This week’s Cyber Intel Brief uncovers SonicWall cascade breaches, a record-breaking 11.5 Tbps botnet DDoS, and APT41’s latest espionage campaign.
13 September – 19 September 2025 | TLP: CLEAR
EXECUTIVE SUMMARY
Critical infrastructure experienced multiple significant security incidents during the collection period. Intelligence confirms cascading security failures in network infrastructure, with SonicWall's cloud portal breach exposing firewall configurations while Akira ransomware operators actively exploited unpatched SSL VPN vulnerabilities. Threat actors achieved record DDoS capabilities through a 300,000-router botnet generating 11.5 Tbps attacks, while software supply chains experienced the first successful self-replicating worm in the NPM ecosystem.
CRITICAL INCIDENTS
1. SonicWall Infrastructure Compromise Cascade
SonicWall disclosed a brute-force attack against its MySonicWall cloud portal affecting under 5% of customers, exposing encrypted firewall configuration backup files that could facilitate exploitation. The incident occurred simultaneously with a fresh surge of over 40 Akira ransomware attacks exploiting CVE-2024-40766 (CVSS 9.3) in SonicWall SSL VPN appliances. Analysis confirms attacks target LDAP misconfigurations and virtual office portals, with particular focus on Gen 6 to Gen 7 migrations where organizations failed to reset default passwords. The combination of configuration exposure and active vulnerability exploitation creates cascading risks across SonicWall's enterprise customer base.
2. Record-Breaking AISURU Botnet DDoS Attack
The AISURU botnet executed an 11.5 Tbps distributed denial-of-service attack using approximately 300,000 compromised routers worldwide. The botnet originated from Totolink router firmware hijacking in April 2025, growing to current scale by September through systematic compromise of consumer networking equipment. Attack methodology used GRE tunneling across multiple command-and-control servers with custom packet sequences designed to bypass legacy DDoS mitigation tools. The scale represents a significant increase in botnet capabilities, surpassing previous documented attack volumes and demonstrating the weaponization of Internet of Things devices at substantial scale.
3. NPM Supply Chain Self-Replicating Worm Attack
Security researchers discovered "Shai-Hulud," the first successful self-replicating worm in the NPM package ecosystem, compromising 180+ packages including 25 CrowdStrike modules. The malware deploys TruffleHog credential scanner to harvest AWS tokens, GitHub personal access keys, and NPM tokens, then creates persistent GitHub Actions workflows for ongoing data exfiltration. CrowdStrike confirmed rapid package removal and credential rotation, but the incident demonstrates successful execution of supply chain attacks with worm-like propagation capabilities. The attack creates "Shai-Hulud" repositories on GitHub containing exfiltrated secrets, indicating systematic credential harvesting operations.
ACTIVE THREAT ACTORS
Akira Ransomware Group
Akira ransomware operators demonstrated sustained high-activity levels with 977 known victims to date, while conducting a fresh surge of 40+ attacks specifically targeting SonicWall SSL VPN vulnerabilities. The group exploits CVE-2024-40766 combined with configuration errors, particularly in organizations that failed to reset passwords during firewall migrations. Intelligence indicates the group maintains sophisticated reconnaissance capabilities, identifying vulnerable systems through publicly accessible management interfaces. Analysis confirms dual AES-RSA encryption deployment and systematic targeting of LDAP group configurations for privilege escalation. The group's operational tempo suggests well-resourced infrastructure and dedicated exploitation teams.
TA415 (APT41/Brass Typhoon)
China-aligned APT group TA415 conducted targeted espionage campaign against U.S.-China economic relations experts using spoofed emails from the U.S.-China Business Council and House Committee members. The group deployed "WhirlCoil" Python loader establishing Visual Studio Code remote tunnels for persistent backdoor access, demonstrating evolution in command-and-control techniques. Campaign active July-August 2025 specifically targeted trade and economic policy specialists in government agencies, think tanks, and academic organizations. Technical analysis reveals abuse of Cloudflare WARP VPN infrastructure for traffic obfuscation and systematic targeting based on victims' policy expertise areas.
Shiny Hunters Cybercriminal Group
Shiny Hunters executed sophisticated attack against Kering luxury brands (Gucci, Balenciaga, Alexander McQueen), stealing 7.4 million customer records including detailed purchase histories showing individual spending up to $86,000. The attack leveraged compromised Salesforce OAuth tokens combined with social engineering techniques, following similar patterns from recent Cartier and Louis Vuitton compromises. Analysis indicates coordinated campaign specifically targeting luxury retail brands and wealthy customer bases for subsequent fraud operations. The group demonstrated advanced understanding of cloud application security and OAuth token manipulation, suggesting dedicated cloud exploitation capabilities.
