Fortifying the frontline: A practical guide to using OSINT for modern border security
The internet facilitates not only cybercrime but also increasingly enables different types of crimes executed in the physical world. The bread crumbs left behind could assist agents and analysts on their mission to secure the nation’s border.
OSINT for border security is essential to national defense. Beyond managing unauthorized migration, open-source intelligence helps agencies prevent drug trafficking, human smuggling, and cross-border criminal operations.
This article examines how security officers and law enforcement agencies can use OSINT techniques to strengthen border security measures and prevent unauthorized individuals and gangs from exploiting borders for malicious purposes. Specific applications include monitoring social media networks used by trafficking organizations, analyzing publicly available satellite imagery to identify unofficial crossing points, and tracking digital footprints of known criminal networks operating across borders.
How do law enforcement use OSINT for border security?
Many different OSINT fields are applicable to boost border security, from the proliferation of social media, to geolocation techniques, to transportation intelligence. Learn about each below.
Social media intelligence (SOCMINT)
SOCMINT can be used to identify and monitor migrant networks, gather real-time route intel and detect smuggling activity and propaganda — with verification baked in.
> Looking for a how-to guide for collecting social media intelligence? Check out the Practical guide to SOCMINT research.
Tracking migration networks
Social media platforms can be used to identify key migrant network facilitators, understand their methods, discover routes and anticipate new trends.
Key methodologies and techniques:
- Identify social media platforms and communities — Smugglers and migrants use specific platforms based on region, culture and security. For example, Facebook is used for closed and secret groups where information is shared relatively privately, and smugglers often pose as "travel agents." Instagram & TikTok are used for sharing real-time journeys through Stories, Reels and posts. Twitter (X) is commonly used for rapid, public information sharing and news updates on border conditions. YouTube is used to host lengthy videos documenting entire journeys. WhatsApp/Telegram, these encrypted messaging apps are the final step for direct communication and coordination with smugglers. Although they are private, their use is often advertised on more public platforms.
- Keyword and hashtag monitoring — OSINT gatherers can search for smugglers using a plethora of specific keywords and hashtags in different languages related to migrants. For example,
"Package" or "parcel" = a group of migrants.
"Guides" or "coyotes" = smugglers.
"Safe house" or "hotel" = temporary accommodation.
"The game" or "playing" = the act of attempting to cross.
There are also route-specific hashtags, such as #RutaBalkanica (Balkan Route), #DarienGap, #Europa, "visa free," "sin visado," "بدون فيزا" and #LibyaToItaly.
- Specific terms — Search for particular keywords commonly used by migrant networks, such as "100% guarantee," "safe journey," "new route," "documents for [country]."
Network analysis and mapping
This is the most important analytical step. The goal is to move from tracking individual accounts to a map of the entire network. It involves the following:
- Identify central nodes — Who are the most connected users? These are commonly the facilitators or key information brokers of the migrant networks. OSINT analysts should look for accounts that consistently post updates, answer questions, and share contact information.
- Extract contacts — Smugglers often list WhatsApp, Telegram or Signal numbers in their bios or posts. These become crucial identifiers to track them.
- Analyze relationships — Using social network analysis tools, OSINT analysts can visualize how different accounts (smugglers, scouts, drivers, migrants) are connected, this helps reveal the hierarchy and structure of the network.
Geolocation and route mapping
Images, videos and text posts can reveal important information about migrant networks and smugglers. For instance:
- Photo/Video analysis — Images and videos shared by migrants are considered intelligence goldmines, as they might reveal:
- Landmarks — Such as mountains, unique buildings (see Figure 1), and road signs.
- Transportation types and characteristics — Such as identifying bus companies, train types, or specific boat models can pinpoint location.
- Metadata — If not stripped by the social media platform, photos can contain GPS coordinates (EXIF data) among other information.

Figure 1 - A Libyan smuggler is promoting his boat in a Facebook post to encourage people to register for a trip from Libya to Italy. The posted photo contains many details that can be used to track the smuggler's home address in Libya
- Checking-ins and location tags — Migrants commonly tag locations at gathering points, safe houses or after successful crossings. Such information can be mapped to identify smuggling routes from beginning to end.
- Real-time updates — Posts like "Leaving Izmir now", "من زواره الي لامبيدوزا" or "Waiting in the forest near Bihac" provide real-time situational awareness of migrant concentrations (see Figure 2).
