Stay up to date the most pressing cyber threats, emerging trends and what they mean for enterprise security, critical infrastructure and global risk.
Classification: TLP: CLEAR
Executive Summary
This week’s cybersecurity landscape includes escalating threats across multiple domains. 120+ Iranian nation-state and hacktivist groups are conducting systematic attacks following the U.S. bombing of Iranian nuclear facilities. Critical infrastructure faces another round of increased vulnerabilities as CISA released ten new Industrial Control System advisories. Russian VetIS food supply system encountered disruption, while ransomware operations surged 126% year-over-year with 2,289 confirmed Q1 2025 victims. Finally, the suspension of the Critical Infrastructure Partnership Advisory Council (CIPAC) is degrading public-private intelligence sharing during a period of elevated threats.
Analyst Comment: Organizations face convergent threats requiring immediate action, including enhanced monitoring for Iranian indicators through September 2025 and emergency patching for ten new ICS vulnerabilities.
Top Stories
1. Iranian Cyber Actors Coordinate Large-Scale Campaign
The Department of Homeland Security issued National Terrorism Advisory System Bulletin on June 22, 2025, confirming heightened threat environment through September 22, 2025. Since then, we have seen 120+ Iranian-aligned hacktivist groups reportedly conducting coordinated attacks against U.S. networks.1 There has also reportedly been a 700% increase in cyberattacks on Israel since the June 12 Israeli strikes2 on Iran while the Iranian threat group Agent Serpens (CharmingKitten) has reportedly deployed AI-enhanced social engineering via malicious PDFs masquerading as RAND documents.3Iranian government-affiliated actors and hacktivist proxies are also reportedly systematically targeting poorly secured U.S. networks with DDoS campaigns, data wipers, and coordinated network compromises.4
Analyst Comment: This represents the largest Iranian cyber mobilization since 2020, requiring enhanced defensive posturing across critical infrastructure sectors with particular attention to poorly secured networks and Internet-connected devices.
2. Critical Infrastructure Faces Compound Attack and Vulnerability Exposure
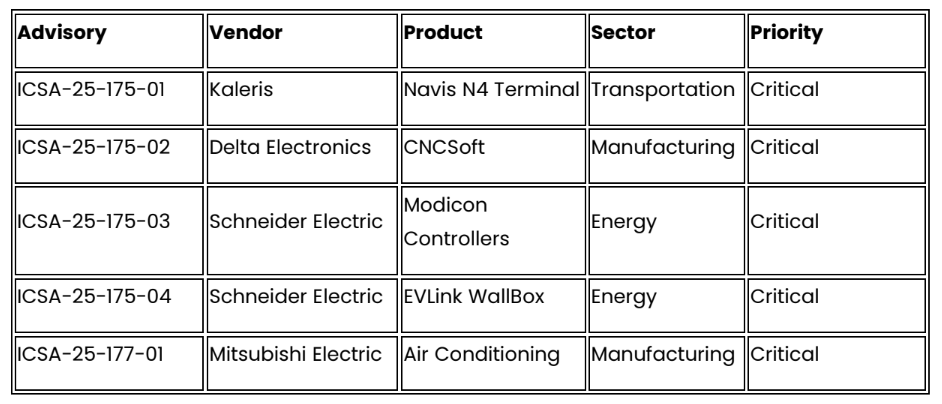
VetIS, the Russian federal veterinary surveillance system, suffered a cyberattack that forced businesses to revert to paper-based certification and halted deliveries to major retailers including Lenta and Yandex Lavka. Concurrently, CISA released ten Industrial Control System advisories June 24-26, 2025, affecting energy (Schneider Electric Modicon Controllers, EVLink charging), transportation (Kaleris Navis N4 maritime terminals), and manufacturing (Delta Electronics CNCSoft, Mitsubishi Electric systems) sectors.5 Finally, researchers identified 300+ exposed Human Machine Interfaces serving 26.6 million people. Thankfully, a coordinated response with the EPA has already reduced that number to fewer than 20 as of this reporting.6
Analyst Comment: The convergence of active infrastructure attacks and mass vulnerability disclosure creates compound threats requiring emergency patching, network segmentation, and enhanced monitoring for both criminal and nation-state targeting.
3. Major Data Breaches and Financial Crimes Demonstrate Global Threat Actor Success
Multiple high-impact breaches this week have affected millions of people, including a reported breach of Aflac insurance that involves the personal health data and Social Security numbers of users across the U.S. and Japan. In other breach news, a recent Zoomcar compromise affects 8.4 million users' personal information, while Israeli hackers (Predatory Sparrow) conducted an attack on the Iranian Bank Sepah that disrupted customer services and gas station transactions.7
Analyst Comment: The scale and coordination of these breaches indicates sophisticated threat actor capabilities across criminal, hacktivist, and nation-state operations, requiring enhanced third-party risk assessment and supply chain security protocols.
