This week’s Cyber Intel Brief uncovers Chinese zero-day exploitation of VMware systems, coordinated attacks on manufacturing networks, and AI-powered malware designed to outsmart modern defenses.
October 25-31, 2025 | Classification: TLP:CLEAR
EXECUTIVE SUMMARY
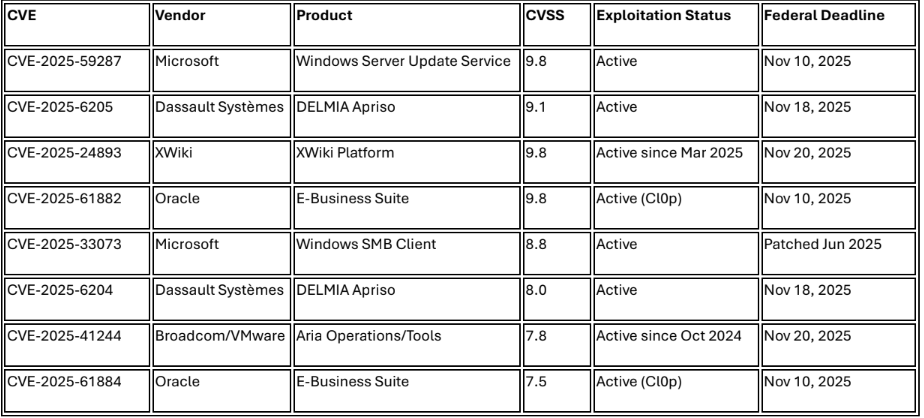
The reporting period featured intense cyber activity driven by the active, critical exploitation of high-severity vulnerabilities across enterprise and industrial systems, mandating immediate patching deadlines in November. The Chinese state-sponsored threat group UNC5174 exploited a VMware Aria Operations zero-day (CVE-2025-41244) since October 2024 to achieve root access, requiring remediation by November 20, 2025. Critical industrial operations are under concentrated attack, marked by CISA adding two DELMIA Apriso manufacturing system vulnerabilities (CVE-2025-6204/6205, CVSS 8.0/9.1) to the Known Exploited Vulnerabilities (KEV) catalog, the first Industrial Control System (ICS)/Operational Technology (OT) additions since December 2023. Furthermore, an emergency out-of-band update is required for the actively exploited, unauthenticated Remote Code Execution flaw in Microsoft Windows Server Update Service (CVE-2025-59287, CVSS 9.8).
Threat actors demonstrated significant technical evolution, focusing heavily on evasion and multi-platform resilience. The Russian GRU-affiliated Sandworm group conducted a two-month campaign using highly stealthy living-off-the-land tactics, relying mainly on legitimate Windows administration tools like rundll32.exe for credential harvesting to evade detection. Ransomware affiliates like Qilin deployed advanced hybrid attacks, combining Linux ransomware variants on Windows systems with a Bring Your Own Vulnerable Driver (BYOVD) approach to bypass security barriers. This complexity extends to mobile threats, where the Herodotus banking trojan bypasses behavioral biometrics by mimicking natural human typing patterns (randomized delays of 300 to 3000 milliseconds between characters) during remote sessions. Finally, the ClickFix social engineering technique continues to bypass traditional security controls by tricking users into manually executing obfuscated shell scripts, avoiding file-based detection.
CRITICAL INCIDENTS
1. Chinese APT Exploits VMware Zero-Day Since October 2024
Chinese state-sponsored threat group UNC5174 exploited VMware Aria Operations vulnerability (CVE-2025- 41244, CVSS 7.8) as zero-day beginning mid-October 2024, disclosed September 29, 2025, and added to CISA Known Exploited Vulnerabilities catalog October 30, 2025.1 The local privilege escalation vulnerability allows non-administrative users with VM access to escalate privileges to root when Service Discovery Management Pack is enabled.2 Malicious actors place custom binaries in /tmp/httpd directory, exploiting improper regex validation in get_versions.sh script to execute code with elevated privileges and spawn root shells.3
Affected systems include VMware Aria Operations (VMware Cloud Foundation Operations versions prior to 9.0.1.0) and VMware Tools versions prior to 13.0.5.0, 13.0.5, and 12.5.4.4 Broadcom updated security advisory VMSA-2025-0015 on October 30, 2025 to confirm suspected exploitation. 5 Federal agencies face November 20, 2025 remediation deadline under Binding Operational Directive 22-01. 6
2. Manufacturing Operations Platform Under Active Attack
CISA added two DELMIA Apriso manufacturing execution system vulnerabilities to Known Exploited Vulnerabilities catalog October 28, 2025 with confirmed active exploitation. 7 CVE-2025-6204 (CVSS 8.0) enables code injection attacks allowing arbitrary code execution on manufacturing operations management systems.8 CVE-2025-6205 (CVSS 9.1) represents missing authorization vulnerability enabling attackers to bypass authentication and gain privileged access. 9
Vulnerabilities affect DELMIA Apriso Release 2020 through Release 2025, with attack chains demonstrating ability to create privileged accounts, drop executables on web servers, and achieve full system compromise.10 This represents the third DELMIA Apriso vulnerability added to CISA KEV in recent months, following CVE-2025- 5086 (CVSS 9.0 deserialization vulnerability) added September 2025.11 DELMIA Apriso manages critical manufacturing processes for automotive and aerospace sectors globally, marking first industrial control system/operational technology vulnerability added to CISA KEV since December 2023. 12 Federal agencies must remediate by November 18, 2025. 13
3. Windows Server Update Service Exploitation Enables Supply Chain Attacks
Microsoft Windows Server Update Service vulnerability (CVE-2025-59287, CVSS 9.8) enables unauthenticated remote code execution through deserialization of untrusted data.14 Australian Cyber Security Centre confirmed active indiscriminate exploitation October 27, 2025, with proof-of-concept exploit code publicly available.15 CISA added vulnerability to Known Exploited Vulnerabilities catalog October 24, 2025, requiring federal remediation by November 10, 2025.16
Vulnerability affects Windows Server 2012 (all versions prior to build 6.2.9200.25728), Windows Server 2012 R2 (prior to build 6.3.9600.22826), Windows Server 2016 (prior to build 10.0.14393.8524), Windows Server 2019 (prior to build 10.0.17763.7922), Windows Server 2022 (prior to build 10.0.20348.4297), and Windows Server 2025 (prior to build 10.0.26100.6905).17 Microsoft released emergency out-of-band update October 23, 2025 after initial October Patch Tuesday remediation proved insufficient.18
4. Oracle E-Business Suite Exploitation Continues
CVE-2025-61882 (CVSS 9.8) and CVE-2025-61884 (CVSS 7.5) in Oracle E-Business Suite remain under active exploitation by Cl0p ransomware group conducting data theft attacks and extortion campaigns.19 Vulnerabilities enable pre-authentication remote code execution chains and server-side request forgery, allowing attackers to compromise systems without user credentials. 20
Affected systems span Oracle E-Business Suite versions 12.2.3-12.2.14, MySQL Server versions 8.0.0-9.4.0, Oracle Database Server versions 19.3-23.9, Oracle WebLogic Server versions 12.2.1.4.0-14.1.2.0.0, and over 250 additional products across financial services, telecommunications, retail, healthcare, and manufacturing sectors. 21 Multiple Oracle EBS customers reported data theft and extortion attempts following exploitation. 22
5. E-Commerce Platform Exploitation Hits 250+ Stores Overnight
Adobe Commerce and Magento vulnerability CVE-2025-54236 under active exploitation enables session hijacking through improper input validation in REST API without user interaction. 23 Attackers commonly drop PHP webshells on default session storage, with over 250 Magento stores compromised overnight in recent campaign. 24 Over 60% of Magento stores remain unpatched despite emergency advisory. 25
Vulnerability affects Adobe Commerce versions 2.4.9-alpha2 through 2.4.4-p15 and earlier. 26 Exploitation enables attackers to hijack administrator sessions and gain complete control of e-commerce platforms, compromising customer data and payment processing infrastructure.
