Open-source intelligence (OSINT) helps corporate security teams identify threats, expose vulnerabilities, and disrupt attacks before damage occurs.
In today's digital landscape, organizations maintain extensive online footprints. From cloud infrastructure to social media profiles, technology underpins nearly every business function. This digital transformation delivers competitive advantages, operational efficiencies, and improved customer satisfaction. However, it simultaneously expands the attack surface available to threat actors.
Open-source intelligence (OSINT) is the practice of collecting and analyzing information from publicly available sources. Developed initially within government intelligence agencies and other public sector entities, OSINT has evolved into a critical corporate security capability following the proliferation of internet technologies and widespread digital transformation worldwide. Beyond enhancing security posture, OSINT enables organizations to gain competitive intelligence, monitor brand reputation, and research new markets before entry.
This article explores practical use cases where OSINT strengthens corporate security defenses. However, before we start, let us discuss why OSINT has become critical for corporate security.
Why is OSINT important for corporate security?
OSINT is critical to corporate security because threat actors rely on publicly available information during reconnaissance. Job postings, employee social media, domain records, and leaked credentials reveal infrastructure details, security gaps, and human vulnerabilities.
For example, threat actors can exploit the following areas to collect intelligence about any target organization that helps them in planning their attacks:
- Digital footprint exposure: Job postings on vacancy websites reveal network infrastructure, technology stacks, and organizational structure. For example, by checking LinkedIn job posts, we can reveal the type of IT infrastructure used by a company (see Figure 1).
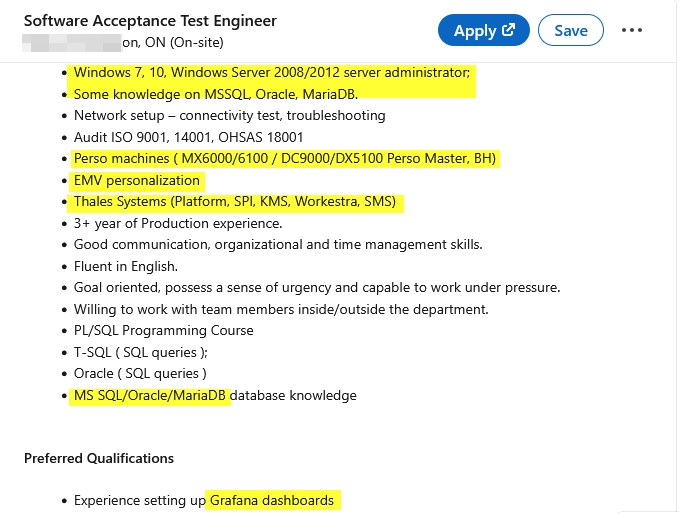
Figure 1 - A LinkedIn job post can reveal important information about IT systems used in the target company
- Social engineering vectors: Threat actors scan employee social media profiles on platforms like Facebook, X, and Instagram to gather personal details, such as the names of family members, friends, and colleagues, which they then use to craft convincing spear phishing emails impersonating those contacts.
- Vulnerability identification: Threat actors search public databases, hacker discussion forums, and Discord/Telegram channels to find exposed credentials, misconfigured services, and outdated software. Such information is exploited to provide direct pathways for initial access.
Threat actors leverage OSINT during attack reconnaissance phases. Organizations must adopt the same techniques defensively to identify and remediate security gaps before hackers exploit them.
Turn OSINT into a defensive advantage. Enter the threat environment with Silo, the unified workspace that lets corporate security teams safely access, investigate, and act on OSINT in real time — all without exposing identities or infrastructure. Launch your first investigation. |
Key OSINT applications for corporate security
Organizations can deploy OSINT across multiple security functions to reduce risk and improve defensive capabilities. The following section details specific use cases where OSINT delivers measurable security improvements for organizations.
Physical security and executive protection
OSINT allows organizations to move physical security from being a reactive, on-premise function to a proactive, intelligence-driven one. For instance, OSINT helps achieve physical security in different ways, including the protection of top management, event security, and the protection of corporate physical facilities.
Protection of top management
OSINT helps security teams ensure the security of the organization's top management by monitoring social media platforms, blogs, and forums for direct threats, doxing (posting home addresses or family details), or discussions of their travel schedule.
For example, the security team may discover a post by a disgruntled employee on a Telegram channel or a Facebook post that says, "The CEO is always unprotected when he takes his dog for a walk in Central Park at 7 AM."
OSINT monitoring can get this piece of information, and the executive protection team informs the CEO and adjusts the security detail's schedule accordingly.
Event security
Corporations conduct different public events each year, such as shareholder meetings, product launches, or opening a new office or branch. The OSINT team can map the digital chatter to identify planned protests, disruptions, or potential threats targeting the event location.
For example, an environmental activist group uses a public Facebook event to organize a protest at a company's manufacturing plant. The OSINT team can collect information about planned group activities and potential arrival time, which allows for safe and managed crowd control.
Protection of corporate physical facilities
OSINT provides the earliest signs of organized, large-scale threats that impact the physical facilities of corporations. For instance, by monitoring keywords, hashtags, and group chatter on social platforms (like X, Telegram, and local forums), security teams can detect planned protests, demonstrations, or employee strikes near a corporate facility's location. Monitoring news outlets can also reveal threats such as political instability, civil unrest, or rising crime rates around the corporation's facilities in a specific country or city.
Loss prevention
In the loss prevention area, OSINT can help corporations combat theft, fraud, and organized retail crime (ORC) by understanding the adversary's tactics and revealing their sales channels.
For example, OSINT can be used to link online aliases, marketplace vendor accounts, and social media profiles to map out entire organized retail crime rings. They can identify the thieves, the merchants who sell the goods, and the leaders.
