Discover how GitHub’s vast code repositories and social features make it a valuable OSINT resource for uncovering sensitive data, technical insights, and developer networks.
GitHub is a cloud-based development platform that allows software developers to work together on projects around the world. Users can share code for open-source projects, compile resources, and create dev environments. The collaborative nature of the platform and the volume of repositories stored there makes it an important resource for open-source investigators to understand and learn.
How GitHub works
Before we look into GitHub's search features, it is important to differentiate between Git and GitHub. Git is the version control system that tracks code changes, while GitHub is the collaborative platform where developers use Git to collaborate on software projects.
The platform uses Git's distributed version control and adds features like access control, bug tracking, feature requests, task management, continuous integration and project wikis. These features help development teams in different locations update code in real-time and coordinate their work effectively.
As the largest online code repository, GitHub has a vast community of developers. Recent data shows that there are over 100 million active developers on the platform, with significant numbers based in the U.S., China and India. In 2022 alone, the platform saw more than 413 million open-source contributions, highlighting its importance as a central hub for collaborative software development.
Why is GitHub important for OSINT gatherers?
GitHub is a valuable data source that offers much more than just code. It serves as a place where human error, operational transparency, and technical research come together. This makes it an essential tool for today's OSINT investigators.
- A rich source for accidental data exposure — Developers commonly accidentally upload sensitive information to public repositories.
- Technical reconnaissance and target profiling — GitHub provides a deep look into a target's technical IT infrastructure, tools and competencies.
- For example, by analyzing a company's or an individual's GitHub repositories, OSINT gatherers can determine what programming languages, frameworks, databases and services they use.
- Historical analysis and change tracking — Every commit on GitHub is timestamped. This allows OSINT investigators to perform temporal analysis.
- Social intelligence and network mapping — GitHub is a social platform for developers. Analyzing social interactions can build a picture of relationships and collaborations.
While GitHub appears primarily as a development platform, it functions equally as a social media environment featuring:
- User profile accounts — Complete with profile pictures, display names, usernames, follower networks, biographical information and links to external platforms and personal websites.
- User collaborations — Platform capabilities include project collaboration, discussions and repository forking (copying project codebase for personal development), revealing significant relationship intelligence.