Top Threats
APT 33
APT33 (Elfin): APT33, also known as Elfin, is an Iranian state-sponsored threat actor conducting cyberespionage activities since at least 2013, typically using commodity malware and possessing an expansive network infrastructure that enables them to scale operations for victim targeting, with historical focus on aerospace, defense, and oil and gas industries.8
Recent 2024 activities include compromising control systems of a European power plant, conducting supply chain attacks against Fortune 500 companies through widely-used network management software, and collaborating with ransomware groups to provide initial access to healthcare providers.9 Over the past three months, Recorded Future's Insikt Group observed an increase in APT33's infrastructure building and targeting activity.10
APT 34
APT34 (OilRig): APT34, also known as OilRig, is a sophisticated state-sponsored cyber threat group with suspected ties to Iran's Ministry of Intelligence and Security (MOIS), active since at least 2014.11 ESET researchers recently identified three new malware downloaders (ODAgent, OilCheck and OilBooster) deployed against Israeli targets, including healthcare, manufacturing and local government organizations, underscoring OilRig's persistence in targeting the same organizations to maintain network footholds.12 Recently, APT34 has intensified its attacks on critical infrastructure in the Middle East, signaling a continued emphasis on exploiting vulnerabilities in these geopolitically sensitive regions.13
APT 35
APT35 (Charming Kitten): APT35, also known as Charming Kitten, is a state-sponsored Iranian cyber threat group active since at least 2013, operating under the direction of the Islamic Revolutionary Guard Corps (IRGC) and specializing in cyber espionage, credential theft, surveillance, and influence operations.14 Check Point observed a new wave of attacks starting mid-June 2025 following the outbreak of the Iran-Israel war that targeted Israeli individuals using fake meeting decoys and AI-driven phishing campaigns.15 Since 2021, the group has evolved beyond relying solely on social engineering, developing custom tools such as BELLACIAO and HYPERSCRAPER, and gained ability to quickly weaponize known vulnerabilities within the first day of going public.16
Trends
Ransomware Operations Surge with Increased Sophistication
Current data reveals 2,289 ransomware victims in Q1 2025, representing 126% year-over-year increase, while SafePay ransomware emerged as top threat actor with 58 victims in May 2025. Industrial ransomware targeting has accelerated, with 708 incidents affecting manufacturing, transportation, and engineering sectors, while Cl0p operations surged from two incidents in Q4 2024 to 154 incidents in Q1 2025 through Cleo Managed File Transfer exploitation. FunkSec demonstrates AI-driven malware with intermittent encryption and sophisticated code obfuscation, while traditional encryption-focused attacks shift toward data-only extortion methods.17
Analyst Comment: The ransomware ecosystem demonstrates enhanced targeting sophistication and operational resilience, requiring organizations to prioritize data protection alongside system recovery capabilities and assume prolonged exposure during complex recovery operations.
Vulnerabilities
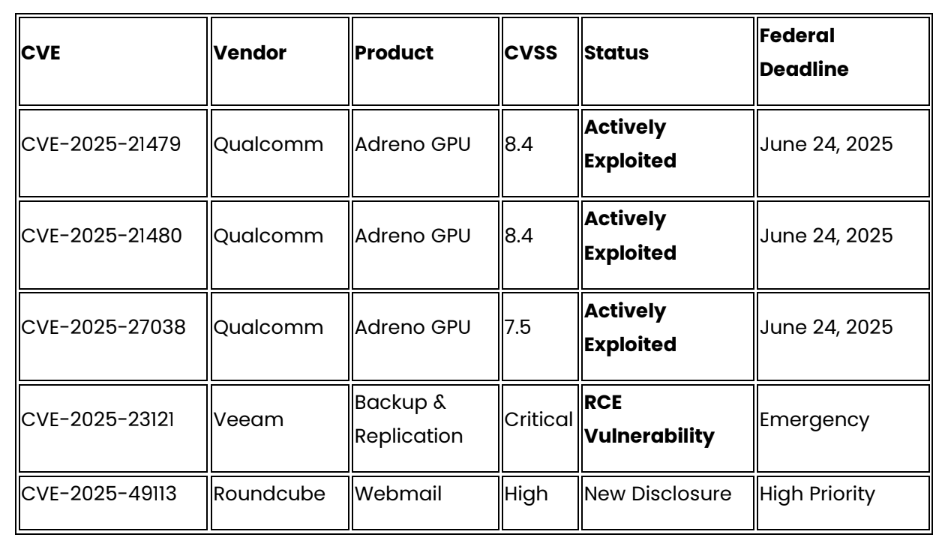
Critical Patches Required This Month (June 2025)
New Industrial Control System Advisories (June 24-26, 2025)
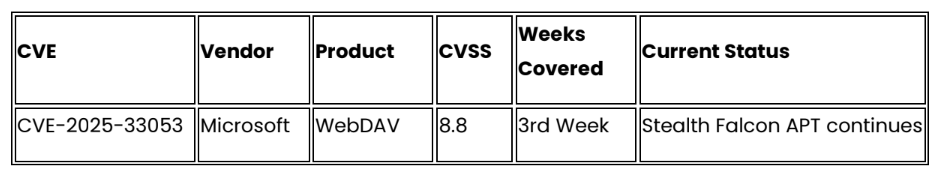
Continuing Active Exploitation (Previous Coverage)
Recommendations
Immediate Actions (0-24 Hours)
- Deploy emergency patches for actively exploited Qualcomm GPU vulnerabilities (CVE 2025-21479, CVE-2025-21480, CVE-2025-27038) across all Android device fleets and embedded systems