6. Russian APT Conducts Living-Off-The-Land Attacks on Ukrainian Government
Russian GRU-affiliated Sandworm threat group conducted sophisticated attacks against Ukrainian government organizations and business services using living-off-the-land tactics to evade detection.27 Operations spanned two-month campaign against large business services organization and week-long
campaign against local government infrastructure beginning June 27, 2025. 28 Attackers deployed Localolive webshell on public-facing servers for persistent backdoor access and remote command execution. 29
Threat actors utilized legitimate Windows administration tools including rundll32.exe with comsvcs.dll for memory dumps every thirty minutes, specifically targeting KeePass password vault processes and credential repositories. 30 Advanced evasion techniques included Windows Resource Leak Diagnostic tool (rdrleakdiag) for memory dumping operations and registry hive exfiltration through native reg.exe commands. 31 Attackers deliberately disabled Windows Defender scanning on Downloads folder and created scheduled tasks for persistent credential harvesting. 32
7. Mobile Banking Malware Campaigns Demonstrate Advanced Evasion Capabilities
Sophisticated mobile banking threat campaigns expanded significantly throughout 2025 with multiple malware families demonstrating advanced evasion techniques targeting financial institutions globally. Over 760 malicious Android applications exploiting NFC relay technology emerged since April 2024, now affecting users across Russia, Poland, Czech Republic, Slovakia, and Brazil.33 Malicious apps masquerade as legitimate financial institution applications including major Russian banks (VTB, Tinkoff, Promsvyazbank), international institutions (Santander, Bradesco, PKO Bank Polski), and government portals. 34
NFC relay malware prompts victims to designate applications as default NFC payment method, then silently intercepts payment card data during tap-to-pay transactions, exfiltrating card numbers, expiration dates, and EMV fields through private Telegram channels. 35 Infrastructure includes over 70 command-and-control servers, dozens of Telegram bots for coordination, and approximately 20 impersonated institutions. 36 Applications establish persistent WebSocket connections enabling real-time communication with command and-control servers executing commands including register_device, apdu_command, card_info, and get_pin for complete payment credential extraction. 37
Herodotus banking trojan emerged targeting users in Italy and Brazil, introducing groundbreaking capability of mimicking human behavior during remote control sessions to bypass behavioral biometrics detection.38 Malware implements novel text input automation technique splitting operator-specified text into individual characters with randomized delays ranging from 300 to 3000 milliseconds between character input events, replicating natural human typing patterns. 39 Traditional remote access trojans deliver complete text strings instantaneously using ACTION_SET_TEXT function, creating suspicious patterns behavioral anti-fraud systems detect as automated attack indicators. 40 Herodotus operates through infection chain beginning with side loading and SMiShing campaigns, leveraging custom dropper designed to bypass Android 13+ restrictions on Accessibility Services. 41
GhostGrab banking trojan emerged with sophisticated overlay attack mechanism displaying convincing phishing screens atop legitimate banking applications. 42 When victims launch targeted financial apps, malware dynamically generates pixel-perfect replicas of login interfaces capturing credentials as users enter them.43 Trojan monitors incoming SMS messages through registered broadcast receivers, filtering for authentication codes matching common OTP patterns. 44 Extracted credentials and OTP codes are immediately encrypted using AES-256 encryption before transmission to remote servers, minimizing detection by network monitoring tools. 45 Financial institutions reported increased incidents of account takeovers correlating with GhostGrab infections, prompting enhanced monitoring protocols and customer security advisories. 46
8. PolarEdge Botnet Establishes Infrastructure-as-a-Service for APT Operations
PolarEdge botnet compromised over 25,000 IoT devices across 40 countries while establishing 140 command and-control servers to facilitate cybercrime operations.47 First disclosed February 2025, botnet exploits vulnerable IoT and edge devices to construct Operational Relay Box network providing infrastructure-as-a service for advanced persistent threat actors. 48 Infection campaign began gaining momentum May 2025 when security monitoring systems detected suspicious activity distributing ELF files. 49
Geographic distribution reveals concentration in Southeast Asia and North America, with South Korea accounting for 41.97 percent of compromised devices, followed by China at 20.35 percent and Thailand at 8.37 percent. 50 Primary targets include KT CCTV systems, Shenzhen TVT DVRs, Cyberoam UTM appliances, and router models from Asus, DrayTek, Cisco, and D-Link. 51 Infrastructure operates across VPS nodes predominantly hosted on Alibaba Cloud and Tencent Cloud platforms. 52
RPX system implements multi-hop proxy architecture designed for source concealment and attribution complexity. 53 When attackers utilize network, connections traverse from local proxy through RPX_Server to RPX_Client on compromised devices before reaching final destinations. 54 Malware achieves persistence through injection into initialization scripts and enforces single-instance execution. 55 Network operations utilize two independent connections: port 55555 for node registration and traffic proxying, and port 55560 for remote command execution. 56
ACTIVE THREAT ACTORS
UNC5174 (Chinese State-Sponsored APT)
Chinese state-sponsored advanced persistent threat group UNC5174 conducted zero-day exploitation of VMware Aria Operations vulnerability (CVE-2025-41244) beginning mid-October 2024, maintaining operational security for over one year before disclosure September 29, 2025.57 Group demonstrates sophisticated capability to identify and exploit privilege escalation vulnerabilities in enterprise virtualization infrastructure, with targeting focused on organizations operating VMware environments. 58
Exploitation methodology involves placement of malicious binaries in insecure temporary directories (/tmp/httpd), leveraging improper regex validation in VMware service discovery scripts to execute code with elevated privileges and establish root-level access. 59 Group maintains access to compromised virtualization infrastructure for long-term intelligence collection operations.
Cl0p Ransomware / FIN11
Cl0p ransomware group (FIN11) actively exploiting Oracle E-Business Suite vulnerabilities CVE-2025-61882 and CVE-2025-61884 in data theft and extortion campaigns targeting enterprise resource planning systems. 60 Group demonstrates pattern of rapidly weaponizing newly disclosed vulnerabilities for mass exploitation operations, with multiple Oracle EBS customers reporting data theft attempts following quarterly patch release. 61
Operational methodology involves leveraging server-side request forgery to bypass network segmentation, accessing internal APIs, and exfiltrating sensitive business data before delivering extortion demands. 62 Group focuses on high-value enterprise targets across financial services, healthcare, energy, and government sectors operating Oracle EBS platforms.63
North Korean Lazarus Group
North Korean state-sponsored Lazarus APT group expanded operations targeting European UAV and drone manufacturers through social engineering campaigns using trojanized GitHub projects and fake job-offer lures.³⁴ Group deploys ScoringMathTea RAT enabling remote control and theft of proprietary unmanned aerial vehicle designs and manufacturing data.64
Lazarus operations in February 2025 expanded to "ClickFake Interview" campaigns targeting cryptocurrency company job applicants with skill assessments incorporating ClickFix social engineering technique.65 Campaign objectives include malware distribution, sensitive information theft, and financial theft to fund North Korean geopolitical ambitions. 66 Corporate systems at multiple European defense manufacturers confirmed compromised, with sensitive weapons-system data likely exposed.67
Recent analysis revealed deployment of new malware variants including HttpTroy backdoor and enhanced BLINDINGCAN variant.68 HttpTroy provides comprehensive control capabilities including file manipulation, screenshot capture, command execution with elevated privileges, and reverse shell deployment. 69 Backdoor communicates exclusively through HTTP POST requests implementing two-layer obfuscation consisting of XOR encryption followed by Base64 encoding. 70
Lazarus targeted two Canadian entities using service-based persistence mechanisms and dynamic registry manipulation, suggesting targeting of enterprise infrastructure where legitimate system services provide effective camouflage for malicious operations. 71 Operations demonstrate continued evolution of North Korean cyber capabilities supporting espionage, financial theft, and weapons development programs.
