The number of social media users is growing steadily every day. Datareportal predicts there are over five billion social media users worldwide. This means roughly more than 90% of internet users are on one or more social media services.
There are scores of social media platforms worldwide. Some specialize in video content, such as YouTube and TikTok, while others focus on image sharing like Instagram, or a mix of both with text content, such as Facebook and X (Twitter).
People post all sorts of information to social media platforms. This includes vacation photos and videos, interactions with friends and work colleagues, and personal details like mailing addresses, email, phone numbers, and the places they regularly visit, including their work locations. A user posting vacation photos with geotags can reveal their home is empty. Check-ins at specific locations establish regular patterns of movement that investigators can map and analyze.
While not all social media platforms are equally important in relation to their number of users, from an OSINT perspective, any social media platform is considered vital because it can provide critical information to support an investigation case. Smaller platforms are particularly valuable because users commonly share content there that they have deleted or never posted elsewhere.
In this guide, we are going to investigate the Bluesky platform. While Bluesky's user base is around 30 million, it is witnessing steady growth, especially after the last US election, when millions of users opted to use this platform instead of Twitter (X) because of their opposition to the strong relations between President Trump and X's owner, Elon Musk.
What is the Bluesky platform?
Bluesky is a microblogging social media platform similar to Twitter (X). Initially launched in 2023, the platform required an invitation to register during its early phase. However, since February 2024, anyone can register without an invitation.
Bluesky is built on top of the AT Protocol. This is an open-source social media framework for building federated social media platforms. It allows users to move their identity and data with them if they opt to leave the platform and move to another supported open source platform. This means a Bluesky user's posts and connections could be traced even if they migrate to another AT Protocol platform, which has implications for long-term investigations.
Investigating Bluesky accounts
As we already said, the Bluesky user interface resembles the X platform. However, the platform differs significantly in being a decentralized network, unlike Twitter, which is controlled by a central authority.
Bluesky gives users more control over their usage experience. For instance, users can create custom feeds based on specific topics, keywords, or user lists. Unlike algorithmic feeds that most platforms force on you, Bluesky lets you choose what you see and in what order.
The platform also introduced "domain handles" to support username naming convention. Instead of a standard username, users can verify their identity on Bluesky using their own domain name. For example, a journalist working for CNN.com could use @journalist.CNN.com as their handle. This adds a layer of authenticity that is harder to impersonate, which matters when we are trying to verify sources during investigations.
Bluesky supports threading, reposts (similar to retweets), likes, and direct messages. Users can also attach images, videos, and links to their posts.
Bluesky account identifiers
Similar to other social media platforms, two identifiers distinguish a Bluesky account, which are: Username or handle and Display Name.
Username
Bluesky username is a unique identifier across the Bluesky platform. It is the one used by other users to mention, find and follow your account.
What makes Bluesky's username different from other platforms is that it is treated like a web domain name. This offer users two naming ways:
- The default handle or format: This is the default format when you register for a Bluesky account. It has the following format: "@yourusername.bsky.social". For example: @darknessgate.bsky.social , where the first part "darknessagte" is the unique username selected by the user and the second part is the .bsky.social , this default suffix essentially makes your profile a subdomain of bsky.social.
- Custom domain name handle: An interesting feature of Bluesky is allowing users to use a custom domain name they own as their handle. For example: darknessagte.osint.link, where darknessagte is the username and OSINT.link is the custom handle I own. A custom domain name is commonly used by brands, organizations, and public figures.
It is worth noting that a Bluesky user may use the same username across different platforms, for example, using the Bluesky handle on Facebook, Twitter (X) and Reddit. To discover other social media platforms where a particular Bluesky handle is used, we can use any of the following services:
- Whatsmyname
- Sherlock - A tool for searching social media accounts by username across 400+ social networks
- More username reverse search engines and tools can be found here.
It is important to know that Bluesky usernames can be changed later without losing account information like followers, following count, likes, and shares. This means it is not reliable to identify a user based only on their Bluesky username. However, there is another detail tied to each Bluesky account that remains the same since the account was created: the decentralized identifier or DID.
Understanding DIDs in Bluesky
Every Bluesky account receives a permanent DID upon creation. This identifier remains with the account forever, no matter how many times the username changes. You can think of it as a social security number for the account, unique and unchanging.