- Implement enhanced monitoring for Iranian hacktivist indicators including DDoS preparation, unusual network traffic patterns, and cryptocurrency infrastructure targeting through September 22, 2025
- Secure backup infrastructure by implementing Veeam Backup & Replication patches (CVE-2025-23121) and validating backup system isolation from production networks
- Conduct non-human identity audit focusing on API tokens, service accounts, and machine credentials with enhanced monitoring for unauthorized access patterns
References
- Department of Homeland Security. (2025, June 22). National terrorism advisory system bulletin - issued June 22, 2025. U.S. Department of Homeland Security. https://www.dhs.gov/ntas/advisory/national-terrorism-advisory system-bulletin-june-22-2025
- The Jerusalem Post. (2025, June 17). Cyberattacks against Israel increase since start of Iran conflict. The Jerusalem Post. https://www.jpost.com/business-and-innovation/tech-and-start-ups/article-857790
- 3 Unit 42. (2025, June 26). Threat brief: Escalation of cyber risk related to Iran. Palo Alto Networks. https://unit42.paloaltonetworks.com/iranian-cyberattacks-2025/
- Unit 42. (2025, June 26). Threat brief: Escalation of cyber risk related to Iran. Palo Alto Networks. https://unit42.paloaltonetworks.com/iranian-cyberattacks-2025/
- Cybersecurity and Infrastructure Security Agency. (2025, June 24-26). CISA releases industrial control systems advisories. CISA Alerts. https://www.cisa.gov/news-events/cybersecurity-advisories
- SecurityWeek. (2025, June 6). Misconfigured HMIs expose US water systems to anyone with a browser. SecurityWeek. https://www.securityweek.com/misconfigured-hmis-expose-us-water-systems-to-anyone-with-a-browser/
- Check Point Research. (2025, June 23). 23rd June – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/23rd-june-threat-intelligence-report/
- Recorded Future. (2024, November 6). Iranian Threat Actor Amasses Large Cyber Operations Infrastructure Network to Target Saudi Organizations. https://www.recordedfuture.com/research/iranian-cyber-operations-infrastructure
- Kiledjian. (2024, September 9). Iranian Cyber APT Groups: A Growing and Sophisticated Threat. Insights For Success. https://www.kiledjian.com/main/2024/8/30/iranian-cyber-apt-groups-a-growing-and-sophisticated-threat
- Recorded Future. (2024, November 6). Iranian Threat Actor Amasses Large Cyber Operations Infrastructure Network to Target Saudi Organizations. https://www.recordedfuture.com/research/iranian-cyber-operations-infrastructure
- Iranian Cyber Group OilRig Targets Iraqi Government in Sophisticated Malware Attack. (2024, September 12). The Hacker News. https://thehackernews.com/2024/09/iranian-cyber-group-oilrig-targets.html
- Korolov, M. (n.d.). Iran-linked hackers develop new malware downloaders to infect victims in Israel. The Record from Recorded Future News. https://therecord.media/oilrig-apt34-iran-linked-hackers-new-downloaders-israel
- Inside APT34 (OilRig): Tools, Techniques, and Global Cyber Threats. (2025, January 29). Trustwave. https://www.trustwave.com/en-us/resources/blogs/trustwave-blog/inside-apt34-oilrig-tools-techniques-and-global-cyber-threats/
- Charming Kitten. (2025, June 20). Wikipedia. https://en.wikipedia.org/wiki/Charming_Kitten
- 15 Iranian APT35 Hackers Targeting Israeli Tech Experts with AI-Powered Phishing Attacks. (2025, June 26). The Hacker News. https://thehackernews.com/2025/06/iranian-apt35-hackers-targeting-israeli.html
- Actor profile - Charming Kitten/APT35 - Highlights. (n.d.). Hunt & Hackett. https://www.huntandhackett.com/threats/actors/charming-kitten
- Check Point Software Technologies. (2025). FunkSec ransomware: AI-powered group. Check Point Cyber Hub. https://www.checkpoint.com/cyber-hub/threat-prevention/ransomware/funksec-ransomware-ai-powered-group/