Stay up to date the most pressing cyber threats, emerging trends and what they mean for enterprise security, critical infrastructure and global risk.
TLP: CLEAR
Executive Summary: The current threat landscape shows active exploitation of a high-severity Chrome zero-day discovered by Google's Threat Analysis Group,, with CISA adding CVE-2025-5419 to the Known Exploited Vulnerabilities (KEV) catalog as of June 6, 2025. Google issued emergency out-of-band patches for Chrome versions 137.0.7151.68/.69, affecting all Chromium-based browsers including Microsoft Edge, Brave, Opera, and Vivaldi., Simultaneously, CISA released updated guidance on Play ransomware, confirming 900 entities compromised as of May 2025, while releasing seven new ICS advisories on June 5, 2025.
Assessment: Current threats demonstrate coordinated targeting of widely-deployed technologies (Chrome browsers) and critical infrastructure (ICS systems) with confirmed active exploitation. The rapid KEV additions and emergency patching cycles indicate accelerated threat actor operations requiring immediate defensive responses.
Recommendations: Organizations should immediately update all Chrome and Chromium-based browsers while implementing enhanced monitoring for V8 JavaScript engine exploitation attempts. The confluence of actively exploited browser vulnerabilities and persistent ransomware campaigns targeting diverse sectors demands elevated security postures across all networks.
Top Stories
1. Google Chrome Zero-Day CVE-2025-5419
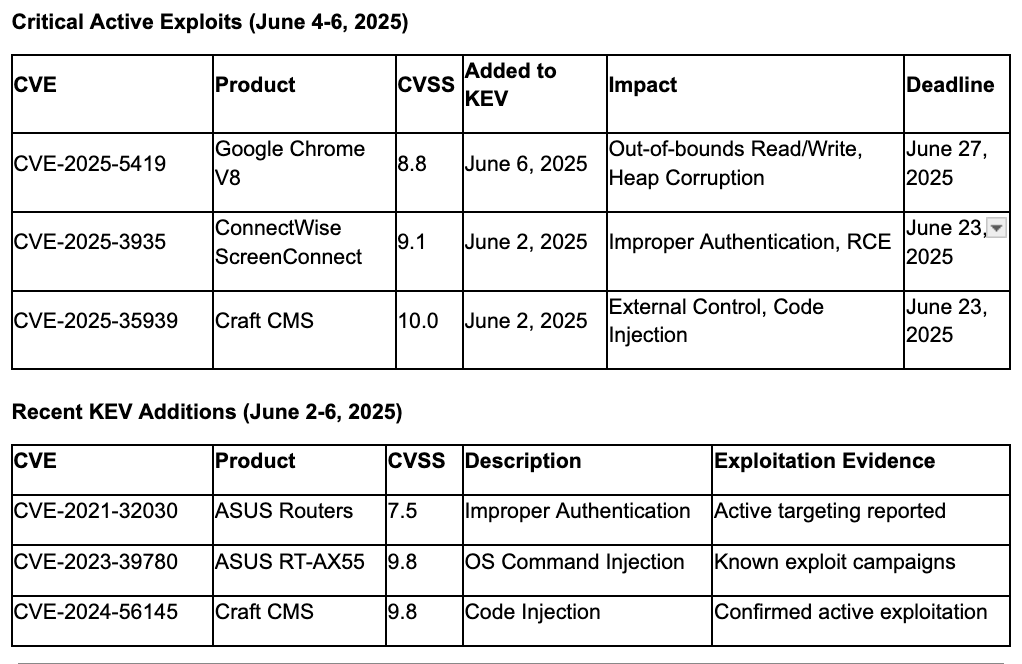
Under Active ExploitationGoogle released emergency patches for Chrome on June 3, 2025, addressing CVE-2025-5419, a high-severity out-of-bounds read and write vulnerability in the V8 JavaScript engine that allows remoteattackers to trigger heap corruption via crafted HTML pages.,, Google's Threat Analysis Group discovered the flaw on May 27, with Google pushing configuration changes the following day and formal patches this week., CISA added the vulnerability to its KEV catalog on June 6, 2025, requiring federal agencies to patch immediately. This marks Google's third actively exploited Chrome zero-day in 2025, following CVE-2025-2783 and CVE-2025-4664. , Organizations must immediately update to Chrome version 137.0.7151.68/.69 for Windows/macOS and 137.0.7151.68 for Linux, with users of Chromium-based browsers (Microsoft Edge, Brave, Opera, Vivaldi) requiring vendor-specific patches.