- Project networking — Users can follow repositories, subscribe to other users and monitor codebase changes.
GitHub search
GitHub's integrated search function provides the most straightforward investigation approach. Investigators can input relevant keywords or phrases, then apply filtering criteria to refine results. When investigating company-related repositories or mentions, using company names or domain names as search terms reveals their presence across the platform.
To access the GitHub search function, go to the main page (after logging in) https://github.com. You will see the search box located in the upper right side of the page (see Figure 1).
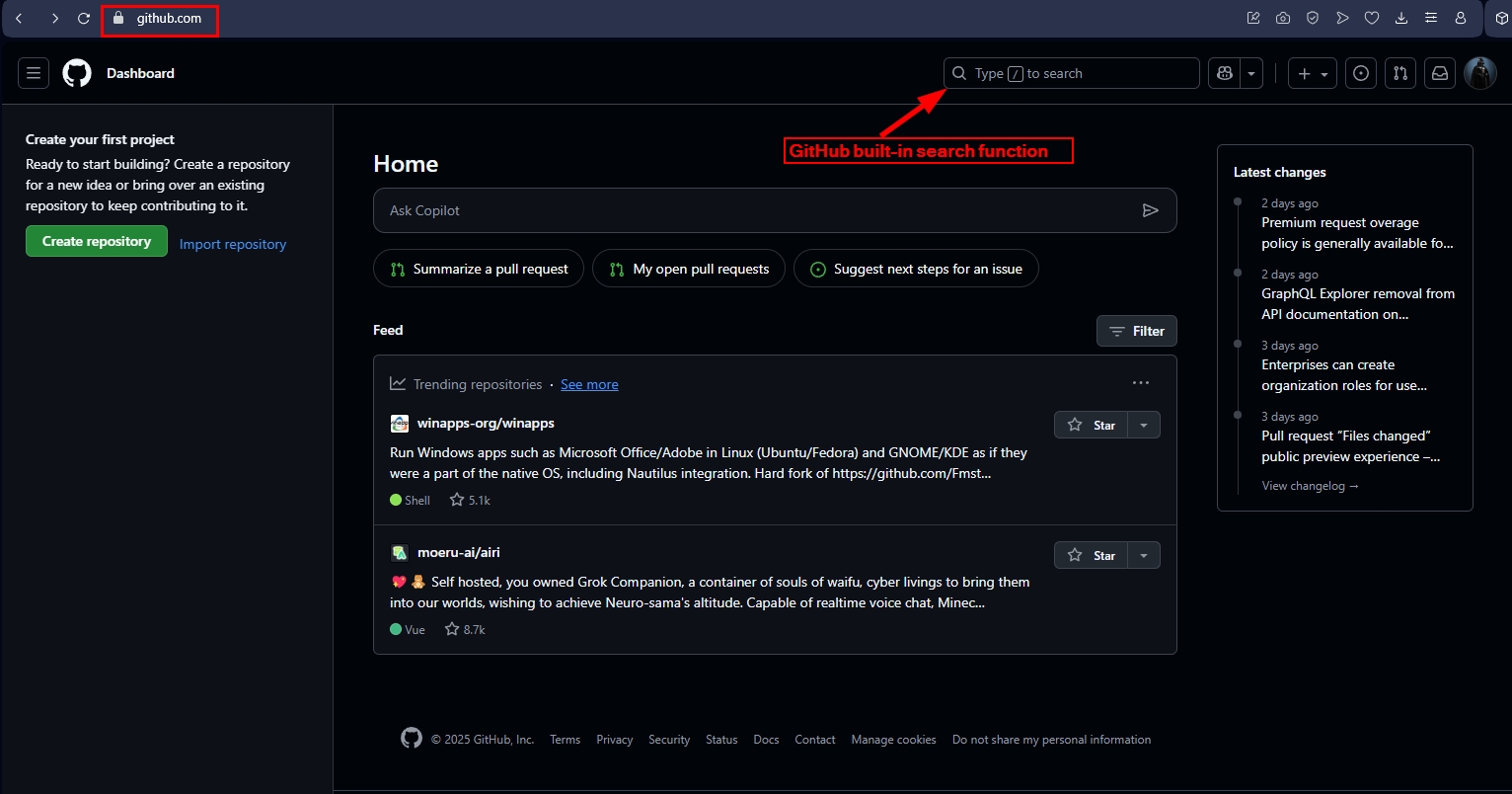
Figure 1 - GitHub search built-in function
Let us search for the keyword "OSINT", we can see from Figure 2 that GitHub organizes returned results according to different criteria:
- Code: Searches for specific strings and snippets within the actual source code files across all public repositories. This is one of the most powerful filters for finding code examples, vulnerabilities or accidentally exposed secrets.
- Repositories: Searches for entire code repositories based on their name, description, the content of the README file, and other metadata. Please note that it does not search the code within the files themselves (that's what the Code filter is for).
- Issues: Searches within GitHub Issues, which are used for bug reports, feature requests, and general project discussions. This is great for seeing if a particular bug has been reported or if a specific feature is being discussed.
- Pull requests: Searches within Pull Requests (PRs). A pull request is a proposal to change a codebase. This filter lets you find discussions about specific code changes, see how features were implemented, or find fixes for problems.
- Discussions: Searches within GitHub Discussions, a forum-like feature for projects (like Q&A, ideas, or announcements).
- Users: Searches for GitHub users by their username, full name or public bio. This is useful for finding developers who work with specific technologies or are part of certain organizations.
- Commits: Searches the messages that developers write when they save (commit) changes to the code. This is excellent for tracking the history of a specific change or fix.
- Packages: Searches for published packages on GitHub Packages. This is a registry for software packages (like npm, Maven, NuGet, etc.) that can be used as dependencies in other projects.
- Wikis: Search the content of wiki pages tied to GitHub repositories. People often use wikis for detailed documentation, tutorials and FAQs.
- Topics: Searches for repositories that have been tagged with a specific topic (a user-defined label like machine-learning or css-framework). This is a way to discover projects within a specific category.
- Marketplace: Search for apps and actions found on the GitHub Marketplace. These tools improve GitHub's functions, including CI/CD workflows, code quality checkers, and project management integrations.