TRENDS
Ransomware Activity Surge
Multiple indicators confirm increased ransomware activity during September 2025, with CardioFocus healthcare technology company compromised by Incransom group and sustained attacks across technology and healthcare sectors. Available evidence suggests 10-20% year-over-year increase in ransomware victims despite major law enforcement actions during summer 2025. Healthcare and critical infrastructure sectors experienced persistent threat actor focus, with technology sector showing continued targeting through multiple September 2025 incidents. Analysis of victim databases indicates geographic expansion with increased targeting of Asia-Pacific organizations by BlackNevas ransomware, which targets 50% of attacks at the region using dual AES-RSA encryption.
Government Industrial Control System Vulnerability Surge
CISA released 17 industrial control system advisories during the collection period, covering critical infrastructure vendors including Schneider Electric, Siemens, Hitachi Energy, and Westermo Network Technologies., Analysis shows systematic vulnerability disclosure patterns affecting energy, healthcare, and transportation sectors requiring immediate attention. Advisories span ICSA-25-261-01 through ICSA-25-261-07 and ICSA-25-259-01 through ICSA-25-259-07, with particular focus on SIMATIC NET, SCALANCE, and RUGGEDCOM industrial products. OpenSSL vulnerabilities in Siemens industrial products represent cross-cutting risks requiring coordinated patching across multiple product lines.
Supply Chain Attack Evolution
Software supply chain attacks demonstrate increasing sophistication with the emergence of self-replicating malware capabilities in trusted package repositories. Beyond the NPM worm attack, 40+ additional packages were compromised in coordinated campaigns affecting multiple maintainers and injecting credential-stealing malware. Attack patterns include bundle.js script injection that downloads credential scanners and creates persistent GitHub Actions workflows for ongoing data exfiltration. Analysis confirms targeting of developer environments to harvest AWS_ACCESS_KEY_ID, GITHUB_TOKEN, NPM_TOKEN, and other cloud credentials, indicating systematic compromise of development infrastructure.
VULNERABILITIES
Critical Patches Required This Month
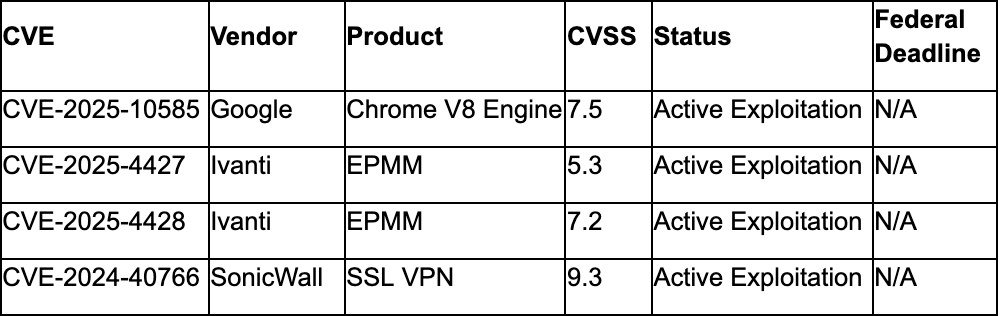
Continuing Active Exploitation
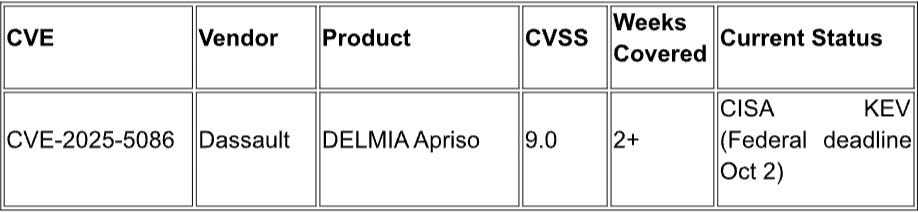
RECOMMENDATIONS
Immediate Actions (0-24 Hours)
- Emergency audit of all SonicWall deployments with immediate password resets and SSL VPN access restrictions
- Update Chrome to versions 140.0.7339.185/.186 (Windows/macOS) and 140.0.7339.185 (Linux) for CVE-2025-10585
- Audit development environments for affected NPM packages and rotate all npm tokens, GitHub personal access tokens immediately
- Review firewall configurations for unauthorized modifications and implement network segmentation for critical infrastructure systems
- CyberScoop. (2025, September 19). Attack on SonicWall's cloud portal exposes customers' firewall configurations. CyberScoop. https://cyberscoop.com/sonicwall-cyberattack-customer-firewall-configurations/
- CISA. (2025, September 18). CISA Releases Nine Industrial Control Systems Advisories. Alert. https://www.cisa.gov/news-events/alerts/2025/09/18/cisa-releases-nine-industrial-control-systems-advisories