2. CISA Updates Play Ransomware Guidance Covering 900 Compromised Entities
CISA released updated guidance on June 4, 2025, for Play ransomware (Playcrypt), confirming the FBI has identified approximately 900 entities exploited by these actors as of May 2025. Since June 2022, Play has targeted diverse businesses and critical infrastructure across North America, South America, and Europe, becoming one of the most active ransomware groups in 2024. The updated guidance emphasizes keeping all operating systems, software, and firmware updated as primary defense measures. This represents a significant increase in confirmed victims, indicating accelerated operations by the Play group. Organizations must implement comprehensive backup strategies, network segmentation, and enhanced monitoring for Play-specific tactics, techniques, and procedures while ensuring all systems receive timely security updates.
3. CISA Releases Multiple Critical Infrastructure Advisories
CISA released seven Industrial Control Systems advisories on June 5, 2025, covering CyberData 011209 SIP Emergency Intercom and Hitachi Energy systems, providing timely information about current security issues, vulnerabilities, and exploits surrounding ICS. Additionally, CISA released three ICS advisories on June 3, 2025, affecting Schneider Electric Wiser Home Automation, EcoStruxure Power Build Rapsody, and Mitsubishi Electric MELSEC iQ-F Series. These releases indicate ongoing targeting of critical infrastructure components by threat actors. CISA also added five new vulnerabilities to the KEV catalog on June 2, 2025, including CVE-2025-3935 (ConnectWise ScreenConnect) and CVE-2025-35939 (Craft CMS), both enabling remote code execution. Critical infrastructure operators must immediately review these advisories and implement recommended mitigations while prioritizing patches for newly identified KEV vulnerabilities.
Top Vulnerabilities
Recommendations
Immediate Actions (0-24 hours)
- Chrome Emergency Updates: Deploy Chrome 137.0.7151.68/.69 (Windows/macOS) and 137.0.7151.68 (Linux) across all systems immediately to address CVE-2025-5419
- Chromium-Based Browser Patches: Update Microsoft Edge, Brave, Opera, and Vivaldi when vendor patches become available for V8 engine vulnerability
- ConnectWise ScreenConnect Isolation: Immediately isolate and patch CVE-2025-3935 in ScreenConnect servers, implement network segmentation to prevent lateral movement
- Play Ransomware Defense Review: Audit backup integrity and network segmentation following CISA's updated guidance on 900 compromised entities
Short-term Actions (1-7 days)
- V8 Engine Monitoring: Implement behavioral analytics to detect JavaScript heap corruption exploitation attempts across all web browsers
- ICS Security Assessment: Review CISA's June 3 and June 5 ICS advisories for Schneider Electric, Hitachi Energy, CyberData, and Mitsubishi Electric products
- Browser Security Hardening: Deploy enterprise browser management policies to ensure automatic updates and restrict potentially malicious JavaScript execution
- Ransomware Preparedness Drills: Conduct tabletop exercises specifically targeting Play ransomware scenarios based on CISA's updated 900-entity findings
- Help Net Security. Google fixes Chrome zero-day with in-the-wild exploit (CVE-2025-5419). June 4, 2025. Available at: https://www.helpnetsecurity.com/2025/06/04/google-fixes-chrome-zero-day-with-in-the-wild-exploit-cve-2025-5419/
- The Hacker News. New Chrome Zero-Day Actively Exploited; Google Issues Emergency Out-of-Band Patch. June 3, 2025. Available at: https://thehackernews.com/2025/06/new-chrome-zero-day-actively-exploited.html
- Help Net Security. Google fixes Chrome zero-day with in-the-wild exploit (CVE-2025-5419). June 4, 2025. Available at: https://www.helpnetsecurity.com/2025/06/04/google-fixes-chrome-zero-day-with-in-the-wild-exploit-cve-2025-5419/