Kimsuky (North Korean APT)
North Korean Kimsuky APT group deployed HttpTroy backdoor against single victim in South Korea through ZIP archive masquerading as VPN invoice from legitimate Korean security company. 72 Attack leveraged Korean language-based social engineering and scheduled task naming conventions consistent with local antivirus software, creating plausible-sounding system activities. 73
Campaign employed three-stage infection chain beginning with lightweight GO-based dropper containing three embedded files encrypted using XOR operations. 74 Upon execution, dropper displays deceptive PDF invoice while simultaneously establishing backdoor infrastructure through COM server registration via regsvr32.exe. 75 Second stage creates scheduled tasks mimicking AhnLab antivirus updates, repeating every minute to maintain persistence. 76
HttpTroy malware architecture incorporates dynamic API hashing and runtime string reconstruction techniques, preventing static analysis while complicating detection mechanisms deployed by security organizations monitoring for known malware signatures and behavioral indicators. 77
Sandworm (Russian GRU APT)
Russian military intelligence unit Sandworm conducted sophisticated living-off-the-land attacks against Ukrainian government organizations and business services spanning two-month operation.78 Attackers demonstrate exceptional operational security awareness, minimizing malware deployment while relying primarily on legitimate Windows administration tools and dual-use utilities to avoid detection. 79
Initial compromise occurred through webshell deployment on public-facing servers exploiting unpatched vulnerabilities. 80 Attackers utilized Localolive webshell for establishing persistent backdoor access enabling remote command execution capabilities.81 Operations showcase threat actors prioritizing stealth over speed, employing legitimate administration tools to maintain attribution ambiguity while systematically harvesting sensitive organizational data throughout extended network access periods. 82
SALT TYPHOON (Chinese APT)
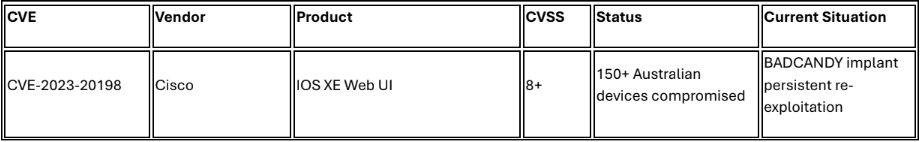
Chinese nexus APT group SALT TYPHOON associated with BADCANDY implant operations targeting Cisco IOS XE devices.83 Since July 2025, Australian Cyber Security Centre assessed over 400 devices potentially compromised with BADCANDY implant in Australia, with over 150 devices remaining compromised as of late October 2025.84
BADCANDY represents low-equity Lua-based web shell exploiting CVE-2023-20198, one of top routinely exploited vulnerabilities in 2023. 85 Threat actors typically apply non-persistent patch post-compromise to mask device vulnerability status. 86 Implant does not persist following device reboot; however, actors who accessed account credentials or established other persistence mechanisms retain network access.87 Australian authorities believe actors can detect when BADCANDY implant is removed and re-exploit devices, with bulk victim notifications showing steady decline from 400+ compromises to under 200 in 2025 but fluctuations indicating ongoing re-exploitation. 88
LockBit Ransomware Group
LockBit ransomware group demonstrated rapid resurgence following 2024 disruption, with dozen organizations compromised in September 2025, half by new LockBit 5.0 ("ChuongDong") variant.89 Technical evolution includes multi-platform builds (Windows, Linux, ESXi), stronger anti-analysis capabilities, and faster encryption algorithms. 90 Group deploys attacks across Europe, Americas, and Asia, maintaining high operational tempo despite law enforcement disruption operations. 91
Qilin Ransomware Group
Qilin ransomware group claimed more than 40 victims every month since start of 2025, barring January, with number of postings on data leak site touching high of 100 cases in June.92 Group accounted for 84 victims each in August and September 2025, emerging as one of most active ransomware groups. 93 Operations active since July 2022 with attacks primarily targeting manufacturing (23%), professional and scientific services (18%), and wholesale trade (10%) sectors in U.S., Canada, U.K., France, and Germany. 94
Attacks mounted by Qilin affiliates leverage leaked administrative credentials on dark web for initial access using VPN interface, followed by RDP connections to domain controller and successfully breached endpoints. 95 Attackers conduct system reconnaissance and network discovery, executing tools like Mimikatz, WebBrowserPassView.exe, BypassCredGuard.exe, and SharpDecryptPwd to facilitate credential harvesting and exfiltrate data to external SMTP server using Visual Basic Script. 96
Recent analysis uncovered sophisticated Qilin attack deploying Linux ransomware variant on Windows systems combined with bring your own vulnerable driver (BYOVD) technique and legitimate IT tools to bypass security barriers.97 Attackers abused legitimate tools including AnyDesk through Atera Networks' RMM platform, ScreenConnect for command execution, and Splashtop for final ransomware execution.98 Group specifically targeted Veeam backup infrastructure using specialized credential extraction tools, systematically harvesting credentials from multiple backup databases to compromise disaster recovery capabilities before deploying ransomware payload.99
Qilin operations deploy SOCKS proxy DLL to facilitate remote access, abuse ScreenConnect's remote management capabilities for discovery commands and network scanning, use "eskle.sys" driver as part of BYOVD attack to disable security solutions, deploy PuTTY SSH clients for lateral movement to Linux systems, use COROXY backdoor for command-and-control traffic obfuscation, and execute Linux ransomware binary directly on Windows systems using Splashtop Remote's management service. 100
Predatory Sparrow (Israeli-Attributed)
