Deploy and scale seamlessly across the globe, and centrally manage activity regardless of computer, network or location
Run all web code in a secure, high-trust environment fully isolated on all sides — from malicious web content to unmanaged devices and networks
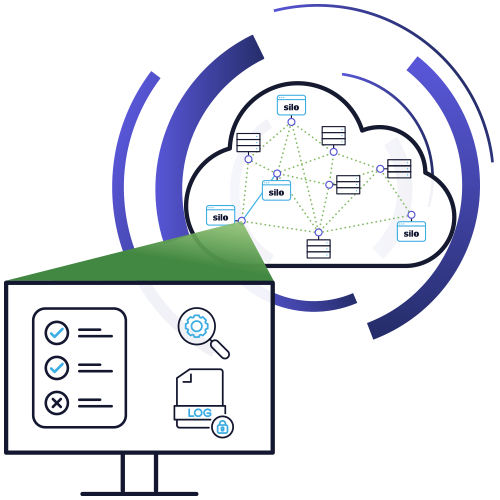
Govern all web activity with rich, admin-defined policies and give admins complete visibility, audit and oversight through a comprehensive logging framework