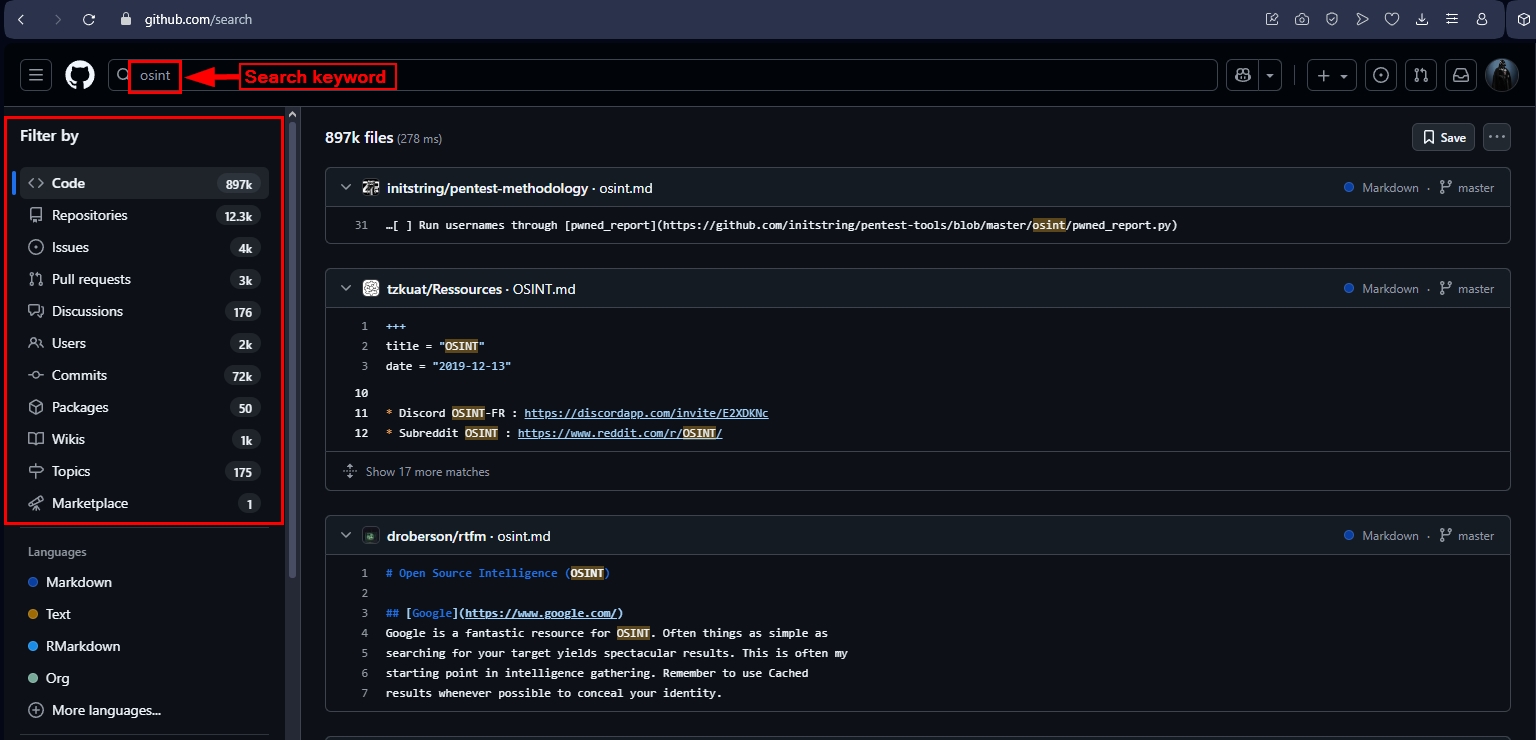
Figure 2 - GitHub allows filtering returned results according to different filters
We can also filter results according to code, repositories or issues written in a specific programming or markup language (see Figure 3). GitHub automatically detects the primary language of every repository and the language of individual code files. The language filter lets you use this metadata to narrow down our searches with extreme precision.
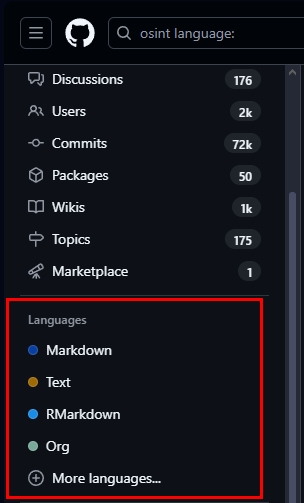
Figure 3 - Filter GitHub search results according to programming language used to create the code snippets, repositories or issues
The Path filter (see Figure 4) narrows your search results to only those files where the path and/or filename matches your query. For instance, it searches the entire path of a file, from the repository's root directory onwards. You can use it to find files in specific directories, files with specific names or a combination of both.