Israeli-attributed cyber-sabotage group Predatory Sparrow continues escalating operations targeting Iranian critical infrastructure, financial systems, and government institutions.101 In June 2025, group claimed responsibility for erasing Bank Sepah data and disrupting services, followed by attacking Nobitex cryptocurrency exchange resulting in theft and permanent destruction of $90 million in cryptocurrency. 102 Attackers published Nobitex complete source code, infrastructure documentation, and internal R&D materials. 103
Group deploys multi-stage malware chains using native Windows batch scripting and Visual Basic droppers to maintain stealth and persistence.104 In attacks against Iranian Railways, group employed "Meteor" wiper malware with XOR-encrypted configuration files to evade detection, executing through scheduled tasks for coordinated large-scale infrastructure paralysis.105 Operations demonstrate state-level capability and strategic targeting aligned with Israeli national security interests, focusing on economic damage, psychological impact through public data destruction claims, and degradation of Iranian critical infrastructure resilience.106
TRENDS
Social Engineering Evolution Bypasses Traditional Security Controls
ClickFix social engineering technique became prevalent in 2025 due to ability to target multiple operating systems for data theft, financial theft, and malware distribution.107 Between January 2025 and October 2025, Center for Internet Security Cyber Threat Intelligence tracked two ClickFix campaigns leading to ransomware distribution, including August 2025 Interlock ransomware incident affecting U.S. State, Local, Tribal, and Territorial government victim. 108 ClickFix comprised over one-third of all non-malware Albert Network Monitoring and Management alerts in first half of 2025. 109
Technique exploits user familiarity with CAPTCHA verification and security prompts, tricking users into executing malicious shell scripts. 110 Threat actors leverage unauthorized access to legitimate websites to inject JavaScript producing fake CAPTCHA verification or Cloudflare Turnstile prompts, triggering user interaction while preventing automated analysis. 111 Users instructed to copy obfuscated PowerShell scripts and execute via Windows Run utility, downloading additional payloads from attacker-controlled infrastructure. 112
ClickFix campaigns distributed Lumma Stealer (information stealer), trojanized NetSupport (legitimate remote administration tool abused for malicious access), and SocGholish/FakeUpdates JavaScript payloads stealing sensitive information and dropping additional malware including ransomware.113 Technique bypasses traditional security controls by relying on users executing scripts directly rather than downloading files, evading file-based detection mechanisms and endpoint protection systems. 114
UK Nationally Significant Cyber Attacks Surge 48%
UK National Cyber Security Centre handled 204 nationally significant cyber attacks in 12-month reporting period ending October 2025, representing 48% increase from 89 incidents in previous period.115 NCSC
responded to 429 total cyber incidents averaging four nationally significant attacks weekly. 116 High-profile attacks impacted Marks & Spencer, Co-op Group, Harrods, and Jaguar Land Rover with operational disruptions including empty shelves and production line shutdowns. 117
Legacy system vulnerabilities in Microsoft SharePoint, Ivanti products, and Fortinet FortiManager connected to 29 incidents. 118 Advanced persistent threat actors from China, Russia, Iran, and North Korea conducting escalated cyber operations increasingly targeting critical infrastructure and major corporations. 119 UK government issued letters to all FTSE 350 companies urging elevation of cyber risk to board-level priority. 120
Australian Critical Infrastructure Targeting Intensifies
Australian Cyber Security Centre Annual Cyber Threat Report 2024-25 revealed 84,700+ cybercrime reports (one every 6 minutes), with critical infrastructure entities receiving 190+ notifications of malicious activity representing 111% increase year-over-year. 121 Average incident cost for small businesses increased to $56,600 (14% increase). 122
Top targeted sectors include Government, Financial Services, Healthcare, and IT/Telecommunications. 123 Scattered Spider threat actor conducting help desk social engineering attacks for initial access. 124 Legacy system vulnerabilities remain primary attack vector across Australian organizations.125
Manufacturing Sector Under Coordinated Attack
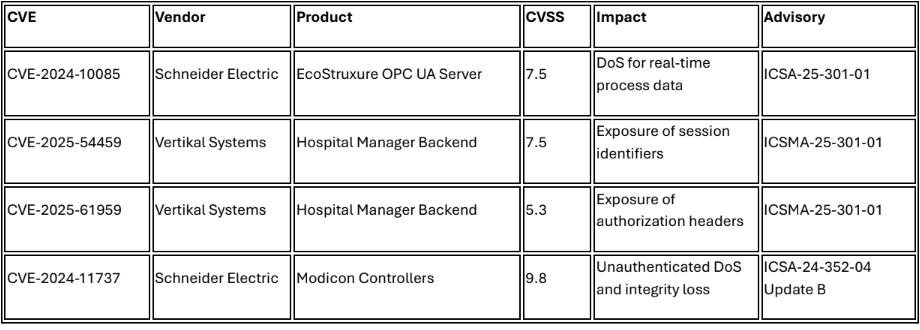
Three DELMIA Apriso vulnerabilities added to CISA Known Exploited Vulnerabilities catalog within two months (CVE-2025-5086 in September, CVE-2025-6204 and CVE-2025-6205 in October) demonstrates concentrated targeting of manufacturing execution systems.126DELMIA Apriso manages critical manufacturing processes for automotive and aerospace sectors globally, representing first industrial control system/operational technology vulnerability added to CISA KEV since December 2023. 127
CISA published 13 industrial control systems advisories during October 2025 addressing vulnerabilities in Schneider Electric, Vertikal Systems, Rockwell Automation, Siemens, CloudEdge, Raisecomm, and Oxford Nanopore products.128 Products deployed across commercial facilities, critical manufacturing, energy, and healthcare sectors. 129 Multiple vulnerabilities enable denial of service for real-time process data, unauthorized access to session identifiers and authorization headers, and unauthenticated attacks sending crafted packets causing denial of service and integrity loss. 130
Analyst Comment: Concentrated vulnerability disclosures across multiple industrial control system vendors combined with active exploitation of manufacturing execution systems indicates coordinated reconnaissance and targeting campaign. Organizations operating operational technology should implement defense-in-depth strategies including network segmentation isolating control systems from enterprise networks and enhanced monitoring for unauthorized access attempts.