The DID format looks like this: did:plc:random_string_of_characters. For example, my Bluesky account DID is: did:plc:436v3w5t4qntdjnhyacdobfa.
The DID of a Bluesky account is unique and should be the first piece of information that is documented by OSINT gatherers when collecting information about a target Bluesky account.
You can fetch the DID of any Bluesky account using two methods:
- The first one is manual and requires inspecting the account HTML page source code.
- The second is easy and relies on a third-party service to retrieve the DID code after supplying the target Bluesky username.
Here are two free online services for retrieving Bluesky account DID:
- Ilo.so (see Figure 1)
- Bluesky DID Lookup
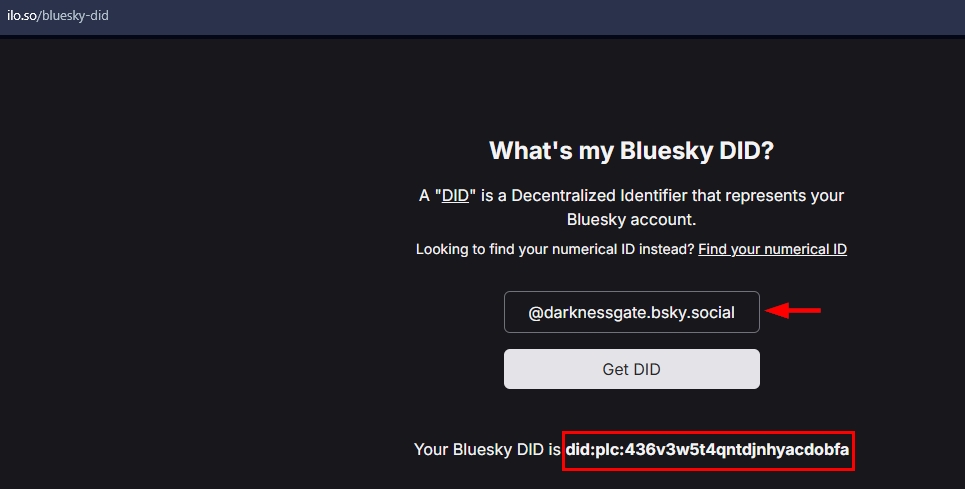
Figure 1 - Retrieving Bluesky DID using a third-party service
Bluesky display name
Bluesky's Display Name is the name that appears at the top of a user's profile, typically in a larger font (see Figure 2). Unlike the handle, the Display Name is not unique across the platform and can be changed as the user wants. It is generally used as a friendly, human-readable name for the account, such as a person's real name (first and last name), a business name, or a creative nickname.
Since the Display Name is often the user's real name or a common alias, an investigator can use it to search for other profiles on different social media platforms. For instance, if a target's Display Name is "John Smith," an investigator can search for "John Smith" on other sites (X, Facebook, Instagram, etc.) to look for profiles with a similar name, profile picture, or bio, helping to link the Bluesky account to other online presences. Here are some Google dorks to find where a particular Display Name exists online:
- "John Smith" (site:facebook.com OR site:twitter.com OR site:instagram.com OR site:linkedin.com)
- "John Smith" inurl:profile -site:bsky.app
- "John Smith" (site:github.com OR site:reddit.com OR site:medium.com OR site:youtube.com)
- "John Smith" (site:tiktok.com OR site:pinterest.com OR site:flickr.com OR site:vimeo.com)
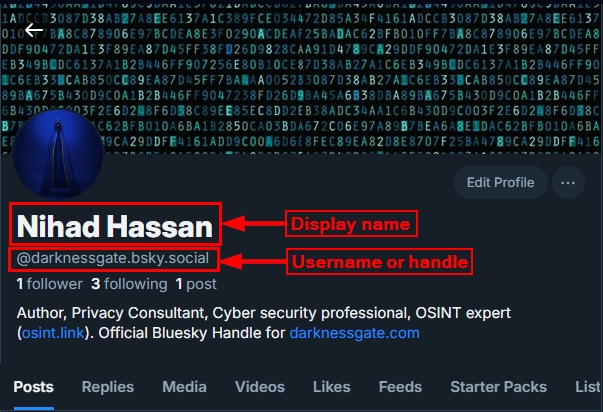