- Wiz Research. (2025, September 16). Shai-Hulud npm supply chain attack. Wiz Blog. https://www.wiz.io/blog/shai-hulud-npm-supply-chain-attack
- CyberScoop. (2025, September 19). Attack on SonicWall's cloud portal exposes customers' firewall configurations. CyberScoop. https://cyberscoop.com/sonicwall-cyberattack-customer-firewall-configurations/
- CyberScoop. (2025, September 19). SonicWall firewalls targeted by fresh Akira ransomware surge. CyberScoop. https://cyberscoop.com/sonicwall-akira-ransomware-attacks-surge/
- Cybersecurity News. (2025, September 19). AISURU botnet with 300,000 hijacked routers behind the recent massive 11.5 Tbps DDoS attack. Cybersecurity News. https://cybersecuritynews.com/aisuru-botnet-with-300000-hijacked-routers/
- Wiz Research. (2025, September 16). Shai-Hulud npm supply chain attack. Wiz Blog. https://www.wiz.io/blog/shai-hulud-npm-supply-chain-attack
- Cybersecurity News. (2025, September 19). AISURU botnet with 300,000 hijacked routers behind the recent massive 11.5 Tbps DDoS attack. Cybersecurity News. https://cybersecuritynews.com/aisuru-botnet-with-300000-hijacked-routers/
- The Hacker News. (2025, September 19). Chinese TA415 uses VS Code remote tunnels to spy on U.S. economic policy experts. The Hacker News. https://thehackernews.com/2025/09/chinese-ta415-uses-vs-code-remote.html
- GB Hackers. (2025, September 19). Millions of customer records stolen in cyberattack on Gucci, Balenciaga, and Alexander McQueen. GB Hackers. https://gbhackers.com/records-stolen-gucci-balenciaga-alexander-mcqueen/
- Wiz Research. (2025, September 16). Shai-Hulud npm supply chain attack. Wiz Blog. https://www.wiz.io/blog/shai-hulud-npm-supply-chain-attack
- Cybersecurity News. (2025, September 19). BlackNevas ransomware encrypts files and steals sensitive data from affected companies. Cybersecurity News. https://cybersecuritynews.com/blacknevas-ransomware-encrypts-files/
- CyberScoop. (2025, September 19). Attack on SonicWall's cloud portal exposes customers' firewall configurations. CyberScoop. https://cyberscoop.com/sonicwall-cyberattack-customer-firewall-configurations/
- CISA. (2025, September 18). CISA Releases Nine Industrial Control Systems Advisories. Alert. https://www.cisa.gov/news-events/alerts/2025/09/18/cisa-releases-nine-industrial-control-systems-advisories
- Wiz Research. (2025, September 16). Shai-Hulud npm supply chain attack. Wiz Blog.https://www.wiz.io/blog/shai-hulud-npm-supply-chain-attack
- Cybersecurity News. (2025, September 19). AISURU botnet with 300,000 hijacked routers behind the recent massive 11.5 Tbps DDoS attack. Cybersecurity News. https://cybersecuritynews.com/aisuru-botnet-with-300000-hijacked-routers/
- CyberScoop. (2025, September 19). Attack on SonicWall's cloud portal exposes customers' firewall configurations. CyberScoop. https://cyberscoop.com/sonicwall-cyberattack-customer-firewall-configurations/
- The Hacker News. (2025, September 17). Google patches Chrome zero-day CVE-2025-10585 as active V8 exploit threatens millions. The Hacker News. https://thehackernews.com/2025/09/google-patches-chrome-zero-day-cve-2025.html
- Wiz Research. (2025, September 16). Shai-Hulud npm supply chain attack. Wiz Blog. https://www.wiz.io/blog/shai-hulud-npm-supply-chain-attack