Fake Investment Platform Fraud Operations Demonstrate Sophisticated Infrastructure
Fraudulent investment platforms impersonating cryptocurrency and forex exchanges emerged as predominant method used by financially motivated cybercriminals to defraud victims across Asia and beyond.131 Operations evolved from isolated cybercriminal activities to highly organized cross-border operations with structured hierarchies and specialized roles. 132 In August 2025, Vietnamese authorities arrested 20 individuals connected to billion-dollar Paynet Coin crypto scam, charging them with multi-level marketing violations and asset misappropriation. 133
Threat actors employ multi-stage victim manipulation framework beginning with initial contact through social media platforms including Zalo, Facebook, TikTok, and messaging applications such as Telegram and WhatsApp.134 Scammers present themselves as successful investors or financial experts using carefully crafted personas and forged credentials to establish trust. 135 When victims display hesitation, operators introduce additional "bait" personas including fake fellow investors, friends, or support staff who engage directly with targets to simulate genuine platform activity and reinforce illusion of legitimacy. 136
Technical analysis reveals fraudulent platforms operate on shared backend infrastructure rather than isolated throwaway websites.137 Analysis uncovered recurring API endpoints, SSL certificate reuse, and common administrative interfaces across multiple scam domains with cross-domain HTTP requests showing connections to API subdomains using paths such as /user/info, /index/tickers, and /index/init. 138 Infrastructure investigation uncovered exposed administrative panels accessible through subdomains following predictable naming patterns, with control interfaces often presented in Simplified Chinese featuring integration with popular Chinese platforms including Tencent QQ, WeChat, and Weibo. 139
Chat-based onboarding systems represent sophisticated technical layer, with many platforms loading chatbot interfaces powered by third-party services like Meiqia serving multiple functions including access control, trust reinforcement, and payment instruction delivery. 140 When victims select deposit functions, platforms redirect to chatbot windows providing specific bank account details or cryptocurrency wallet addresses. 141 Technical infrastructure includes auxiliary components such as chat simulation tools designed to fabricate convincing conversation screenshots with configurable message metadata, timestamps, and delivery status indicators to create fabricated social proof for victim persuasion. 142
Ransomware Groups Demonstrate Technical Evolution and Resilience
Qilin ransomware operations demonstrate sophisticated technical evolution with deployment of Linux ransomware variants on Windows systems using bring your own vulnerable driver techniques combined with legitimate IT tool abuse.143 Group claimed 100 victims in June 2025 and maintained 84 victims monthly in August and September, demonstrating sustained operational capability. 144 Attacks leverage multiple remote monitoring and management tools including AnyDesk, Chrome Remote Desktop, Distant Desktop, GoToDesk, QuickAssist, and ScreenConnect for persistent access and lateral movement. 145
LockBit group demonstrated rapid resurgence following 2024 law enforcement disruption operations, with new LockBit 5.0 variant featuring multi-platform builds across Windows, Linux, and ESXi systems, stronger anti analysis capabilities, and faster encryption algorithms.146 Group maintains high operational tempo deploying attacks across Europe, Americas, and Asia despite international law enforcement coordination. 147
Beast ransomware group launched February 2025 and rapidly expanded operations with 16 publicly disclosed victims by August 2025 spanning United States, Europe, Asia, and Latin America across manufacturing, construction, healthcare, business services, and education sectors.148 Group operates sophisticated affiliate network with distributed partnership model where each victim receives separate negotiation communications from different threat actors. 149 Beast employs network propagation methodology centered on SMB port scanning from compromised systems, enabling lateral movement across organizational infrastructure without requiring additional user interaction. 150 This horizontal spreading capability proves particularly effective in enterprise environments where network shares remain inadequately segmented, maximizing infection scope while maintaining low detection profiles. 151
Gentlemen's RaaS emerged on underground forums offering cross-platform attack capability targeting Windows, Linux, NAS, BSD, and ESXi systems with generous 90% affiliate revenue sharing arrangement.152
Platform deploys Go-based locker and separate C-coded ESXi locker utilizing XChaCha20 with Curve25519 cryptography and per-file ephemeral keys. 153 Self-propagation capability through WMI, WMIC, SCHTASKS, SC, and PowerShell Remoting commands enables rapid network traversal with persistence via scheduled tasks and run-on-boot routines.154
VULNERABILITIES
Critical Patches Required This Month (October/November 2025)
Industrial Control Systems Requiring Immediate Attention
Continuing Active Exploitation (No New Patches)

RECOMMENDATIONS
1. Emergency Patching Priority
- Deploy Microsoft emergency out-of-band patch for CVE-2025-59287 (WSUS) immediately to all Windows Server instances
- Apply VMware patches for CVE-2025-41244 (Aria Operations/Tools) and verify Service Discovery Management Pack configurations
- Patch DELMIA Apriso systems for CVE-2025-6204 and CVE-2025-6205 or implement network isolation if patching cannot be completed immediately
- Update Adobe Commerce/Magento systems to address CVE-2025-54236 SessionReaper vulnerability
2. Oracle E-Business Suite Operators
- Implement emergency patching for CVE-2025-61884 and CVE-2025-61882
- Review network logs for indicators of Cl0p ransomware activity and server-side request forgery exploitation
- Establish network segmentation preventing SSRF exploitation of internal APIs
- Conduct forensic analysis for evidence of data exfiltration or account compromise
3. Windows Server Administrators
- Verify WSUS instances not exposed to untrusted networks
- Implement SMB signing enforcement to mitigate CVE-2025-33073 privilege escalation • Review running configurations for unexpected privilege 15 accounts and unknown tunnel interfaces • Establish enhanced monitoring for WSUS server compromise indicators
4. Industrial Control System Operators
- Review CISA ICS advisories ICSA-25-301-01, ICSMA-25-301-01, and ICSA-24-352-04 Update B • Apply Schneider Electric, Rockwell Automation, and Siemens patches to affected systems
- Implement network segmentation isolating operational technology environments from enterprise networks
- Establish baseline monitoring for Modbus traffic and OPC UA server connections
5. Mobile Banking Security
- Issue customer advisories regarding NFC relay malware affecting Android devices
- Implement enhanced fraud detection monitoring for NFC-based transactions showing anomalous patterns
- Establish application whitelisting policies for mobile device management systems preventing installation of unauthorized banking applications
- Review transaction logs for indicators of NFC relay exploitation including unusual geographic patterns or velocity checks
6. IoT Infrastructure Security
- Conduct immediate inventory of IoT devices including CCTV systems, DVRs, UTM appliances, and routers
- Review network logs for suspicious outbound connections from IoT devices to cloud hosting providers • Implement network segmentation isolating IoT devices from critical business systems • Establish baseline monitoring for IoT device communication patterns
1 Cybersecurity and Infrastructure Security Agency. (2025, October 30). CISA adds two known exploited vulnerabilities to catalog. https://www.cisa.gov/news-events/alerts/2025/10/30/cisa-adds-two-known-exploited-vulnerabilities-catalog
2 Broadcom. (2025, October 30). VMSA-2025-0015.1: VMware Aria Operations and VMware Tools updates address multiple vulnerabilities. https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/36149
3 NVISO. (2025, September 29). You name it, VMware elevates it (CVE-2025-41244). https://blog.nviso.eu/2025/09/29/you-name-it vmware-elevates-it-cve-2025-41244/
4 Center for Internet Security. (2025). Multiple vulnerabilities in VMware Aria Operations and VMware Tools could allow for privilege escalation (Advisory No. 2025-092). https://www.cisecurity.org/advisory/multiple-vulnerabilities-in-vmware-aria-operations-and vmware-tools-could-allow-for-privilege-escalation_2025-092
5 Broadcom. (2025, October 30). VMSA-2025-0015.1: VMware Aria Operations and VMware Tools updates address multiple vulnerabilities. https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/36149
6 Cybersecurity and Infrastructure Security Agency. (2025, October 30). CISA adds two known exploited vulnerabilities to catalog. https://www.cisa.gov/news-events/alerts/2025/10/30/cisa-adds-two-known-exploited-vulnerabilities-catalog
7 Cybersecurity and Infrastructure Security Agency. (2025, October 30). CISA adds two known exploited vulnerabilities to catalog. https://www.cisa.gov/news-events/alerts/2025/10/30/cisa-adds-two-known-exploited-vulnerabilities-catalog
8The Cyber Express. (2025, October 28). CISA warns DELMIA Apriso vulnerabilities are under attack.
https://thecyberexpress.com/delmia-apriso-vulnerabilities-under-attack/
9 Cybersecurity and Infrastructure Security Agency. (2025, October 30). CISA adds two known exploited vulnerabilities to catalog. https://www.cisa.gov/news-events/alerts/2025/10/30/cisa-adds-two-known-exploited-vulnerabilities-catalog
10 SC Media. (2025, October 28). Dassault Apriso flaws added to CISA list of exploited vulnerabilities.
https://www.scworld.com/news/dassault-apriso-flaws-added-to-cisa-list-of-exploited-vulnerabilities