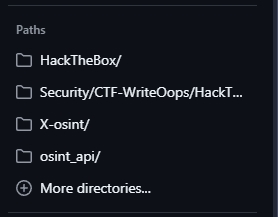
Figure 4 - Using the Paths filter in GitHub
The advanced section in Github search includes three filters:
- Owner: This filter limits your search to repositories owned by a specific user or organization. It is a direct way to explore all the public works of a particular person, company, or group.
- Symbol: This is an advanced, code-specific filter that allows you to search for symbol definitions within code. "Symbols" include:
- Function and method definitions (e.g., def my_function():, function calculateTotal())
- Class definitions (e.g., class UserModel:)
For instance, instead of searching for every occurrence of a word in the code (comments, variable uses, etc.), it helps you find where that function, class, or variable is defined initially.
- Exclude Archives (or is:archived): This checkbox lets you exclude repositories that have been archived. Archiving a repository on GitHub makes it read-only. No new issues, pull requests, or code changes can be made. This is often used for projects that are no longer maintained, are outdated, or have been completed.
GitHub advanced search
The advanced GitHub search can be accessed from the bottom left corner of the GitHub search page (see Figure 5), the direct link to it https://github.com/search/advanced
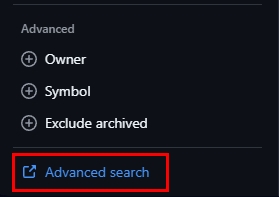
Figure 5 - Access GitHub advanced search
The advanced GitHub search page contains six sections. Here is a breakdown of each section and what filters it contains.
Advanced options (see Figure 6)
- From these owners: This filter limits your search to repositories owned by the specific users or organizations you list.
- In these repositories: This is one of the most precise filters. It narrows your search down to only the specific, full-named repositories you provide.
- Created on the dates: This filter finds repositories based on their creation date.
- Written in this language: This filter limits results to repositories whose primary language is the one you select.
A complete example would be:
From these owners: google, microsoft, netflix, airbnb
In these repositories: (Leave blank to search all repos from these owners)
Created on the dates: >2025-01-01
Written in this language: TypeScript
This search would translate to:
"Find repositories owned by Google, Microsoft, Netflix, or Airbnb that are primarily written in TypeScript, and have been created after January 1, 2025."
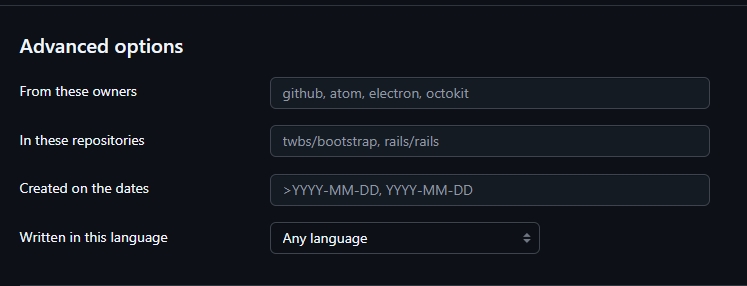
Figure 6 - Advanced options section
Repositories options (see Figure 7)
- With this many stars: Filters repositories by their star count (popularity metric). For example:
stars:>10000 - Find highly popular repositories with over 10,000 stars
stars:1..100 - Find repositories with moderate popularity (1-100 stars)
stars:0 - Find repositories with no stars (new or unpopular projects)
- With this many forks: Filters by fork count (indicates how many times the repository has been copied). For example:
forks:>1000 - Find repositories that are frequently forked (indicates active development/contribution)
forks:0 - Find original repositories that haven't been forked
forks:50..200 - Find moderately forked projects
- Of this size: Filters repositories by their total size in kilobytes. For example:
size:>100000 - Find large repositories (over 100MB)
size:<1000 - Find small repositories (under 1MB, useful for simple projects)
size:10000..50000 - Find medium-sized repositories (10-50MB)
- Pushed to: Filters by the last push date (when code was last updated). For example:
pushed:>2025-06-01 - Find recently active repositories (updated after June 2025)
pushed:<2022-01-01 - Find potentially abandoned repositories (no updates since 2022)
pushed:2025-01-01..2025-03-31 - Find repositories updated in Q1 2025
- With this license: Filters repositories by their software license type. For example:
license:mit - Find MIT-licensed projects
license:gpl-3.0 - Find GPL v3 projects
license:apache-2.0 - Find Apache-licensed projects
- Return repositories (fork options): Controls whether search results include forked repositories:
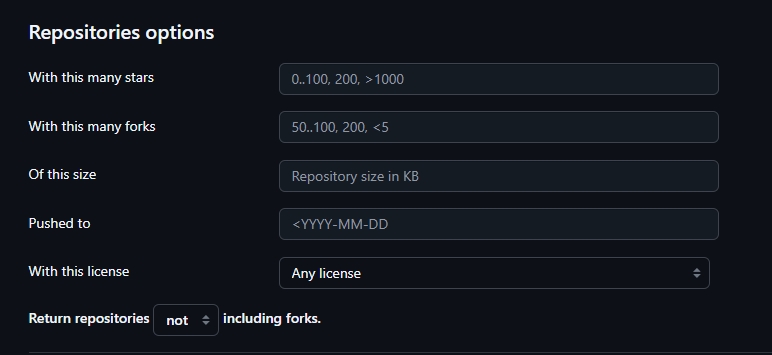
Figure 7 – GitHub advanced search page - Repositories options
Code options
- With this extension: Filters code files by their file extension, allowing you to search for specific file types. For example, extension:py or extension:js or extension:config