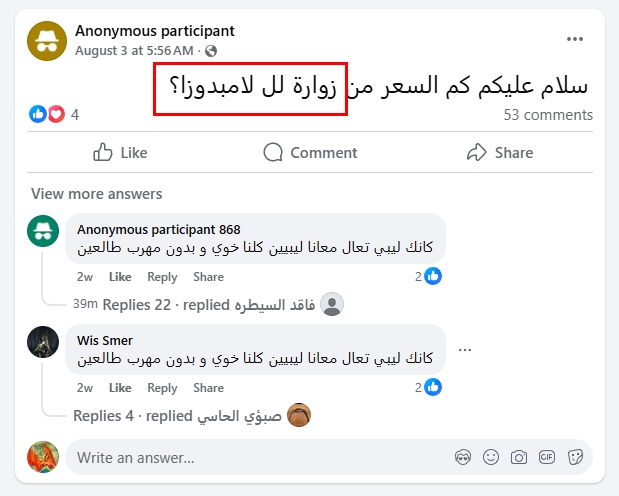
Figure 2 - Most migrants from Libya to Italy go from the City of Zuwara in Libya, which is a major gathering point for African migrants before going to Italy by boat
Sentiment and trend analysis
Sentiment in social media posts and comments can reveal important information about migrants' routes and specific border points. For instance, it can reveal:
- Shifting routes — An increase in complaints about a specific border point (e.g., increased patrols, violence from guards) can indicate that a route is closing, prompting smuggler networks to open a new one. OSINT Analysts can anticipate this shift by monitoring migrants' posts online.
- Changing prices — Monitoring the discussed prices for crossing specific border segments indicates the cost of business for smugglers and the demand for particular routes.
- Crisis detection — A spike in posts about drownings, accidents, or illnesses on a particular route can alert authorities to a developing humanitarian crisis.
Free OSINT tools for tracking migration networks
- Twitter advanced search: (we already have a guide for conducting OSINT on the Twitter (X) platform).
- Facebook search: (we already have a guide for conducting OSINT on the Facebook platform).
- Social Searcher: Free social media search engine.
- Google Reverse Image Search
- Maltego (Community Edition): Network analysis & mapping.
Geospatial Intelligence (GEOINT)
GEOINT enables OSINT gatherers to conduct wide-area surveillance, verify physical features, monitor temporal changes, and plan operations using imagery and maps. Primary applications for border security include:
- Change detection — Using historical satellite imagery to identify new paths cut through forests, makeshift camps or unauthorized constructions near borders. This includes detecting fresh tire tracks, cleared vegetation or temporary structures indicating increased activity.
- Route analysis — Mapping terrain to predict smuggling or migration corridors based on topography, water sources and natural barriers.
- Verification — Corroborating intelligence from other sources. Cross-referencing social media geotagged photos with satellite imagery confirms location accuracy and operational patterns.
- Drone footage analysis — Monitoring remote areas through commercial satellite feeds and publicly available aerial imagery. Real-time analysis requires coordination with official surveillance platforms.
Some tools for conducting GEOINT on border security:
- Google Earth Pro: The industry standard for historical imagery and basic GIS measurement tools.
- Sentinel Hub Playground: Access to free, high-frequency satellite imagery from the ESA's Sentinel constellations.
- NASA Worldview: Excellent for near-real-time imagery and monitoring large-scale environmental changes that might affect routes.
- QGIS: An open source Geographic Information System (GIS).
- OpenStreetMap (OSM): Sometimes contains more updated and detailed information in remote areas than commercial maps.
Deep and dark web monitoring
Monitoring the darknet allows OSINT gatherers to discover threats related to illicit trafficking, forged documentation and organized smuggling rings operating in hidden online spaces.
Key applications include:
- Identifying illicit marketplaces — Finding forums and markets where stolen passports (See Figure 3), visas, and other identity documents are sold. Operators frequently advertise "clean" passports from specific countries, often pricing based on visa-free access rankings. Markets display sample photographs of document quality, watermark replication techniques and delivery methods across borders. Vendors establish reputations through customer feedback systems similar to legitimate e-commerce platforms.
- Mapping trafficking routes — Monitoring discussions where smugglers offer their services, detailing routes, prices and methods. Posts reveal seasonal route preferences, checkpoint avoidance strategies, and coordination points for human cargo transfers. Smugglers advertise specialized services for different demographics, pricing structures based on route difficulty and success rate guarantees. These discussions often reference specific geographic landmarks, border patrol shift patterns, and optimal crossing times.
- Threat actor analysis — Understanding hierarchies, specializations, and reputations of different smuggling organizations. Analysis reveals operational divisions between document forgers, route coordinators, transportation providers and safe house operators. Organizations demonstrate territorial boundaries, competitive relationships, and collaborative partnerships for complex multi-border operations.