11 The Cyber Express. (2025, October 28). CISA warns DELMIA Apriso vulnerabilities are under attack.
https://thecyberexpress.com/delmia-apriso-vulnerabilities-under-attack/
12 The Cyber Express. (2025, October 28). CISA warns DELMIA Apriso vulnerabilities are under attack.
https://thecyberexpress.com/delmia-apriso-vulnerabilities-under-attack/
13 Cybersecurity and Infrastructure Security Agency. (2025, October 30). CISA adds two known exploited vulnerabilities to catalog. https://www.cisa.gov/news-events/alerts/2025/10/30/cisa-adds-two-known-exploited-vulnerabilities-catalog
14 Center for Internet Security. (2025, October 24). A vulnerability in Microsoft Windows Server Update Services (WSUS) could allow for remote code execution (Advisory No. 2025-099). https://www.cisecurity.org/advisory/a-vulnerability-in-microsoft-windows-server update-services-wsus-could-allow-for-remote-code-execution_2025-099
15 Australian Signals Directorate's Australian Cyber Security Centre. (2025, October 25). Critical vulnerability in Microsoft Windows Server Update Service (WSUS). Australian Government cyber.gov.au. https://www.cyber.gov.au/about-us/view-all-content/alerts-and advisories/critical-vulnerability-in-Microsoft-Windows-Server-Update-Service
16 Center for Internet Security. (2025, October 24). A vulnerability in Microsoft Windows Server Update Services (WSUS) could allow for remote code execution (Advisory No. 2025-099). https://www.cisecurity.org/advisory/a-vulnerability-in-microsoft-windows-server update-services-wsus-could-allow-for-remote-code-execution_2025-099
17 Center for Internet Security. (2025, October 24). A vulnerability in Microsoft Windows Server Update Services (WSUS) could allow for remote code execution (Advisory No. 2025-099). https://www.cisecurity.org/advisory/a-vulnerability-in-microsoft-windows-server update-services-wsus-could-allow-for-remote-code-execution_2025-099
18 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
19 Center for Internet Security. (2025, October 22). Oracle quarterly critical patches issued October 21, 2025 (Advisory No. 2025-098). https://www.cisecurity.org/advisory/oracle-quarterly-critical-patches-issued-october-21-2025_2025-098
20 Center for Internet Security. (2025, October 22). Oracle quarterly critical patches issued October 21, 2025 (Advisory No. 2025-098). https://www.cisecurity.org/advisory/oracle-quarterly-critical-patches-issued-october-21-2025_2025-098
21 Center for Internet Security. (2025, October 22). Oracle quarterly critical patches issued October 21, 2025 (Advisory No. 2025-098). https://www.cisecurity.org/advisory/oracle-quarterly-critical-patches-issued-october-21-2025_2025-098
22 Center for Internet Security. (2025, October 22). Oracle quarterly critical patches issued October 21, 2025 (Advisory No. 2025-098). https://www.cisecurity.org/advisory/oracle-quarterly-critical-patches-issued-october-21-2025_2025-098
23 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
24 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
25 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
26 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
27 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
28 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
29 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
30 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
31 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
32 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
33 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
34 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
35 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
36 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
37 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
38 Cybersecurity News. (2025, October). New Android malware Herodotus mimic human behaviour to bypass biometrics detection. https://cybersecuritynews.com/new-android-malware-herodotus-mimic-human-behaviour/
39 Cybersecurity News. (2025, October). New Android malware Herodotus mimic human behaviour to bypass biometrics detection. https://cybersecuritynews.com/new-android-malware-herodotus-mimic-human-behaviour/
40 Cybersecurity News. (2025, October). New Android malware Herodotus mimic human behaviour to bypass biometrics detection. https://cybersecuritynews.com/new-android-malware-herodotus-mimic-human-behaviour/
41 Cybersecurity News. (2025, October). New Android malware Herodotus mimic human behaviour to bypass biometrics detection. https://cybersecuritynews.com/new-android-malware-herodotus-mimic-human-behaviour/
42 Cybersecurity News. (2025, October). New GhostGrab Android malware silently steals banking login details and intercept SMS for OTPs. https://cybersecuritynews.com/new-ghostgrab-android-malware/
43 Cybersecurity News. (2025, October). New GhostGrab Android malware silently steals banking login details and intercept SMS for OTPs. https://cybersecuritynews.com/new-ghostgrab-android-malware/
44 Cybersecurity News. (2025, October). New GhostGrab Android malware silently steals banking login details and intercept SMS for OTPs. https://cybersecuritynews.com/new-ghostgrab-android-malware/
45 Cybersecurity News. (2025, October). New GhostGrab Android malware silently steals banking login details and intercept SMS for OTPs. https://cybersecuritynews.com/new-ghostgrab-android-malware/
46 Cybersecurity News. (2025, October). New GhostGrab Android malware silently steals banking login details and intercept SMS for OTPs. https://cybersecuritynews.com/new-ghostgrab-android-malware/
47 Cybersecurity News. (2025, October). PolarEdge botnet infected 25,000+ devices and 140 C2 servers exploiting IoT vulnerabilities. https://cybersecuritynews.com/polaredge-botnet-infected-25000-devices/
48 Cybersecurity News. (2025, October). PolarEdge botnet infected 25,000+ devices and 140 C2 servers exploiting IoT vulnerabilities. https://cybersecuritynews.com/polaredge-botnet-infected-25000-devices/
49 Cybersecurity News. (2025, October). PolarEdge botnet infected 25,000+ devices and 140 C2 servers exploiting IoT vulnerabilities. https://cybersecuritynews.com/polaredge-botnet-infected-25000-devices/
50 Cybersecurity News. (2025, October). PolarEdge botnet infected 25,000+ devices and 140 C2 servers exploiting IoT vulnerabilities. https://cybersecuritynews.com/polaredge-botnet-infected-25000-devices/
51 Cybersecurity News. (2025, October). PolarEdge botnet infected 25,000+ devices and 140 C2 servers exploiting IoT vulnerabilities. https://cybersecuritynews.com/polaredge-botnet-infected-25000-devices/
52 Cybersecurity News. (2025, October). PolarEdge botnet infected 25,000+ devices and 140 C2 servers exploiting IoT vulnerabilities. https://cybersecuritynews.com/polaredge-botnet-infected-25000-devices/
53 Cybersecurity News. (2025, October). PolarEdge botnet infected 25,000+ devices and 140 C2 servers exploiting IoT vulnerabilities. https://cybersecuritynews.com/polaredge-botnet-infected-25000-devices/
54 Cybersecurity News. (2025, October). PolarEdge botnet infected 25,000+ devices and 140 C2 servers exploiting IoT vulnerabilities. https://cybersecuritynews.com/polaredge-botnet-infected-25000-devices/
55 Cybersecurity News. (2025, October). PolarEdge botnet infected 25,000+ devices and 140 C2 servers exploiting IoT vulnerabilities. https://cybersecuritynews.com/polaredge-botnet-infected-25000-devices/
56 Cybersecurity News. (2025, October). PolarEdge botnet infected 25,000+ devices and 140 C2 servers exploiting IoT vulnerabilities. https://cybersecuritynews.com/polaredge-botnet-infected-25000-devices/
57 NVISO. (2025, September 29). You name it, VMware elevates it (CVE-2025-41244). https://blog.nviso.eu/2025/09/29/you-name-it vmware-elevates-it-cve-2025-41244/
58 NVISO. (2025, September 29). You name it, VMware elevates it (CVE-2025-41244). https://blog.nviso.eu/2025/09/29/you-name-it vmware-elevates-it-cve-2025-41244/
59 NVISO. (2025, September 29). You name it, VMware elevates it (CVE-2025-41244). https://blog.nviso.eu/2025/09/29/you-name-it vmware-elevates-it-cve-2025-41244/