- In this path: Filters code by its location within the repository structure. For example:
path:config/ - Find files in configuration directories
path:src/ - Find files in source code directories
path:test/ - Find files in testing directories - With this file name: Searches for files with specific names, regardless of their location. For example,
filename:config.json - Find configuration files named config.json
filename:.env - Find environment variable files
filename:docker-compose.yml - Find Docker Compose files - Return code (fork options): Controls whether search results include code from forked repositories.
Issues options
- In the state: Filters GitHub issues by their current status. For example: state:open - Find currently unresolved issues | state:closed - Find resolved or completed issues
- With the reason: Filters closed issues by the specific reason they were closed. It has three options:
completed - Issues that were successfully resolved/implemented
not planned - Issues that were rejected or won't be addressed
reopened - Issues that were closed but later reopened - With this many comments: Filters issues by comment count. For example:
comments:>50 - Find highly discussed issues (controversial or complex topics)
comments:0 - Find issues with no community engagement
comments:1..5 - Find moderately discussed issues - With the labels: Filters issues by assigned labels/tags. Such as: label:bug or label:"help wanted" or label:security.
- Opened by the author: Filters issues created by specific users. For example: author:torvalds - Find issues opened by Linus Torvalds. We can also change the author name to become the company name to find issues opened by a specific company.
- Mentioning the users: Filters issues that mention specific users using @username.
- Assigned to the users: Filters issues assigned to specific users for resolution.
- Updated before the date: Filters issues by their last update timestamp. For example:
updated:<2023-01-01 - Find stale issues (potentially abandoned)
updated:>2025-08-01 - Find recently active issues
updated:2025-01-01..2025-03-31 - Find issues active in Q1 2025
Users options
- With this full name: Filters users by their display name (not username). For example: fullname:"Grace Hopper" - Find users with this exact display name.
- From this location: Filters users by their self-reported location in their profile. For example: location:"San Francisco, CA" or location:London.
- With this many followers: Filters users by their follower count (influence/popularity metric). For example:
followers:>1000 - Find influential developers with large followings
followers:0 - Find new or inactive users with no followers
followers:10..100 - Find moderately followed users
followers:>10000 - Find highly influential tech personalities - With this many public repositories: Filters users by the number of public repositories they maintain. For example:
repos:0 - Find users with no public repositories
repos:>100 - Find highly productive developers
repos:1..5 - Find casual developers or beginners
repos:<3 - Find users with minimal public activity - Working in this language: Filters users by their primary programming language (based on repository analysis). For example: language:Python or language:JavaScript
Wiki options
- Updated before the date: Filters GitHub wiki pages by their last modification timestamp. For example:
updated:<2023-01-01 - Find outdated wiki pages (potentially containing obsolete information)
updated:>2025-08-01 - Find recently updated documentation
updated:2025-01-01..2025-03-31 - Find wikis updated in Q1 2025
updated:<2022-01-01 - Find very stale documentation (possibly abandoned projects)
Inspecting GitHub user profile
GitHub profiles can provide useful information. The amount of information varies for each user, but many developers share more than just their code. Profiles often contain details like names, locations, affiliations, and links to personal websites or other social media accounts. In addition to the profile page, repositories, contribution history and starred projects can show technical skills, areas of interest, professional networks and even time zones or activity patterns. Altogether, this makes GitHub a good place for collecting both direct and indirect insights about a user.