OSINT can also be used to discover theft tactics used by cybercriminals. For instance, darknet forums and encrypted apps like Telegram are commonly used as hubs for sharing "how-to" guides on defeating security tags, such as breaking Windows or MS Office activation mechanisms, to use the software products illegally without paying for them.
By understanding the theft tactics used by hackers, corporations can tighten their security defenses and prevent such methods from becoming widespread and causing more damage to company profits.
Brand protection and digital impersonation detection
OSINT can play an important role in protecting a corporation's brand. For instance, the majority of advertising is now done on social media platforms, and monitoring these outlets has become very important to detect any disinformation campaign or other attempts to damage a company's reputation.
For instance, OSINT can be used to:
- Find counterfeit goods: OSINT teams can use automated tools to scan e-commerce sites and social media for counterfeit products using the company's logos and branding. This protects revenue and prevents customers from having poor experiences with dangerous fakes.
- Take down phishing sites and impersonation attempts: OSINT helps identify domains and social media accounts that impersonate the brand to steal customer credentials, such as your-bank-login.com instead of your-bank.com. OSINT can also be used to provide the evidence needed to file takedown requests with domain registrars and hosting providers.
- Monitor for brand misuse: OSINT helps organizations identify unauthorized use of their brand name and logo across the internet. Threat actors and fraudulent entities frequently exploit trusted brand names to deceive customers, damage reputation, and generate illegitimate revenue.
Proactive fraud detection
Fraudulent activities are continually evolving, and traditional fraud detection schemes that rely on customer reports, transaction monitoring, and post-incident forensics provide limited visibility into emerging threats until damage occurs.
OSINT transforms fraud prevention from reactive to proactive by monitoring publicly accessible information where fraudsters plan, coordinate, and execute their operations. By analyzing digital traces across forums, social media, underground marketplaces, and domain infrastructure, security teams can identify fraud schemes during early stages before widespread customer impact.
OSINT can help combat fraudulent activities in several ways.
Detecting brand impersonation
OSINT allows spotting and identifying entities that illegally use your company's brand name to deceive customers and business partners. This can be done via:
- Spotting fraudulent domains: Monitoring newly registered domain names that closely resemble your company's legal domain (this tactic is also known as typosquatting).
- Monitoring social media: Identifying illegal accounts on social media platforms like Facebook, X and Instagram that use your brand name and logo or falsely announce business partnerships with your company.
- Discovering malicious ads: OSINT helps discover malicious paid advertisements, which commonly appear on search engines or social media, and are used to direct users to phishing sites using your brand name.
Discovering fraud infrastructure
This involves using OSINT to discover the technical ecosystem that powers the malicious campaigns, which allows the security team to shut down the means of the attack, not just the attack. OSINT can help in the following areas:
- Identify payment processors: Identify which companies are processing transactions for the fraudulent website, and notify them to stop immediately.
- Identify hosting providers: Revealing the web hosts or IT infrastructure providers (e.g., AWS, Cloudflare, smaller VPS companies) that are housing the fraudulent websites or command-and-control servers.
- Reveal communication channels: Fraudsters commonly use applications such as Telegram to distribute their scams, recruit "money mules," or organize attacks. Identifying these channels can help the security team report them for shutdown.
Tracking threat actors
OSINT is used to monitor online communities where fraudsters meet, exchange information and coordinate their attack activities. OSINT is used in this field to:
- Monitor darknet forums: Continually searching private, darknet, and semi-private forums/marketplaces where malicious tools and data are bought and sold. For example, a fraudster may post an advertisement on a darknet market offering to sell 5,000 corporate credentials stolen from a recent breach. Such information allows the security team to confirm a data breach and work instantly to prevent threat actors from exploiting it – by changing breached credentials, passwords, or revoking access of compromised accounts.
- Discover online communities sharing attack techniques and tools: Cybercriminals commonly share their attack techniques and exploit kits on darknet forums. By monitoring these places, the security team can discover how attackers are bypassing security measures and work to close any security gaps before they are exploited by hackers.
Organizations face the same intelligence environment as their adversaries. The difference is who takes action first. Implementing OSINT capabilities changes security from reacting to incidents to actively hunting threats.
Begin by setting up continuous monitoring of your digital presence, training teams to think like attackers during reconnaissance, and incorporating OSINT findings into current security processes. Threat actors already use these techniques against your organization; defensive OSINT helps you find and fix vulnerabilities before they can be exploited.
How OSINT strengthens corporate security FAQs
What is OSINT in corporate security?
OSINT in corporate security involves collecting and analyzing publicly available information—such as social media, domains, forums, and marketplaces—to identify threats, vulnerabilities, and adversary activity before attacks occur.
How do attackers use OSINT against organizations?
Threat actors use OSINT during reconnaissance to gather information about employees, infrastructure, and security gaps. This data helps them plan phishing, fraud, intrusion, and physical attacks with higher success rates.
How does OSINT help prevent fraud?
OSINT enables early detection of fraud schemes by monitoring domains, ads, forums, and social platforms where fraudsters coordinate attacks. This allows organizations to disrupt infrastructure before customers are impacted.
Is OSINT legal and compliant?
Yes, OSINT is both legal and compliant. OSINT relies on publicly available information. When conducted through secure platforms with proper governance, OSINT investigations remain compliant while minimizing organizational risk.
Why do security teams need a secure OSINT platform?
Investigating threats directly exposes analysts to tracking, targeting, and infrastructure risk. Secure platforms like Silo isolate environments, mask identity, and centralize workflows — allowing safe, scalable OSINT operations.
Tags OSINT research