Stay up to date the most pressing cyber threats, emerging trends and what they mean for enterprise security, critical infrastructure and global risk.
Executive Summary
The week of July 19-25, 2025 was dominated by widespread exploitation of multiple Microsoft SharePoint zero-day vulnerabilities by Chinese nation-state actors. This campaign represents one of the most significant enterprise infrastructure threats observed this year, with over 400 confirmed compromises spanning federal agencies, critical infrastructure, and private sector organizations across 29 countries. Simultaneously, critical vulnerabilities in network access control systems (Cisco ISE) and managed file transfer platforms (CrushFTP) are under active exploitation, while the Interlock ransomware group escalated targeting of critical infrastructure sectors through sophisticated social engineering campaigns.
The convergence of nation-state espionage operations with ransomware deployment by Storm-2603 signals a concerning evolution in threat actor tactics, blending traditional intelligence collection with financially motivated destruction. Federal agencies face immediate compliance deadlines under BOD 22-01, with CISA adding six vulnerabilities to the Known Exploited Vulnerabilities catalog during this period. The scale and sophistication of these coordinated campaigns underscore the critical need for accelerated patch management and enhanced monitoring across all enterprise environments.
Analyst Comment: Basic security hygiene failures have enabled access to critical national infrastructure, requiring immediate resource allocation for emergency response.
Critical Incidents
1. US Nuclear Security Administration Compromise via SharePoint Zero-Day
The National Nuclear Security Administration (NNSA), responsible for maintaining and designing the nation's nuclear weapons cache, was confirmed breached via CVE-2025-53770 exploitation starting July 18, 2025.1 Additional federal agencies compromised include the National Institutes of Health (eight SharePoint servers affected), Department of Homeland Security, and Department of Education.2 The California Independent System Operator, which operates most of California's electric grid, was also targeted but successfully contained the threat with no operational impact.3 While officials stated no sensitive or classified information was compromised at NNSA, the breach demonstrates successful nation-state targeting of the nation's most critical security infrastructure.4
Analyst Comment: The successful compromise of nuclear weapons oversight infrastructure represents a serious breach of critical national security assets.
2. Microsoft SharePoint Zero-Day Exploitation Campaign by Chinese APT Groups
Chinese nation-state actors have successfully exploited critical SharePoint vulnerabilities (CVE-2025-53770, CVE-2025-53771, CVE-2025-49704, CVE-2025-49706) in a campaign dubbed "ToolShell," compromising over 400 organizations globally across government, telecommunications, and software sectors.5 The campaign, active since July 7, 2025, affects only on-premises SharePoint servers and enables unauthenticated remote code execution, allowing attackers to extract cryptographic keys and establish persistent access through webshell deployment.6 Storm-2603 has uniquely combined espionage objectives with Warlock ransomware deployment, indicating convergence of state-sponsored and financially motivated operations.7
Analyst Comment: The scale and coordination of this campaign represents perhaps the most significant enterprise infrastructure compromise observed this year, requiring fundamental reassessment of SharePoint security postures.
3. UK Co-op Retail Giant Data Breach Affects 6.5 Million Customers
UK retail giant Co-op officially disclosed a cyber-attack resulting in theft of personal data from all 6.5 million customers, following a massive breach in April that led to system shutdowns and food shortages.8 The attack exposed contact information but not financial data, with the Scattered Spider threat group suspected of responsibility.9 This group is known for deploying DragonForce ransomware and represents a significant evolution in retail sector targeting capabilities.10 The attack's operational impact included widespread supply chain disruptions affecting food distribution networks across the UK.11
Analyst Comment: The combination of massive customer data exposure with operational supply chain disruption demonstrates escalating threat actor capabilities in targeting critical retail infrastructure.