Inspect username
The first thing we need to inspect is the username. GitHub username is unique across the platform and it appears in the profile URL in addition to appearing under the profile picture (see Figure 8).
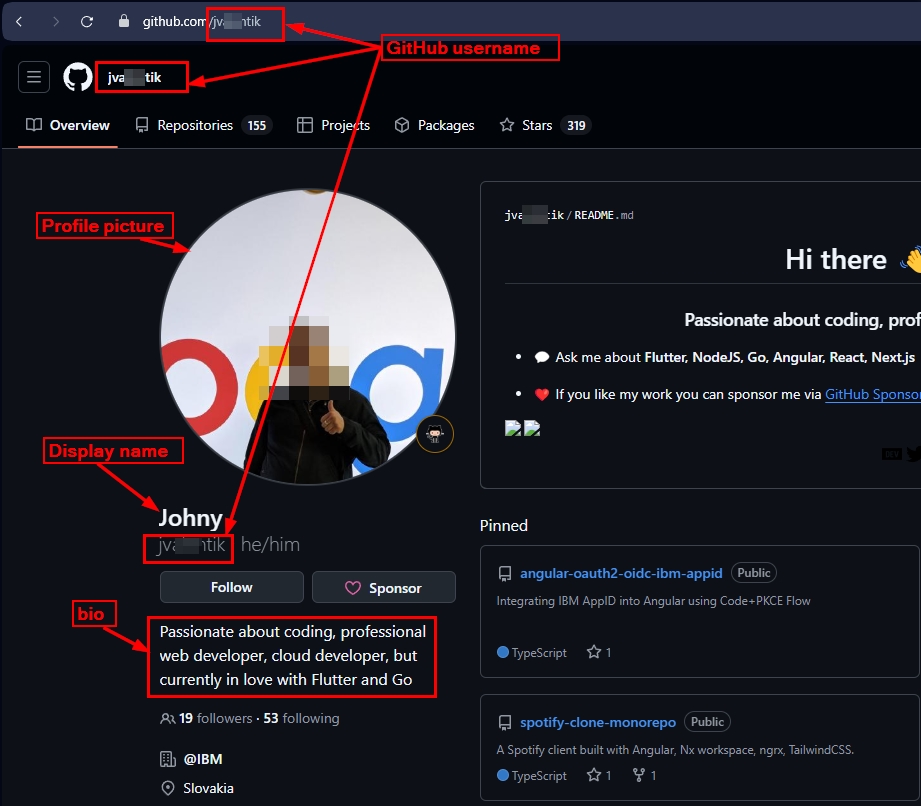
Figure 8 - GitHub username is unique and appears in the target user profile URL
Many people prefer to use the same username across different social media platforms, and GitHub is no exception. We should conduct a reverse username search to see where the same username appears, which allows OSINT gatherers to discover linked social media accounts. Here are some services for executing a reverse username search:
Inspect GitHub display name
Similar to other social media platforms, GitHub allows users to set a display name, which could be either a professional alias or the real name of the account holder. Display names are often reused across multiple platforms online, so conducting a comprehensive search can reveal additional leads about the target GitHub user's digital footprint.
- Here are some Google dorks to search for GitHub display name online:
- "[Display Name]" -site:github.com
- "[Display Name]" site:linkedin.com
- "[Display Name]" site:x.com
- "[Display Name]" site:reddit.com
- "[Display Name]" + "developer" OR "programmer" OR "engineer"
- "[Display Name]" + "portfolio" OR "resume" OR "CV"
- "[Display Name]" + "contact" OR "email" OR "hire me"
- "[Display Name]" + "[Programming Language]" (e.g., Python, JavaScript)
- "[Display Name]" filetype:pdf
- "[Display Name]" + "conference" OR "speaking" OR "presentation"
- "[Display Name]" + "@" (to find email patterns)
Profile picture
GitHub profile pictures may contain a personal photo of the account holder or an avatar. When the profile image contains a personal photograph, we should conduct reverse image searches to discover where this photo appears elsewhere online. Here are the primary reverse image search engines:
User Bio/Description
GitHub user bio contains different information about the user, such as personal or professional summary, job titles and interests. Some GitHub bios are long and they contain other information such as:
- Gender
- Professional Title/Role — e.g., "Senior DevOps Engineer at @CompanyX", "Security Researcher", "ML Engineer".