Figure 2 - The Bluesky display name and username
The Bluesky Display Name may also have special meaning in other civilizations or cultures that can help us in our investigation. Here are some online services that reveal name meaning:
Account join date
Unlike X, Bluesky does not display the account join date in the profile page. To retrieve the account, join date of any Bluesky user, follow these steps:
- Visit the target Bluesky profile page
- Open browser developer tools (Ctrl+Shift+I)
- Select the Network tab, insert the following "getProfile" in the filter box
- Refresh the page to capture network requests
- Click on any of the loaded requests, then examine its attributes in the "Response" tab
- Locate the "createdAt" timestamp to see the Bluesky account join date (see Figure 3)
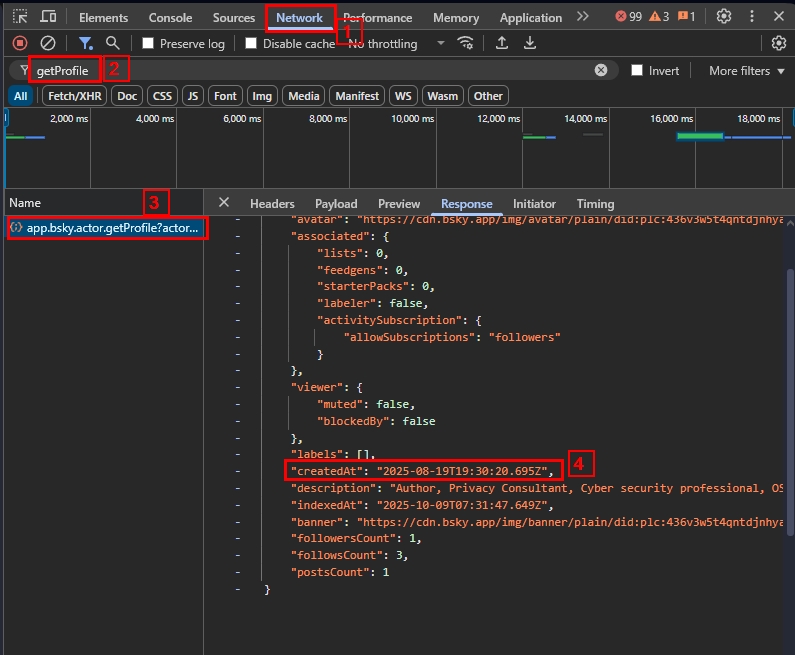
Figure 3 - Retrieve account Join date
The retrieved date/time appears in ISO 8601 format. To convert it into something readable by humans, use the following service:
- Timestamp-converter (see Figure 4)
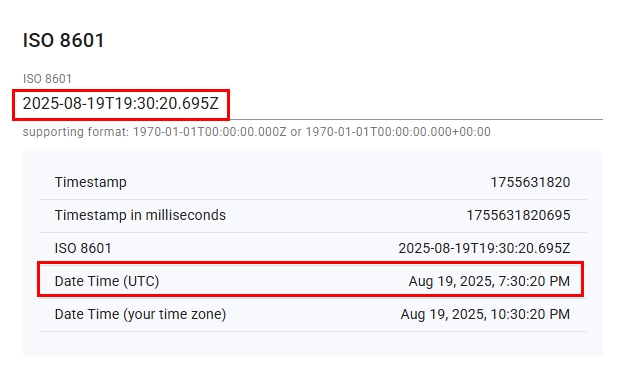
Figure 4 - Convert ISO 8601 time to a readable format
Bluesky profile and header images
Analyzing Bluesky profile and header images can reveal important information, such as:
Metadata (EXIF and hidden data)
If Bluesky has not compressed the uploaded images, then they can still contain valuable metadata information such as:
- EXIF data: GPS coordinates, capturing device model, camera type, and photo date/time.
- Software tags: Editing software or filters used (e.g., Photoshop).
- Original file names: Sometimes indicative of personal naming habits or organization systems.
Here are some tools for inspecting EXIF metadata in images and videos:
If metadata is stripped, you can use reverse image search tools to find earlier versions that may still contain it (e.g., uploaded elsewhere before Bluesky). Here are some reverse image search engines:
Visual clues from the profile image
The profile photo could show details about identity and lifestyle.
- Facial recognition can be done by cross-matching on other platforms through reverse image search.