4. Thailand Ministry of Labor Ransomware Attack with Government Data Theft
Thailand's Ministry of Labor experienced a sophisticated cyber-attack by the Devman ransomware group (linked to DragonForce) resulting in website defacement, alleged theft of 300GB of sensitive data, and encryption of 2,000 laptops and dozens of servers.12 The attack potentially exposed citizen data and classified government documents, with attackers demanding a $15 million ransom for data recovery and non-disclosure.13 The incident represents escalating targeting of Southeast Asian government infrastructure by international ransomware operations.14
Analyst Comment: The systematic targeting of government infrastructure in Thailand indicates expanding ransomware group geographic reach and sophisticated understanding of regional government dependencies.
5. CrushFTP Zero-Day Administrative Takeover Campaign
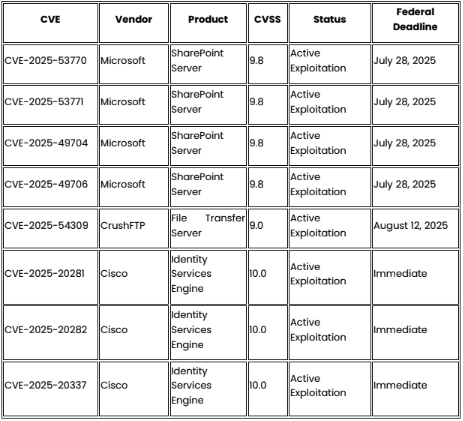
A critical zero-day vulnerability (CVE-2025-54309, CVSS 9.0) in CrushFTP managed file transfer platforms has been actively exploited since July 18, 2025, enabling threat actors to gain administrative access on over 10,000 vulnerable instances globally.15 The vulnerability stems from mishandled AS2 validation when DMZ proxy features are not configured, allowing remote attackers to achieve admin privileges via HTTPS interface manipulation.16 CISA added this vulnerability to the Known Exploited Vulnerabilities catalog on July 22, 2025, with federal agencies required to remediate by August 12, 2025.17
Analyst Comment: This represents CrushFTP's third critical zero-day in 15 months, indicating systemic security development issues requiring enhanced vendor oversight for critical infrastructure applications.
6. Dell Customer Solution Centers Platform Breach by World Leaks
World Leaks (rebranded Hunters International) breached Dell's Customer Solution Centers platform, stealing 1.3TB of data containing 416,103 files.18 Dell maintains the compromised data is "primarily synthetic (fake) data" used for product demonstrations, though the breach demonstrates sophisticated targeting of enterprise demonstration environments.19 World Leaks represents a significant shift in extortion tactics, abandoning ransomware deployment and focusing solely on data exfiltration and extortion, citing reduced profitability and increased operational risks associated with encryption-based attacks.20
Analyst Comment: The evolution toward pure data exfiltration models indicates threat actor adaptation to improved backup and recovery capabilities, requiring enhanced data loss prevention strategies.
Active Threat Actors
Chinese Nation-State Actor Consortium (Linen Typhoon, Violet Typhoon, Storm 2603)
These Chinese APT groups demonstrated unprecedented coordination in exploiting SharePoint vulnerabilities, with Linen Typhoon and Violet Typhoon focusing on traditional espionage while Storm-2603 deployed both Warlock and LockBit ransomware.21 The actors operate from IP addresses 104.238.159[.]149, 107.191.58[.]76, and 96.9.125[.]147, with one address previously linked to Ivanti EPMM exploitation.22 Their advanced capabilities include in-memory .NET module execution to avoid file-based artifacts and sophisticated machine key extraction techniques for persistent authentication bypass.23
Interlock Ransomware Group