60 Center for Internet Security. (2025, October 22). Oracle quarterly critical patches issued October 21, 2025 (Advisory No. 2025-098). https://www.cisecurity.org/advisory/oracle-quarterly-critical-patches-issued-october-21-2025_2025-098
61 Center for Internet Security. (2025, October 22). Oracle quarterly critical patches issued October 21, 2025 (Advisory No. 2025-098). https://www.cisecurity.org/advisory/oracle-quarterly-critical-patches-issued-october-21-2025_2025-098
62 Center for Internet Security. (2025, October 22). Oracle quarterly critical patches issued October 21, 2025 (Advisory No. 2025-098). https://www.cisecurity.org/advisory/oracle-quarterly-critical-patches-issued-october-21-2025_2025-098
63 Center for Internet Security. (2025, October 22). Oracle quarterly critical patches issued October 21, 2025 (Advisory No. 2025-098). https://www.cisecurity.org/advisory/oracle-quarterly-critical-patches-issued-october-21-2025_2025-098
64 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
65 Center for Internet Security Cyber Threat Intelligence Team. (2025, October 27). ClickFix: An adaptive social engineering technique. Center for Internet Security. https://www.cisecurity.org/insights/blog/clickfix-an-adaptive-social-engineering-technique
66 Center for Internet Security Cyber Threat Intelligence Team. (2025, October 27). ClickFix: An adaptive social engineering technique. Center for Internet Security. https://www.cisecurity.org/insights/blog/clickfix-an-adaptive-social-engineering-technique
67 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
68 Cybersecurity News. (2025, October). Kimsuky and Lazarus hacker groups unveil new tools that enable backdoor and remote access. https://cybersecuritynews.com/kimsuky-and-lazarus-hacker-groups-unveil-new-tools/
69 Cybersecurity News. (2025, October). Kimsuky and Lazarus hacker groups unveil new tools that enable backdoor and remote access. https://cybersecuritynews.com/kimsuky-and-lazarus-hacker-groups-unveil-new-tools/
70 Cybersecurity News. (2025, October). Kimsuky and Lazarus hacker groups unveil new tools that enable backdoor and remote access. https://cybersecuritynews.com/kimsuky-and-lazarus-hacker-groups-unveil-new-tools/
71 Cybersecurity News. (2025, October). Kimsuky and Lazarus hacker groups unveil new tools that enable backdoor and remote access. https://cybersecuritynews.com/kimsuky-and-lazarus-hacker-groups-unveil-new-tools/
72 Cybersecurity News. (2025, October). Kimsuky and Lazarus hacker groups unveil new tools that enable backdoor and remote access. https://cybersecuritynews.com/kimsuky-and-lazarus-hacker-groups-unveil-new-tools/
73 Cybersecurity News. (2025, October). Kimsuky and Lazarus hacker groups unveil new tools that enable backdoor and remote access. https://cybersecuritynews.com/kimsuky-and-lazarus-hacker-groups-unveil-new-tools/
74 Cybersecurity News. (2025, October). Kimsuky and Lazarus hacker groups unveil new tools that enable backdoor and remote access. https://cybersecuritynews.com/kimsuky-and-lazarus-hacker-groups-unveil-new-tools/
75 Cybersecurity News. (2025, October). Kimsuky and Lazarus hacker groups unveil new tools that enable backdoor and remote access. https://cybersecuritynews.com/kimsuky-and-lazarus-hacker-groups-unveil-new-tools/
76 Cybersecurity News. (2025, October). Kimsuky and Lazarus hacker groups unveil new tools that enable backdoor and remote access. https://cybersecuritynews.com/kimsuky-and-lazarus-hacker-groups-unveil-new-tools/
77 Cybersecurity News. (2025, October). Kimsuky and Lazarus hacker groups unveil new tools that enable backdoor and remote access. https://cybersecuritynews.com/kimsuky-and-lazarus-hacker-groups-unveil-new-tools/
78 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
79 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
80 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
81 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
82 Cybersecurity News. (2025, October). Russian hackers attacking government entity using stealthy living-off-the-land tactics. https://cybersecuritynews.com/russian-hackers-attacking-government-entity/
83 Australian Signals Directorate's Australian Cyber Security Centre. (2025, October 31). Don't take BADCANDY from strangers – How your devices could be implanted and what to do about it. Australian Government cyber.gov.au. https://www.cyber.gov.au/about-us/view all-content/alerts-and-advisories/badcandy
84 Australian Signals Directorate's Australian Cyber Security Centre. (2025, October 31). Don't take BADCANDY from strangers – How your devices could be implanted and what to do about it. Australian Government cyber.gov.au. https://www.cyber.gov.au/about-us/view all-content/alerts-and-advisories/badcandy
85 Australian Signals Directorate's Australian Cyber Security Centre. (2025, October 31). Don't take BADCANDY from strangers – How your devices could be implanted and what to do about it. Australian Government cyber.gov.au. https://www.cyber.gov.au/about-us/view all-content/alerts-and-advisories/badcandy
86 Australian Signals Directorate's Australian Cyber Security Centre. (2025, October 31). Don't take BADCANDY from strangers – How your devices could be implanted and what to do about it. Australian Government cyber.gov.au. https://www.cyber.gov.au/about-us/view all-content/alerts-and-advisories/badcandy
87 Australian Signals Directorate's Australian Cyber Security Centre. (2025, October 31). Don't take BADCANDY from strangers – How your devices could be implanted and what to do about it. Australian Government cyber.gov.au. https://www.cyber.gov.au/about-us/view all-content/alerts-and-advisories/badcandy
88 Australian Signals Directorate's Australian Cyber Security Centre. (2025, October 31). Don't take BADCANDY from strangers – How your devices could be implanted and what to do about it. Australian Government cyber.gov.au. https://www.cyber.gov.au/about-us/view all-content/alerts-and-advisories/badcandy
89 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
90 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
91 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
92 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
93 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
94 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
95 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
96 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
97 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
98 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
99 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
100 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
101 Priya. (2025, October 28). Predatory Sparrow group launches attacks on critical infrastructure to disrupt and destroy data. Cyber Security News. https://cyberpress.org/predatory-sparrow-cyberattack/
102 Priya. (2025, October 28). Predatory Sparrow group launches attacks on critical infrastructure to disrupt and destroy data. Cyber Security News. https://cyberpress.org/predatory-sparrow-cyberattack/
103 Priya. (2025, October 28). Predatory Sparrow group launches attacks on critical infrastructure to disrupt and destroy data. Cyber Security News. https://cyberpress.org/predatory-sparrow-cyberattack/
104 Priya. (2025, October 28). Predatory Sparrow group launches attacks on critical infrastructure to disrupt and destroy data. Cyber Security News. https://cyberpress.org/predatory-sparrow-cyberattack/
105 Priya. (2025, October 28). Predatory Sparrow group launches attacks on critical infrastructure to disrupt and destroy data. Cyber Security News. https://cyberpress.org/predatory-sparrow-cyberattack/
106 Priya. (2025, October 28). Predatory Sparrow group launches attacks on critical infrastructure to disrupt and destroy data. Cyber Security News. https://cyberpress.org/predatory-sparrow-cyberattack/
107 Center for Internet Security Cyber Threat Intelligence Team. (2025, October 27). ClickFix: An adaptive social engineering technique. Center for Internet Security. https://www.cisecurity.org/insights/blog/clickfix-an-adaptive-social-engineering-technique