- Skills and technologies — Users often list their tech stack, e.g., "Python | Go | Rust | Kubernetes".
- Interests and focus areas — e.g., "Open Source Enthusiast", "Contributing to privacy-focused tools"
- @" Mentions of organizations — If a user puts "Dev at @AcmeCorp", clicking that link takes you to the company's GitHub page. This confirms employment and allows you to see the company's other employees and projects.
Company
Current employer or organization affiliation.
Location
Geographic information (city, country, timezone implications).
Website/Blog Links
External domains for expanded investigation. For each personal website, we should inspect the following:
- Whois information of the domain name. Here is a list of online services to find WHOIS information of domain names https://osint.link/technical-footprinting/#whois
- Hosting provider name. Use hostingchecker to know the name of the hosting provider of the website.
- Subdomain discovery – To find other parts of the website that are not linked to the front page. To find all subdomain names of a website, type site:target.com -inurl:www and Google will show all related subdomain names of the target. Example:site:yahoo.com -inurl:www. There are also automated tools to find subdomain names such as DNSdumpster and Virus Total.
- Manual review of the website content, for example, reading the "About us" and "contact us" pages.
- View pages source code to reveal HTML comments, technology stack, and metadata tags that may reveal developer names.
- Check the Wayback Machine at archive.org. See how the site has evolved over time. Old versions might have information that has since been removed.
Email address
Contact information (if public). If there is an email address listed, then we should do the following:
Use Google dorks to find where this email appears online.
- "target@example.com" (filetype:pdf OR filetype:doc OR filetype:docx)
- "target@example.com" site:github.com OR site:gitlab.com OR site:bitbucket.org
- intitle:"index of" target@example.com
- site:linkedin.com "target@example.com" OR site:x.com "target@example.com" OR site:facebook.com target@example.com
To find out which services a target email address has used, check its exposure in past data breaches. This means searching databases of compromised accounts, which can show previous associations and online behavior linked to the email.
Here is a list of data leaks websites: https://osint.link/#leak
Link to other social media profiles
Such as Twitter (X). LinkedIn and Mastodon to name only a few (see Figure 9).
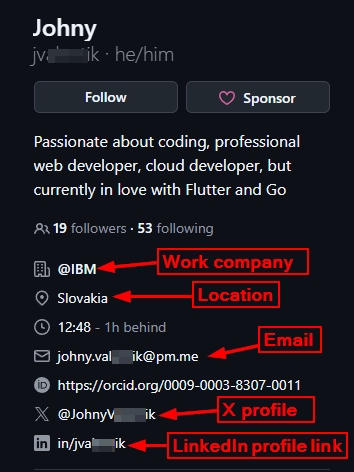
Figure 9 - GitHub user profile may display important information about user
Followers & following count
The GitHub profile page displays follower and following counts that provide direct access to all GitHub users who follow or are followed by the target user. This social network data can reveal valuable intelligence about the user's professional connections and community involvement.
- Company identification - Multiple followers from the same organization may indicate the target's employer.
- Project collaboration - Mutual following relationships often indicate collaboration.
- Geographic clustering - Followers concentrated in specific regions may reveal location.
- Skill assessment - Following patterns can indicate technical interests and expertise areas.
GitHub contribution activity
This section on the GitHub profile page contains a comprehensive chronology of the user's events and activities on GitHub since account creation. By inspecting the contribution activity, we can analyze the types of activities a GitHub user has been involved in throughout their entire account history. To access historical data, simply click on the year displayed on the right side to view that year's specific activities (See Figure 10).