This sophisticated cybercriminal organization has escalated targeting of critical infrastructure across North America and Europe, employing drive-by downloads from compromised legitimate websites and innovative "ClickFix" social engineering techniques.24 The group utilizes AnyDesk, Cobalt Strike, and SystemBC for persistence while implementing double extortion models that encrypt systems and exfiltrate sensitive data.25 FBI investigations indicate active operations as recently as June 2025, with the group demonstrating advanced understanding of critical infrastructure operations and dependencies.26
Iranian Ministry of Intelligence and Security (MOIS) - MuddyWater APT
Four new Android spyware variants (DCHSpy) emerged targeting Iranian dissidents and activists through fake VPN applications disguised as "Earth VPN" and "Comodo VPN".27 The campaigns exploit geopolitical tensions and Starlink internet service activation during government-imposed blackouts, collecting WhatsApp data, location information, call logs, and conducting audio/video surveillance.28 The timing coincides with Iran's crackdown following Israel-Iran hostilities, demonstrating state-sponsored surveillance capabilities targeting civil society.29
Trends
Zero-Day Exploitation Timeline Acceleration
Flashpoint analysis reveals 54% of prioritized vulnerabilities in H1 2025 had exploits available or were actively exploited, with the average time from disclosure to exploit availability decreasing to less than one day.30 Analysis confirms 97% of vulnerabilities with exploit information already had exploits available at disclosure, indicating pre-disclosure vulnerability research and development by threat actors.31 Microsoft Windows, Google Chrome, and Zoom vulnerabilities remained without CVE assignments for over 90 days in multiple cases, creating intelligence gaps for defensive planning.32
Analyst Comment: The collapse of exploitation timelines eliminates traditional patching windows and requires fundamental shifts toward preventive security architectures and zero trust implementation.
Global Cyber Attack Volume Surge
Check Point Research documented a 21% year-over-year increase in global weekly cyber attacks per organization in Q2 2025, reaching 1,984 attacks with the education sector remaining most targeted.33 Europe experienced the highest regional growth at 22%, while approximately 1,600 ransomware incidents were disclosed in Q2 2025, primarily affecting business services, manufacturing, and construction sectors.34 North America and Europe accounted for 53% and 25% of ransomware cases respectively, indicating persistent targeting of Western economies.35
Analyst Comment: The sustained increase in attack frequency combined with shortened exploitation timelines creates compounding defensive challenges requiring automated response capabilities and enhanced threat intelligence integration.
Critical Infrastructure Ransomware Convergence
Multiple ransomware groups demonstrated enhanced critical infrastructure targeting capabilities, with Qilin ransomware claiming a record 89 victims in July 2025 while adding "Call Lawyer" features to their affiliate panels for victim pressure tactics.36 DragonForce completed their "Devman 2.0" RaaS platform with ransom demands ranging from $60,000 to $10 million, while targeting government entities including Thailand's Ministry of Labor with 300GB data theft claims.37 Singapore's critical infrastructure faced coordinated attacks by UNC3886 across defense, technology, and telecommunications sectors.38
Analyst Comment: The professionalization of ransomware operations with legal pressure tactics and systematic critical infrastructure targeting indicates threat actors are adapting to law enforcement pressure while escalating operational impact.
