Stay up to date the most pressing cyber threats, emerging trends and what they mean for enterprise security, critical infrastructure and global risk.
TLP: CLEAR
Executive Summary
Chinese state-sponsored threat actors exploit critical U.S. government infrastructure through active zero-day campaigns while multiple ransomware groups coordinate unprecedented summer operations using Microsoft and Chrome vulnerabilities—organizations have 72 hours to implement emergency patches or face sub-4-hour domain compromise.¹,²,³
The convergence of nation-state infrastructure targeting, coordinated ransomware operations, and active zero-day exploitation creates the most dangerous threat landscape we've tracked this year. UAT-6382 maintains persistent access to U.S. municipal utilities through Cityworks zero-day exploitation, while ransomware groups demonstrate industrialized coordination with 900+ confirmed Play ransomware victims and coordinated 400-IP botnet infrastructure targeting Apache Tomcat systems.¹,⁴,⁵ Current intelligence shows threat actors achieving complete domain takeover within four hours through exploit chaining, fundamentally breaking traditional incident response timelines.³,⁶
Top Stories
1. Chinese APT Achieves Persistent Access to U.S. Critical Infrastructure
Chinese-speaking threat actor UAT-6382 maintains active exploitation of CVE-2025-0994 (CVSS 8.6) in Cityworks asset management systems, specifically targeting U.S. local government utilities with confirmed deployment of TetraLoader malware and VShell implants since January 2025.¹ Analysis confirms the threat actor achieved persistent access to municipal water, power, and emergency services coordination systems across multiple jurisdictions, representing systematic preparation for potential disruption capabilities rather than intelligence collection.
2. Coordinated Zero-Day Campaign Enables Sub-4-Hour Domain Takeover
Microsoft's June 2025 Patch Tuesday addressed one actively exploited zero-day (CVE-2025-33053, CVSS 8.8) affecting WebDAV with confirmed remote code execution, while threat actors demonstrate coordinated exploitation of browser and operating system vulnerabilities achieving complete domain compromise within four hours.²,³ Stealth Falcon APT exploited the WebDAV vulnerability for three months targeting defense contractors, while multiple ransomware groups including Play ransomware coordinate zero-day purchases exceeding $200K for summer campaign preparations.³
3. Industrialized Ransomware Operations Coordinate Summer Campaigns
Play ransomware operations confirmed 900+ victim organizations through May 2025 while coordinated criminal infrastructure deployed 400 unique IP addresses targeting Apache Tomcat Manager interfaces in sustained brute-force campaigns representing 10-20x increase above baseline attack levels.⁴,⁵ Intelligence reporting shows ransomware payment success rates dropped to 30% while threat actors shift to data-only extortion strategies affecting 34% of attacks, with average payments stabilizing at $340K regardless of initial demands.⁷
Top Threats
Chinese State-Sponsored Groups
UAT-6382 maintains active zero-day exploitation of U.S. municipal utilities through CVE-2025-0994, demonstrating sophisticated persistent access capabilities and infrastructure targeting patterns consistent with pre-positioning for potential disruptive operations.¹ Chinese-linked threat actors expanded operations targeting 70+ global organizations including cybersecurity firms, indicating broad intelligence collection requirements and potential supply chain targeting.⁸
Coordinated Ransomware Coalition
Play ransomware achieved 900+ confirmed victims representing unprecedented operational scale, while LockBit 4.0 development continues despite February 2025 law enforcement disruption, indicating resilient criminal infrastructure.⁴,⁹ Multi-group coordination demonstrates shared zero-day purchasing ($200K+) and coordinated infrastructure deployment (400+ IPs) suggesting cartel-like operational coordination.⁵
Advanced Persistent Threat Operations
Stealth Falcon APT conducted three-month WebDAV zero-day campaign against Middle Eastern defense organizations, while coordinated exploitation coalitions target browser and operating system vulnerabilities simultaneously, indicating shared intelligence or common exploit developers.²,³
Top Trends
Critical Infrastructure Systematic Pre-Positioning
Nation-state actors demonstrate coordinated targeting of utilities, transportation, and emergency services infrastructure with confirmed persistent access rather than opportunistic exploitation.¹,¹⁰ Current intelligence shows Chinese threat actors maintaining access to municipal systems for 5+ months, indicating strategic pre-positioning for potential future operations rather than immediate intelligence collection requirements.