- If the profile image contains a person wearing a uniforms, badges, or contains logos, it could reveal job roles, affiliations, or group memberships.
- The environment can include visible landmarks, weather, plants, or buildings that suggest a geographic area.
- Objects in the background, such as vehicles, computers, books, or decorations, can indicate business occupation, income level, or interests.
- Lighting and the time of day, along with time zone hints, can help estimate location or posting habits.
Header (Banner) image analysis
Header images commonly reflect personality, affiliations, or location.
- Landscapes or landmarks are useful for geolocation. You can find skylines, mountains, or beaches through Google Earth or Mapillary.
- Event photography can highlight specific events or conferences.
- Symbolic images like flags, logos, or quotes may show political, cultural, or ideological preferences.
- Color schemes and styles sometimes match branding used by the same person elsewhere, such as the same header on LinkedIn or X.
Profile bio
From an OSINT perspective, a Bluesky bio—though it is somehow short—can reveal a wealth of information about a user's identity, location, affiliations, and online footprint when analyzed systematically.
Identity indicators
The bio may contain elements that confirm someone's identity, such as:
- Full name, nickname, or alias.
- Professional title or role such as ("Security researcher," "Journalist," "PhD Candidate").
- Education references, such as mentions of universities, research institutions, or training programs.
Location
The bio may contain a hint to the user geographical location, such as:
- Explicit mentions of a city, country, or region (e.g., "Berlin-based," "from Nairobi").
- Implicit indicators like local slang, time zone patterns, or mentions of events or cultural references are unique to a specific location.
- Emoji clues like flags or city icons, which could refer to home country or current residence.
Communities
The bio could contain clues to current employer or affiliated communities, such as:
- Organizational links that point to employers, startups, NGOs, or media outlets.
- Hashtags or acronyms like (#infosec, #greenpeace, #OSINT), which identify professional or ideological communities.
Contact information
The bio may contain links to other social media profiles, such as LinkedIn or Reddit, and may also include email addresses or links to a personal blog or website. For each domain found in the bio, we should do the following:
- Check previous versions of the website using the Wayback Machine to see how the site evolved and what information might have been removed.
- Check website IP addresses to identify hosting providers and potential server locations. You can also use third-party services to discover the organization hosting the website, such as Hostingchecker.
- Check domain name WHOIS records to find registration details, registrant information, and historical ownership data. Here are some services for fetching WHOIS records of any domain: https://osint.link/technical-footprinting/#whois
- Perform reverse WHOIS lookups to discover other domains registered by the same person or organization.
The websites themselves should be inspected thoroughly to discover information that can open new leads in our investigations. Look for:
- Email addresses in contact forms, footers, or embedded in page source code
- People's names in team pages, author bylines, or comment sections
- Physical addresses in contact pages or legal disclaimers
- Phone numbers listed for business or personal contact
- Files stored on the website (PDFs, images, documents) that can reveal metadata information such as author names, creation dates, software used, and geolocation data
- Social media widgets or embedded feeds that link to additional profiles
- Code comments in the page source that might contain developer names or internal notes
Searching on Bluesky
The Bluesky search box is located in the upper right corner of the Bluesky interface (I'm using the web version of the application). To start your search, look at the following tips:
- To search for a specific phrase, use quotes "“ around keywords, for example: "OSINT resources". The returned results will also include posts that contain images with the phrase in its ALT attribute.
- To search for posts that contain a specific hashtag, use the # symbol. For example: #OSINT will return all posts that contain the #OSINT hashtag.
- To find posts that mention a specific user, search using their handle. For example: @darknessgate.bsky.social will return all posts that include this Bluesky handle. We can also use the mentions search operator to return all posts mentioning a specific user. for example: mentions:darknessgate.bsky.social
- To find posts from a specific user, use the from operator. For example: from:darknessgate.bsky.social This will show all posts from user "darknessgate"
- To find a specific URL, use the domain operator. For example: domain:osint.link will return all posts that include the URL osint.link (see Figure 5)
- To find posts in a specific language, use the lang operator. Please note you should include the language code to specify it. For example: lang:ar OSINT This will search for posts containing OSINT keyword in the Arabic language only. To see a list of language codes, check Wikipedia , column named Set 1.