Vulnerabilities
Critical Patches Required This Week
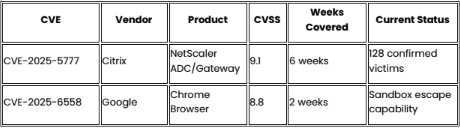
Continuing Active Exploitation
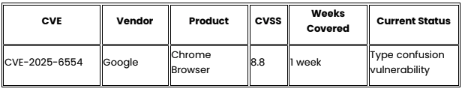
Recommendations
Immediate Actions (0-24 Hours)
- Disconnect all internet-facing SharePoint servers or implement emergency AMSI mitigations pending patching completion
- Execute emergency patching for SharePoint CVE-2025-53770/53771/49704/49706 with mandatory ASP.NET machine key rotation and IIS restart
- Audit all Cisco ISE installations (versions 3.3-3.4) and apply critical patches for CVE-2025-20281/20282/20337
- Verify CrushFTP installations are updated to versions 10.8.5_12 or 11.3.4_26
- Deploy network monitoring for IOCs: 104.238.159[.]149, 107.191.58[.]76, 96.9.125[.]147
- Implement enhanced monitoring for spinstall0.aspx webshell deployment on SharePoint environments
- Review customer data protection measures following major retail and enterprise data breaches
- Assess government data handling procedures in light of Southeast Asian ministry targeting
- Nakashima, E. (2025, July 23). U.S. nuclear and health agencies hit in Microsoft SharePoint breach. The Washington Post. https://www.washingtonpost.com/technology/2025/07/23/sharepoint-microsoft-hack-nih-nnsa/
- Nakashima, E. (2025, July 23). U.S. nuclear and health agencies hit in Microsoft SharePoint breach. The Washington Post. https://www.washingtonpost.com/technology/2025/07/23/sharepoint-microsoft-hack-nih-nnsa/
- Nakashima, E. (2025, July 23). U.S. nuclear and health agencies hit in Microsoft SharePoint breach. The Washington Post. https://www.washingtonpost.com/technology/2025/07/23/sharepoint-microsoft-hack-nih-nnsa/
- Nakashima, E. (2025, July 23). U.S. nuclear and health agencies hit in Microsoft SharePoint breach. The Washington Post. https://www.washingtonpost.com/technology/2025/07/23/sharepoint-microsoft-hack-nih-nnsa/
- Microsoft Security Response Center. (2025, July 22). Disrupting active exploitation of on-premises SharePoint vulnerabilities. Microsoft Security Blog. https://www.microsoft.com/en-us/security/blog/2025/07/22/disrupting-active-exploitation-of-on-premises-sharepoint-vulnerabilities/
- Cybersecurity and Infrastructure Security Agency. (2025, July 20). Microsoft releases guidance on exploitation of SharePoint vulnerabilities [Alert]. https://www.cisa.gov/news-events/alerts/2025/07/20/update-microsoft-releases-guidance-exploitation-sharepoint-vulnerabilities
- Unit 42. (2025, July 24). Active exploitation of Microsoft SharePoint vulnerabilities: Threat brief. Palo Alto Networks. https://unit42.paloaltonetworks.com/microsoft-sharepoint-cve-2025-49704-cve-2025-49706-cve-2025-53770/
- Check Point Research. (2025, July 21). 21st July – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/21st-july-threat-intelligence-report/
- Check Point Research. (2025, July 21). 21st July – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/21st-july-threat-intelligence-report/
- Check Point Research. (2025, July 21). 21st July – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/21st-july-threat-intelligence-report/
- Check Point Research. (2025, July 21). 21st July – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/21st-july-threat-intelligence-report/
- Check Point Research. (2025, July 21). 21st July – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/21st-july-threat-intelligence-report/
- Check Point Research. (2025, July 21). 21st July – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/21st-july-threat-intelligence-report/
- Check Point Research. (2025, July 21). 21st July – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/21st-july-threat-intelligence-report/
- Toulas, B. (2025, July 18). New CrushFTP zero-day exploited in attacks to hijack servers. BleepingComputer. https://www.bleepingcomputer.com/news/security/new-crushftp-zero-day-exploited-in-attacks-to-hijack-servers/
- SecurityOnline. (2025, July 18). CVE-2025-54309: CrushFTP targeted in active exploits due to unpatched zero-day vulnerability. SecurityOnline. https://securityonline.info/cve-2025-54309-crushftp-targeted-in-active-exploits-due-to-unpatched-zero-day-vulnerability/