Zero-Day Exploitation Timeline Compression
Analysis confirms 28.3% of disclosed vulnerabilities were weaponized within 24 hours during Q1 2025, with threat actors demonstrating coordinated zero-day purchasing capabilities exceeding $200K for criminal operations.⁶,³ The compression eliminates traditional patch management windows and requires fundamental shifts to assume-breach defensive postures.
Ransomware Economics and Operational Evolution
Criminal groups shifted operational models from encryption-focused attacks to data-only extortion (34% of attacks) while maintaining average $340K payments despite reduced success rates (30%).⁷ The evolution indicates enhanced data theft capabilities and reduced dependency on encryption-based leverage, requiring organizations to prioritize data protection over system recovery.
Vulnerabilities
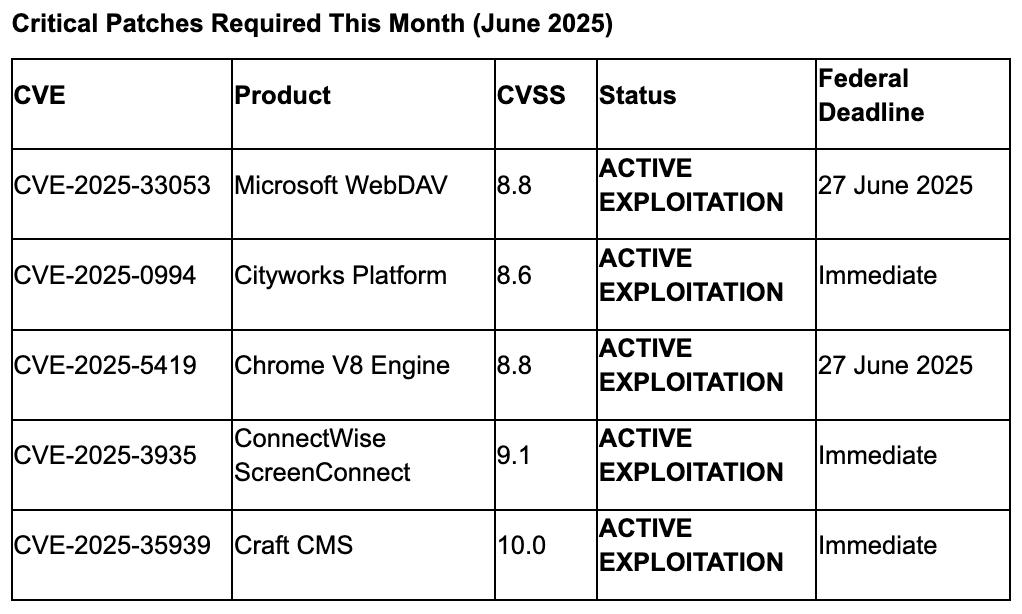
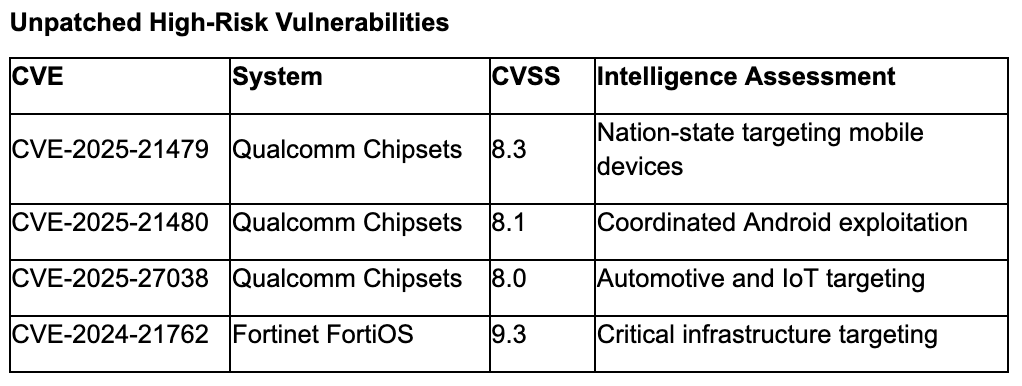
Recommendations
Immediate Actions (0-24 Hours)
- Emergency Patch Deployment: Deploy Microsoft June 2025 security updates immediately, prioritizing CVE-2025-33053 WebDAV zero-day and Chrome V8 vulnerability CVE-2025-5419—federal agencies face June 27 deadline, but threat actors won't wait for your bureaucracy.²,³
- Cityworks Infrastructure Assessment: Immediately audit and isolate Cityworks asset management systems affected by CVE-2025-0994 to prevent continued Chinese APT exploitation of utilities infrastructure.¹
- Apache Tomcat Hardening: Block all 400+ identified malicious IP addresses from coordinated botnet campaigns and implement multi-factor authentication on exposed Tomcat Manager interfaces—this level of coordination typically precedes major ransomware deployment.⁵
- Enhanced Monitoring Deployment: Implement behavioral analytics for zero-day exploitation indicators, particularly privilege escalation and lateral movement patterns, given documented 4-hour domain compromise timelines.³,⁶
Short-Term Actions (1-7 Days)
- Comprehensive Vulnerability Assessment: Conduct organization-wide scans for all CISA Known Exploited Vulnerabilities catalog entries added in June 2025, prioritizing internet-facing systems and critical infrastructure components.²
- Qualcomm Device Inventory: Identify and assess systems containing Qualcomm chipsets affected by actively exploited CVE-2025-21479, CVE-2025-21480, and CVE-2025-27038—patches remain unavailable requiring compensating controls.¹¹