- To find posts within a specific timeframe, use the since and until search operators with the following date format: YYYY-MM-DD. The date/time should be formatted using the UTC date. Here is a time converter to convert from any date/time format into UTC | utctime. For example: OSINT since:2025-01-01 until:2025-10-01 | This will find posts with the keyword "OSINT" between January 1, 2025, and October 1, 2025.
- We can combine more than one search operators in one search query. For example: OSINT since:2025-01-01 until:2025-10-01 lang:ar This will return posts with the keyword "OSINT" between January 1, 2025, and October 1, 2025, which is written in Arabic language only.
It is worth mentioning that users can search Bluesky even without logging into the platform. This ensures privacy for OSINT gatherers and allows reconnaissance without creating an account that could be traced back to the investigator.
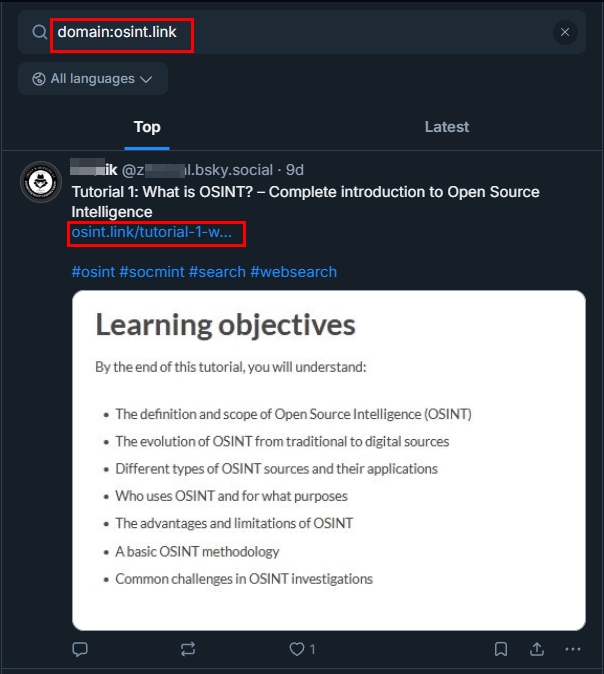
Figure 5 - Use the domain search operator to find all posts containing a specific URL
Using Google dorks to search within Bluesky
Google dorking allows OSINT gatherers to use advanced search operators combined with the site:bsky.app operator to narrow down their search results. This technique leverages Google's indexing of Bluesky's public content to find specific information without relying on Bluesky's native search functionality. Here are some examples:
- site:bsky.app intext:"OSINT tool" | Finds posts where users are discussing, or sharing information about specific OSINT tools or techniques.
- site:bsky.app inurl:profile intext:"engineer" | Finds profiles whose visible bio or page text includes "engineer."
- site:bsky.app inurl:profile intext:"linkedin.com" OR intext:"linktr.ee" OR intext:"github.com" | Find profiles linking LinkedIn , GitHub or personal sites.
- site:bsky.app inurl:profile intext:"hiring" OR intext:"looking for" | Identifies users posting about job opportunities or recruitment.
- site:bsky.app inurl:companyname "phishing" | Searches for posts on Bluesky that link to a specific company's custom handle or domain, looking for the word "phishing" to track active social engineering campaigns against that organization.
- site:bsky.app "threat actor" OR "APT group" "Malware analysis" | Looks for discussions among cybersecurity researchers about specific "threat actor" groups (like an APT group) or shared research on "Malware analysis."
Google indexing of Bluesky is not immediate. Recent posts might take hours or even days to show up in search results. For real-time monitoring, use Google dorking along with direct searches on the platform.
Bluesky represents a growing part of the social media landscape that OSINT practitioners cannot ignore. Its open structure and decentralized nature make it accessible for investigators but challenging to monitor completely. The platform's unique features, especially the permanent DID system and custom domain handles, require investigators to change their methods beyond traditional username tracking.
As Bluesky continues to draw users looking for alternatives to established platforms, expect to see more subjects of interest active there. The techniques outlined in this guide provide a foundation for methodical investigation. However, keep in mind that social media OSINT is always changing. Platform features evolve, user behaviors shift, and new tools regularly appear. Stay updated, document your methods, and always verify findings from multiple sources.
Tags Anonymous research OSINT research Social media