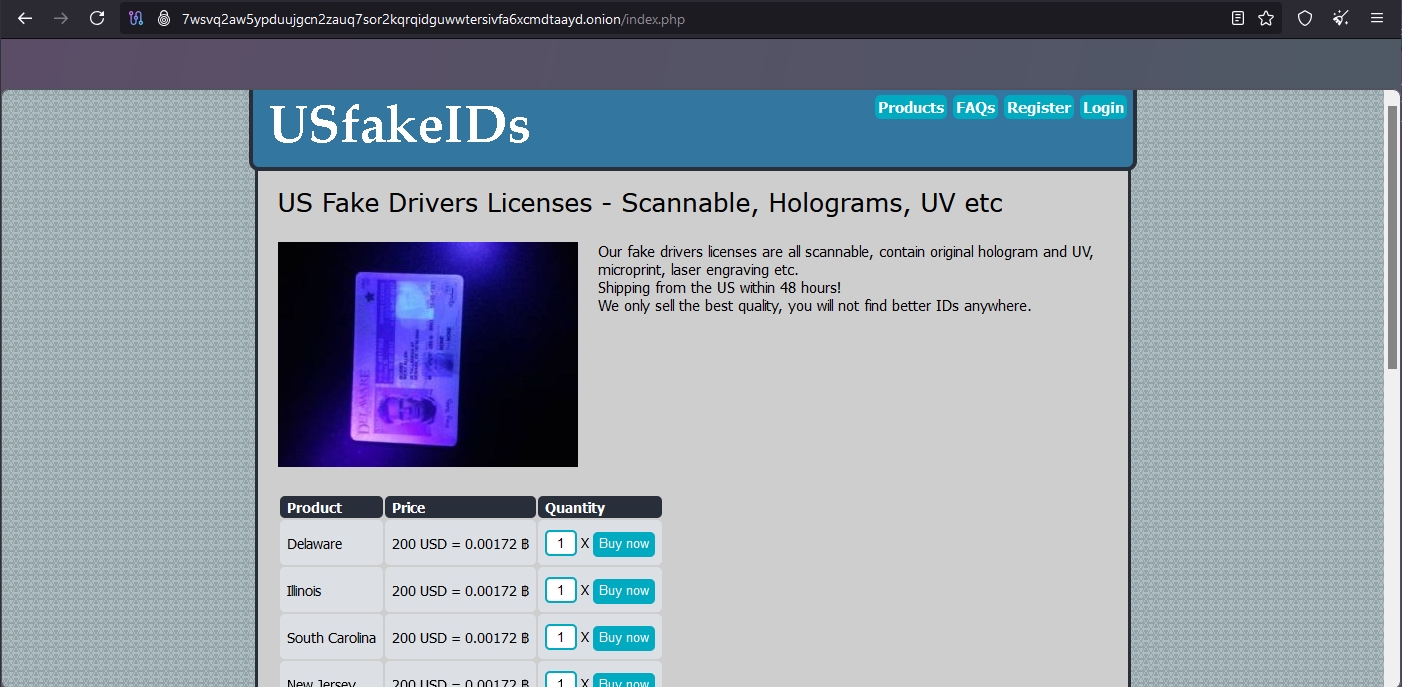
Figure 3 - An onion website selling fake US driving licenses
Free OSINT tools & services for researching the dark web:
- Tor Browser in Silo: Essential for accessing .onion sites on the TOR dark web safely
- DuckDuckGo: The default search engine on Tor, helpful in finding indexed dark web resources.
- Ahmia: A search engine that indexes onion sites, helping to discover relevant forums and markets.
- Torch: Another search engine for the dark web
- OSINT researchers often rely on curated lists and directories of known marketplaces and forums, which are shared within the community, such as The Hidden Wiki and OnionLinks.
OSINT techniques give law enforcement agencies strong tools to improve border security efforts. Social media intelligence uncovers smuggling networks and real-time migration patterns. Geospatial analysis spots unauthorized crossing points and changes in routes. Monitoring the dark web reveals document trafficking and the structures of organizations that operate outside traditional surveillance.
Success relies on systematically combining these methods. Agencies need to build specialized knowledge, follow security procedures, and create legal guidelines for gathering intelligence. As criminal networks change their digital presence, border security operations must continuously update their OSINT skills to keep an edge over increasingly complex trafficking groups.
Safely investigating organized crime for border protection
Social media is a two-way street. Analysts and agents who employ open-source techniques need safeguards in place to make sure the bad actors they investigate aren’t looking back. The Silo investigation platform combines remote browser isolation to covertly access any are of the web with sleek analysis features and audit-ready compliance. See why 750+ government agencies and organizations choose Silo. Request a demo today.
OSINT for border security FAQs
What is OSINT in border security?
Open-source intelligence (OSINT) in border security involves using publicly available data—like social media, satellite imagery, and dark web sources—to detect smuggling routes and cross-border threats.
How do border agencies use social media intelligence?
Border agencies use social media intelligence (SOCMINT) to identify migrant networks, track movement trends, and gather real-time updates on trafficking activities.
What tools help analysts conduct GEOINT for border monitoring?
Analysts rely on tools like Google Earth Pro, Sentinel Hub, and QGIS to detect terrain changes, unauthorized crossings, and smuggling corridors along borders.
How can law enforcement safely investigate the dark web?
Law enforcement can use isolated browsers like Silo to access the dark web safely, maintaining anonymity and compliance while gathering intelligence.
Tags Anonymous research Law enforcement OSINT research Social media