- The Hacker News. New Chrome Zero-Day Actively Exploited; Google Issues Emergency Out-of-Band Patch. June 3, 2025. Available at: https://thehackernews.com/2025/06/new-chrome-zero-day-actively-exploited.html
- The Register. Google pushes emergency fix for high-severity Chrome 0-day. June 3, 2025. Available at: https://www.theregister.com/2025/06/03/google_chrome_zero_day_emergency_fix/
- Cybersecurity and Infrastructure Security Agency. Updated Guidance on Play Ransomware. June 4, 2025. Available at: https://www.cisa.gov/news-events/alerts/2025/06/04/updated-guidance-play-ransomware
- Cybersecurity and Infrastructure Security Agency. CISA Releases Seven Industrial Control Systems Advisories. June 5, 2025. Available at: https://www.cisa.gov/news-events/alerts/2025/06/05/cisa-releases-seven-industrial-control-systems-advisories
- Help Net Security. Google fixes Chrome zero-day with in-the-wild exploit (CVE-2025-5419). June 4, 2025. Available at: https://www.helpnetsecurity.com/2025/06/04/google-fixes-chrome-zero-day-with-in-the-wild-exploit-cve-2025-5419/
- The Hacker News. New Chrome Zero-Day Actively Exploited; Google Issues Emergency Out-of-Band Patch. June 3, 2025. Available at: https://thehackernews.com/2025/06/new-chrome-zero-day-actively-exploited.html
- BleepingComputer. Google patches new Chrome zero-day bug exploited in attacks. June 3, 2025. Available at: https://www.bleepingcomputer.com/news/security/google-patches-new-chrome-zero-day-bug-exploited-in-attacks/
- The Register. Google pushes emergency fix for high-severity Chrome 0-day. June 3, 2025. Available at: https://www.theregister.com/2025/06/03/google_chrome_zero_day_emergency_fix/
- BleepingComputer. Google patches new Chrome zero-day bug exploited in attacks. June 3, 2025. Available at: https://www.bleepingcomputer.com/news/security/google-patches-new-chrome-zero-day-bug-exploited-in-attacks/
- The Register. Google pushes emergency fix for high-severity Chrome 0-day. June 3, 2025. Available at: https://www.theregister.com/2025/06/03/google_chrome_zero_day_emergency_fix/
- BleepingComputer. Google patches new Chrome zero-day bug exploited in attacks. June 3, 2025. Available at: https://www.bleepingcomputer.com/news/security/google-patches-new-chrome-zero-day-bug-exploited-in-attacks/
- The Hacker News. New Chrome Zero-Day Actively Exploited; Google Issues Emergency Out-of-Band Patch. June 3, 2025. Available at: https://thehackernews.com/2025/06/new-chrome-zero-day-actively-exploited.html
- Cyber Security Agency of Singapore. Active Exploitation of Zero-Day Vulnerability in Google Chrome. June 2025. Available at: https://www.csa.gov.sg/alerts-and-advisories/alerts/al-2025-053
- Cybersecurity and Infrastructure Security Agency. Updated Guidance on Play Ransomware. June 4, 2025. Available at: https://www.cisa.gov/news-events/alerts/2025/06/04/updated-guidance-play-ransomware
- Cybersecurity and Infrastructure Security Agency. Updated Guidance on Play Ransomware. June 4, 2025. Available at: https://www.cisa.gov/news-events/alerts/2025/06/04/updated-guidance-play-ransomware
- Cybersecurity and Infrastructure Security Agency. Updated Guidance on Play Ransomware. June 4, 2025. Available at: https://www.cisa.gov/news-events/alerts/2025/06/04/updated-guidance-play-ransomware
- Cybersecurity and Infrastructure Security Agency. CISA Releases Seven Industrial Control Systems Advisories. June 5, 2025. Available at: https://www.cisa.gov/news-events/alerts/2025/06/05/cisa-releases-seven-industrial-control-systems-advisories
- Cybersecurity and Infrastructure Security Agency. CISA Releases Seven Industrial Control Systems Advisories. June 5, 2025. Available at: https://www.cisa.gov/news-events/alerts/2025/06/05/cisa-releases-seven-industrial-control-systems-advisories
- Cybersecurity and Infrastructure Security Agency. CISA Adds Five Known Exploited Vulnerabilities toCatalog. June 2, 2025. Available at: https://www.cisa.gov/news-events/alerts/2025/06/02/cisa-adds-five-known-exploited-vulnerabilities-catalog