Types of contribution data available
Repository activity
- Commits to repositories (public and private)
- Pull requests created and merged
- Issues opened and commented on
- Repository creation and forking activity
Collaboration patterns
- Contributions to other users' repositories
- Participation in open source projects
- Code review activities
- Discussion participation
Activity timeline analysis
- Account creation date and early activity patterns
- Periods of high/low activity (this may indicate employment changes)
- Consistent contribution schedules (this could reveal work hours, days off)
- Seasonal patterns or gaps in activity
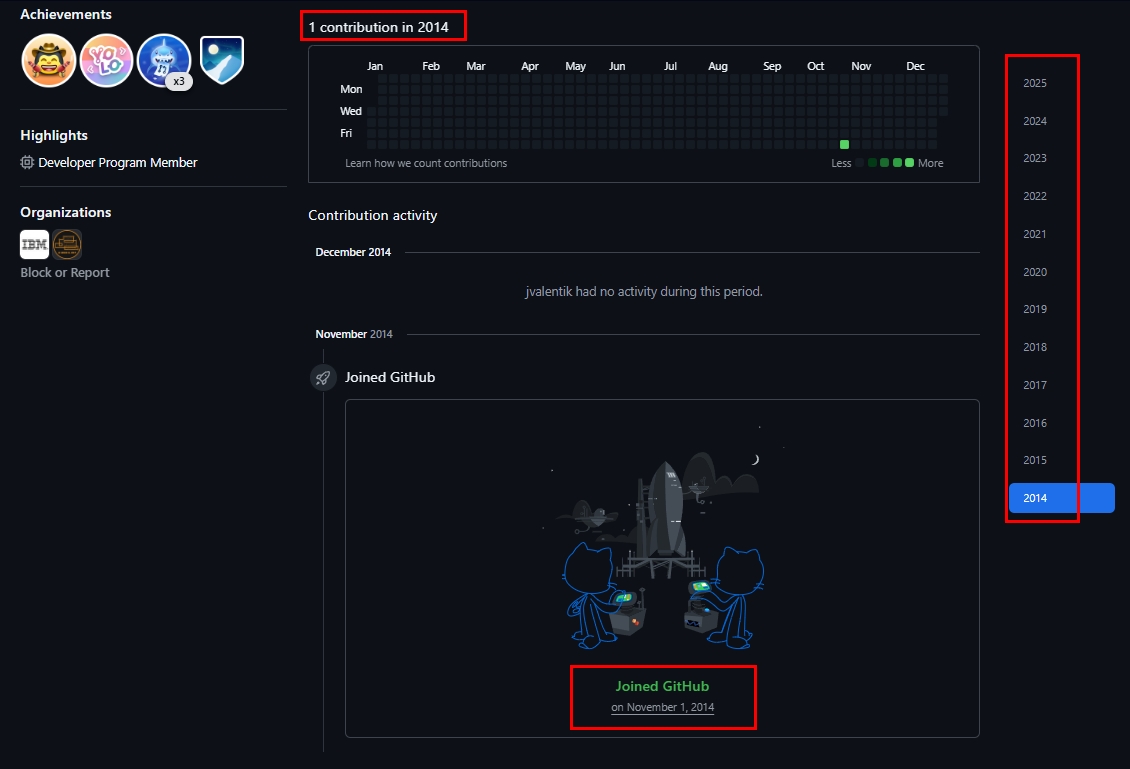
Figure 10 - GitHub contribution activity analysis
GitHub tools
Many GitHub tools facilitate navigating through its contents. Here are the most prominent ones:
- Gitrob – This is a tool that helps you find potentially sensitive files stored in public repositories on GitHub. Gitrob will clone repositories owned by a user or organization to a set depth. It will go through the commit history and flag files that fit the signatures of potentially sensitive files. The results will be shown through a web interface for easy browsing and review.
- TruffleHog – Find leaked credentials on GitHub.
- GitDorker - This is a tool that utilizes the GitHub Search API and an extensive list of GitHub dorks to provide an overview of sensitive information stored on GitHub given a search query.
- GistSearch - Search for code snippets and text files in GitHub's Gist platform.
- GitHub Recon – A tool that automates the process of reconnoitering GitHub repositories.
GitHub is a treasure trove of information for OSINT investigators, going well beyond just code repositories. The platform has social features, user profiles, and activity tracking that create a rich environment for gathering intelligence. By using GitHub's built-in search tools alongside external applications and techniques for connecting data from different platforms, investigators can create detailed profiles of targets, map professional networks, and find digital traces online.
Tags OSINT research