108 Center for Internet Security Cyber Threat Intelligence Team. (2025, October 27). ClickFix: An adaptive social engineering technique. Center for Internet Security. https://www.cisecurity.org/insights/blog/clickfix-an-adaptive-social-engineering-technique
109 Center for Internet Security Cyber Threat Intelligence Team. (2025, October 27). ClickFix: An adaptive social engineering technique. Center for Internet Security. https://www.cisecurity.org/insights/blog/clickfix-an-adaptive-social-engineering-technique
110 Center for Internet Security Cyber Threat Intelligence Team. (2025, October 27). ClickFix: An adaptive social engineering technique. Center for Internet Security. https://www.cisecurity.org/insights/blog/clickfix-an-adaptive-social-engineering-technique
111 Center for Internet Security Cyber Threat Intelligence Team. (2025, October 27). ClickFix: An adaptive social engineering technique. Center for Internet Security. https://www.cisecurity.org/insights/blog/clickfix-an-adaptive-social-engineering-technique
112 Center for Internet Security Cyber Threat Intelligence Team. (2025, October 27). ClickFix: An adaptive social engineering technique. Center for Internet Security. https://www.cisecurity.org/insights/blog/clickfix-an-adaptive-social-engineering-technique
113 Center for Internet Security Cyber Threat Intelligence Team. (2025, October 27). ClickFix: An adaptive social engineering technique. Center for Internet Security. https://www.cisecurity.org/insights/blog/clickfix-an-adaptive-social-engineering-technique
114 Center for Internet Security Cyber Threat Intelligence Team. (2025, October 27). ClickFix: An adaptive social engineering technique. Center for Internet Security. https://www.cisecurity.org/insights/blog/clickfix-an-adaptive-social-engineering-technique
115 National Cyber Security Centre. (2025, October 14). NCSC annual review 2025: It's time to act. https://www.ncsc.gov.uk/files/ncsc annual-review-2025.pdf
116 National Cyber Security Centre. (2025, October 14). NCSC annual review 2025: It's time to act. https://www.ncsc.gov.uk/files/ncsc annual-review-2025.pdf
117 National Cyber Security Centre. (2025, October 14). NCSC annual review 2025: It's time to act. https://www.ncsc.gov.uk/files/ncsc annual-review-2025.pdf
118 National Cyber Security Centre. (2025, October 14). NCSC annual review 2025: It's time to act. https://www.ncsc.gov.uk/files/ncsc annual-review-2025.pdf
119 National Cyber Security Centre. (2025, October 14). NCSC annual review 2025: It's time to act. https://www.ncsc.gov.uk/files/ncsc annual-review-2025.pdf
120 National Cyber Security Centre. (2025, October 14). NCSC annual review 2025: It's time to act. https://www.ncsc.gov.uk/files/ncsc annual-review-2025.pdf
121 New Era Technology AU. (2025, October 24). Top 3 cyber incidents in Australia (October 2025 update). https://www.neweratech.com/au/blog/top-3-cyber-incidents-in-australia-october-2025-update/
122 New Era Technology AU. (2025, October 24). Top 3 cyber incidents in Australia (October 2025 update). https://www.neweratech.com/au/blog/top-3-cyber-incidents-in-australia-october-2025-update/
123 New Era Technology AU. (2025, October 24). Top 3 cyber incidents in Australia (October 2025 update). https://www.neweratech.com/au/blog/top-3-cyber-incidents-in-australia-october-2025-update/
124 New Era Technology AU. (2025, October 24). Top 3 cyber incidents in Australia (October 2025 update). https://www.neweratech.com/au/blog/top-3-cyber-incidents-in-australia-october-2025-update/
125 New Era Technology AU. (2025, October 24). Top 3 cyber incidents in Australia (October 2025 update). https://www.neweratech.com/au/blog/top-3-cyber-incidents-in-australia-october-2025-update/
126 The Cyber Express. (2025, October 28). CISA warns DELMIA Apriso vulnerabilities are under attack. https://thecyberexpress.com/delmia-apriso-vulnerabilities-under-attack/
127 The Cyber Express. (2025, October 28). CISA warns DELMIA Apriso vulnerabilities are under attack. https://thecyberexpress.com/delmia-apriso-vulnerabilities-under-attack/
128 Industrial Cyber. (2025, October 28). CISA issues ICS advisories on Schneider Electric, Vertikal Systems vulnerabilities; adds DELMIA Apriso flaws to KEV catalog. https://industrialcyber.co/cisa/cisa-issues-ics-advisories-on-schneider-electric-vertikal-systems vulnerabilities-adds-delmia-apriso-flaws-to-kev-catalog/
129 Industrial Cyber. (2025, October 28). CISA issues ICS advisories on Schneider Electric, Vertikal Systems vulnerabilities; adds DELMIA Apriso flaws to KEV catalog. https://industrialcyber.co/cisa/cisa-issues-ics-advisories-on-schneider-electric-vertikal-systems vulnerabilities-adds-delmia-apriso-flaws-to-kev-catalog/
130 Industrial Cyber. (2025, October 28). CISA issues ICS advisories on Schneider Electric, Vertikal Systems vulnerabilities; adds DELMIA Apriso flaws to KEV catalog. https://industrialcyber.co/cisa/cisa-issues-ics-advisories-on-schneider-electric-vertikal-systems vulnerabilities-adds-delmia-apriso-flaws-to-kev-catalog/
131 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
132 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
133 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
134 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
135 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
136 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
137 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
138 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
139 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
140 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
141 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
142 Cybersecurity News. (2025, October). Huge surge in fake investment platforms mimic Forex exchanges steal logins. https://cybersecuritynews.com/huge-surge-in-fake-investment-platforms/
143 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
144 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
145 The Hacker News. (2025, October). Qilin ransomware combines Linux payload with BYOVD exploit in hybrid attack. https://thehackernews.com/2025/10/qilin-ransomware-combines-linux-payload.html
146 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
147 Check Point Research. (2025, October 27). 27th October – threat intelligence report. https://research.checkpoint.com/2025/27th october-threat-intelligence-report/
148 Cybersecurity News. (2025, October). New Beast ransomware actively scans for active SMB port from breached system to spread across network. https://cybersecuritynews.com/new-beast-ransomware-actively-scans-for-active-smb-port/
149 Cybersecurity News. (2025, October). New Beast ransomware actively scans for active SMB port from breached system to spread across network. https://cybersecuritynews.com/new-beast-ransomware-actively-scans-for-active-smb-port/
150 Cybersecurity News. (2025, October). New Beast ransomware actively scans for active SMB port from breached system to spread across network. https://cybersecuritynews.com/new-beast-ransomware-actively-scans-for-active-smb-port/
151 Cybersecurity News. (2025, October). New Beast ransomware actively scans for active SMB port from breached system to spread across network. https://cybersecuritynews.com/new-beast-ransomware-actively-scans-for-active-smb-port/
152 Cybersecurity News. (2025, October). New Gentlemen's RaaS advertised on hacking forums targeting Windows, Linux and ESXi systems. https://cybersecuritynews.com/new-gentlemens-raas-advertised-on-hacking-forums/
153 Cybersecurity News. (2025, October). New Gentlemen's RaaS advertised on hacking forums targeting Windows, Linux and ESXi systems. https://cybersecuritynews.com/new-gentlemens-raas-advertised-on-hacking-forums/
154 Cybersecurity News. (2025, October). New Gentlemen's RaaS advertised on hacking forums targeting Windows, Linux and ESXi systems. https://cybersecuritynews.com/new-gentlemens-raas-advertised-on-hacking-forums/
Tags Threat intelligence