- Backup System Validation: Verify backup integrity and test recovery procedures given 34% shift to data-only extortion attacks—traditional backup strategies are insufficient against current threat actor capabilities.⁷
- Third-Party Risk Assessment: Evaluate vendor security postures following supply chain targeting by Chinese threat actors and coordinated ransomware operations against managed service providers.⁸
References
- Cisco Talos Intelligence. (2025, June). UAT-6382 exploits Cityworks zero-day vulnerability to deliver malware. https://blog.talosintelligence.com/uat-6382-exploits-cityworks-vulnerability/
- Cybersecurity and Infrastructure Security Agency. (2025, June 5). CISA Adds One Known Exploited Vulnerability to Catalog. https://www.cisa.gov/news-events/alerts/2025/06/05/cisa-adds-one-known-exploited-vulnerability-catalog
- CrowdStrike. (2025, June 10). June 2025 Patch Tuesday: One Zero-Day and Nine Critical Vulnerabilities Among 66 CVEs. https://www.crowdstrike.com/en-us/blog/patch-tuesday-analysis-june-2025/
- Cybersecurity and Infrastructure Security Agency. (2025, June 4). Updated Guidance on Play Ransomware. https://www.cisa.gov/news-events/alerts/2025/06/04/updated-guidance-play-ransomware
- GBHackers On Security. (2025, June 12). Hackers Launch Coordinated Attack on Apache Tomcat Manager from 400 Unique IPs. https://gbhackers.com/launch-coordinated-attack/
- VulnCheck. (2025). 2025 Q1 Trends in Vulnerability Exploitation. https://vulncheck.com/blog/exploitation-trends-q1-2025
- Spin.AI. (2025, May). Ransomware Tracker 2025: Latest Ransomware Attacks and Payment Trends. https://spin.ai/blog/ransomware-tracker-2025
- SentinelOne Labs. (2025, June). Follow the Smoke | China-nexus Threat Actors Hammer At the Doors of Top Tier Targets. https://www.sentinelone.com/labs/follow-the-smoke-china-nexus-threat-actors-hammer-at-the-doors-of-top-tier-targets/
- Center for Internet Security. (2025, June 12). Top 10 Malware Q1 2025. https://www.cisecurity.org/insights/blog/top-10-malware-q1-2025
- CISA. (2025, June 12). CISA Releases Ten Industrial Control Systems Advisories. https://www.cisa.gov/news-events/alerts/2025/06/12/cisa-releases-ten-industrial-control-systems-advisories
- Google Threat Analysis Group. (2025, June 10). Qualcomm Zero-Day Vulnerabilities Under Active Exploitation. https://blog.google/threat-analysis-group/


