enforcement may include investigations related to harmful assets posted from hate groups or criminal enterprises engaging in phishing and malware-driven posts targeting the community. Those with marketplaces may be involved in identifying, removing and reporting to law enforcement counterfeit, stolen or fake digital and physical goods for sale.
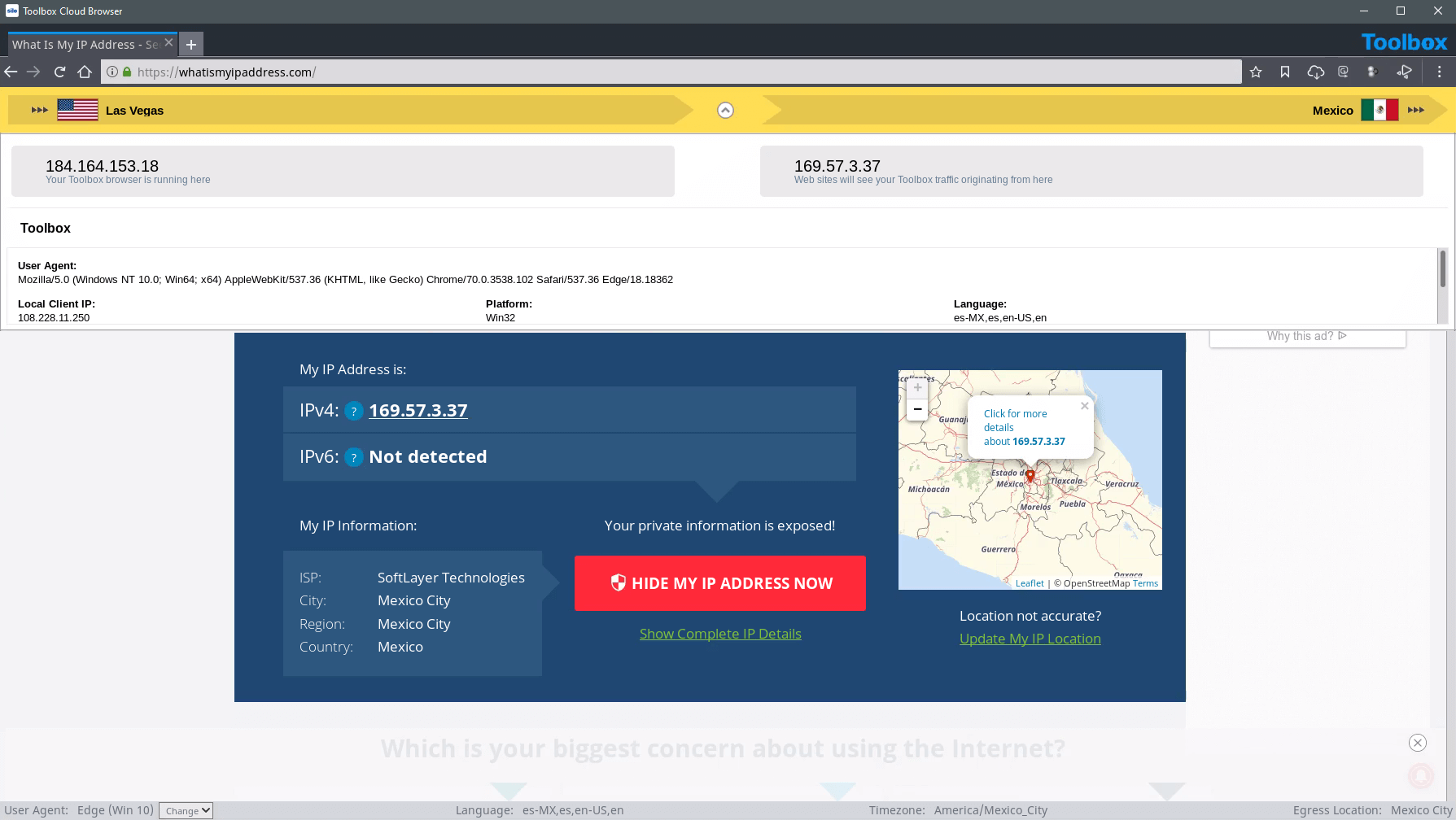
With Silo for Research's managed attribution functionality, you can completely customize how you appear to sites and people you interact with online. Manipulate a variety of your device details including language, time zone and keyboard settings, as well as the browser, OS and other elements. Appear to be browsing from any of Authentic8's dozens of global egress nodes, and show a local IP address that never refers back to you or your organization.
Yes, dark web access is seamlessly integrated within Silo for Research and its suite of analyst tools. You do not need a separate, standalone dark web browser. This integration provides investigators with full isolation from dark web cyberthreats (e.g., malware-laden sites, forums, marketplaces) and anonymity from counter-surveillance efforts utilized by malicious actors.
Yes, Silo for Research integrates with Authentic8 Secure Storage, an encrypted, audited and cloud-based storage repository for users and groups. Investigators may be required to capture and collect content as part of their process. And to maintain efficacy of potential evidence, a proper chain of control and evidentiary requirements must be met.