- Cybersecurity and Infrastructure Security Agency. (2025, July 22). CISA adds four known exploited vulnerabilities to catalog [Alert]. https://www.cisa.gov/news-events/alerts/2025/07/22/cisa-adds-four-known-exploited-vulnerabilities-catalog
- Toulas, B. (2025, July 21). Dell confirms breach of test lab platform by World Leaks extortion group. BleepingComputer. https://www.bleepingcomputer.com/news/security/dell-confirms-breach-of-test-lab-platform-by-world-leaks-extortion-group/
- CyberSecurityNews. (2025, July 21). Dell data breach - test lab platform hacked by World Leaks group. CyberSecurityNews. https://cybersecuritynews.com/dell-data-breach/
- Toulas, B. (2025, July 21). Dell confirms breach of test lab platform by World Leaks extortion group. BleepingComputer. https://www.bleepingcomputer.com/news/security/dell-confirms-breach-of-test-lab-platform-by-world-leaks-extortion-group/
- Microsoft Security Response Center. (2025, July 22). Disrupting active exploitation of on-premises SharePoint vulnerabilities. Microsoft Security Blog. https://www.microsoft.com/en-us/security/blog/2025/07/22/disrupting-active-exploitation-of-on-premises-sharepoint-vulnerabilities/
- Lakshmanan, R. (2025, July 22). Critical unpatched SharePoint zero-day actively exploited, breaches 75+ company servers. The Hacker News. https://thehackernews.com/2025/07/critical-microsoft-sharepoint-flaw.html
- SentinelOne. (2025, July 22). SharePoint ToolShell | Zero-day exploited in-the-wild targets enterprise servers. SentinelOne Blog. https://www.sentinelone.com/blog/sharepoint-toolshell-zero-day-exploited-in-the-wild-targets-enterprise-servers/
- Cybersecurity and Infrastructure Security Agency. (2025, July 22). #StopRansomware: Interlock [Cybersecurity Advisory AA25-203A]. https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-203a
- Cybersecurity and Infrastructure Security Agency. (2025, July 22). #StopRansomware: Interlock [Cybersecurity Advisory AA25-203A]. https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-203a
- Cybersecurity and Infrastructure Security Agency. (2025, July 22). #StopRansomware: Interlock [Cybersecurity Advisory AA25-203A]. https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-203a
- Lakshmanan, R. (2025, July 21). Iran-linked DCHSpy Android malware masquerades as VPN apps to spy on dissidents. The Hacker News. https://thehackernews.com/2025/07/iran-linked-dchspy-android-malware.html
- Goodin, D. (2025, July 21). 4 new Android spyware samples linked to Iran's intel agency. The Register. https://www.theregister.com/2025/07/21/muddywaters_android_iran/
- Cimpanu, C. (2025, July 21). Iranian APT targets Android users with new variants of DCHSpy spyware. SecurityWeek. https://www.securityweek.com/new-variants-of-dchspy-spyware-used-by-iranian-apt-to-target-android-users/
- Flashpoint. (2025, July 24). Part 2: Vulnerability insights and prioritization report 2025 H1 analysis. Flashpoint Blog. https://flashpoint.io/blog/vulnerability-insights-priotiziation-midyear-review-part-2/
- Flashpoint. (2025, July 24). Part 2: Vulnerability insights and prioritization report 2025 H1 analysis. Flashpoint Blog. https://flashpoint.io/blog/vulnerability-insights-priotiziation-midyear-review-part-2/
- Flashpoint. (2025, July 24). Part 2: Vulnerability insights and prioritization report 2025 H1 analysis. Flashpoint Blog. https://flashpoint.io/blog/vulnerability-insights-priotiziation-midyear-review-part-2/
- Check Point Research. (2025, July 21). 21st July – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/21st-july-threat-intelligence-report/
- Check Point Research. (2025, July 21). 21st July – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/21st-july-threat-intelligence-report/
- Check Point Research. (2025, July 21). 21st July – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/21st-july-threat-intelligence-report/
- Bitdefender. (2025, July 25). Bitdefender threat debrief | July 2025. Bitdefender Blog. https://www.bitdefender.com/en-us/blog/businessinsights/bitdefender-threat-debrief-july-2025
- Bitdefender. (2025, July 25). Bitdefender threat debrief | July 2025. Bitdefender Blog. https://www.bitdefender.com/en-us/blog/businessinsights/bitdefender-threat-debrief-july-2025
- Check Point Research. (2025, July 21). 21st July – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/21st-july-threat-intelligence-report/